cisco 200-201 practice test
understanding cisco cybersecurity operations fundamentals (cbrops)
Last exam update: Apr 14 ,2025
Question 1

Refer to the exhibit. Which type of attack is being executed?
- A. cross-site request forgery
- B. command injection
- C. SQL injection
- D. cross-site scripting
Answer:
c
Reference:
https://www.w3schools.com/sql/sql_injection.asp
Question 2
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
- A. Hypertext Transfer Protocol
- B. SSL Certificate
- C. Tunneling
- D. VPN
Answer:
b
Question 3
What is the difference between vulnerability and risk?
- A. A vulnerability represents a flaw in a security that can be exploited, and the risk is the potential damage it might cause.
- B. A risk is potential threat that adversaries use to infiltrate the network, and a vulnerability is an exploit.
- C. A risk is a potential threat that an exploit applies to, and a vulnerability represents the threat itself.
- D. A vulnerability is a sum of possible malicious entry points, and a risk represents the possibility of the unauthorized entry itself.
Answer:
a
Question 4
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
- A. application whitelisting/blacklisting
- B. network NGFW
- C. host-based IDS
- D. antivirus/antispyware software
Answer:
a
Question 5
Which two elements are used for profiling a network? (Choose two.)
- A. session duration
- B. total throughput
- C. running processes
- D. listening ports
- E. OS fingerprint
Answer:
de
Question 6
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
- A. queries Linux devices that have Microsoft Services for Linux installed
- B. deploys Windows Operating Systems in an automated fashion
- C. is an efficient tool for working with Active Directory
- D. has a Common Information Model, which describes installed hardware and software
Answer:
d
Question 7
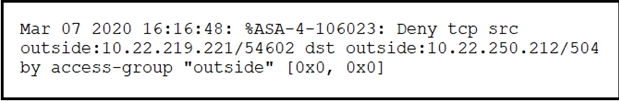
Refer to the exhibit. Which technology generates this log?
- A. NetFlow
- B. IDS
- C. web proxy
- D. firewall
Answer:
d
Question 8
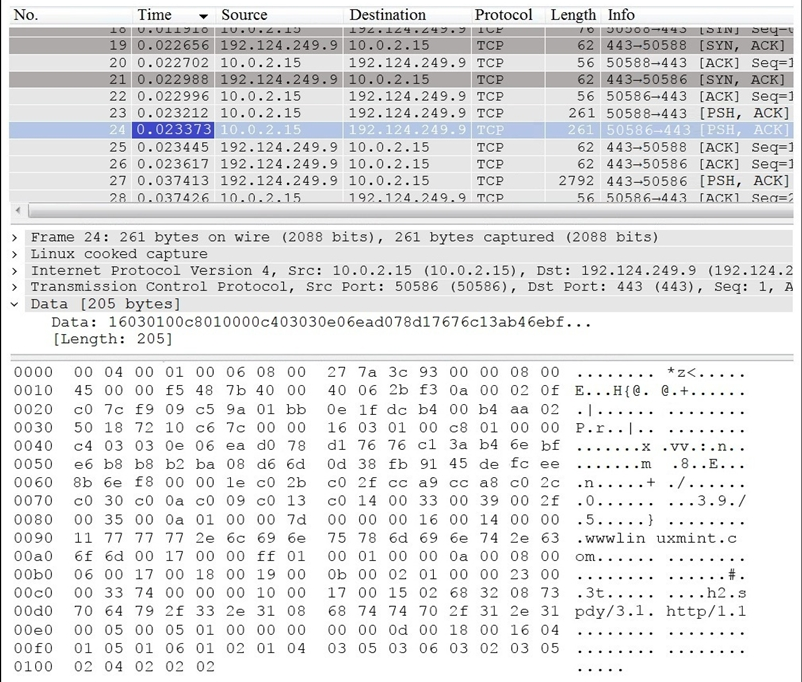
Refer to the exhibit. Which application protocol is in this PCAP file?
- A. SSH
- B. TCP
- C. TLS
- D. HTTP
Answer:
b
Question 9
What are two social engineering techniques? (Choose two.)
- A. privilege escalation
- B. DDoS attack
- C. phishing
- D. man-in-the-middle
- E. pharming
Answer:
ce
Question 10
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
- A. reconnaissance
- B. action on objectives
- C. installation
- D. exploitation
Answer:
c