cisco 300-635 practice test
automating cisco data center solutions (dcauto)
Last exam update: Apr 14 ,2025
Question 1
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)
- A. The REST API request contains a base64-encoded signature of the message content and headers.
- B. The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
- C. The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
- D. The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
- E. The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.
Answer:
ad
Question 2
Refer to the exhibit.
Which action does the execution of this ACI Cobra Python code perform?
- A. It prints all LLDP neighbor MAC and IP addresses.
- B. It prints all Cisco Discovery Protocol neighbor MAC and IP addresses.
- C. It prints all endpoint MAC and IP addresses.
- D. It prints all APIC MAC and IP addresses.
Answer:
c
Question 3
DRAG DROP A co-worker is using Cisco Intersight to determine the maximum available memory per server for their company's data center. Drag and drop the code to complete the Cisco Intersight API call that provides the desired results. Not all options are used.
Select and Place: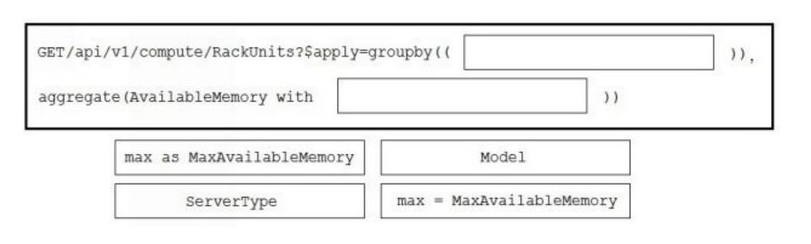
Answer:
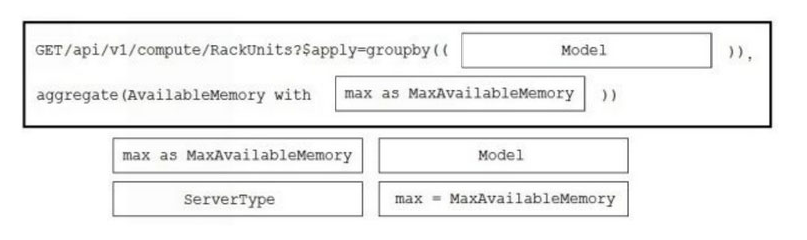
Question 4
When the Cisco bigmuddy-network-telemetry-collector from GitHub is used, which command displays only the message headers?
- A. --print
- B. --all
- C. --brief
- D. --print-all
Answer:
c
Question 5
Which NX-API request queries the MAC address table?
A.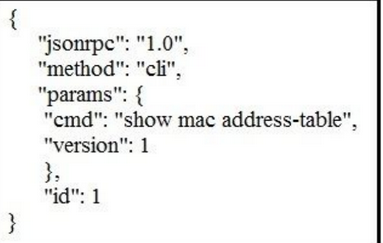
B.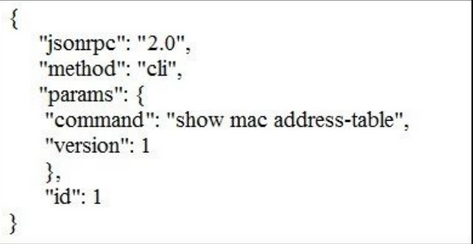
C.
D.
Answer:
d
Question 6

Which Python snippets create an application policy named OrderProcess that contains two application endpoint groups under Tenant SuperEats using direct calls to the ACI REST API? Assume that authentication and library imports are correct.
A.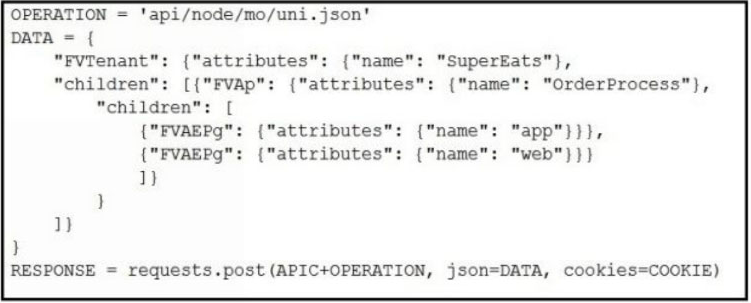
B.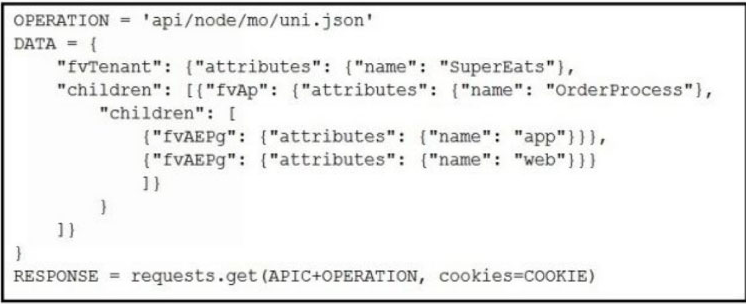
C.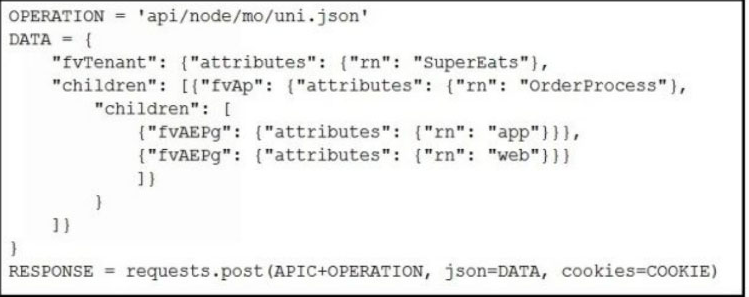
D.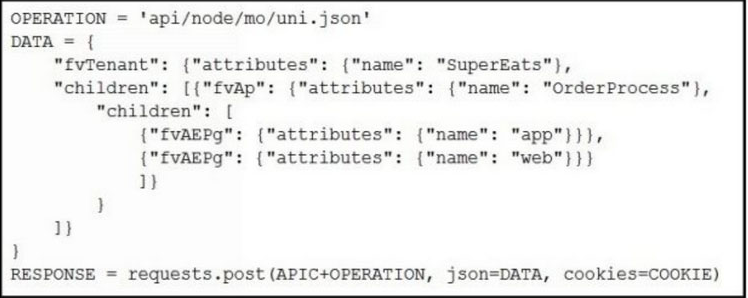
Answer:
d
Question 7
Refer to the exhibit.
Which two statements are true about this API GET request to the ACI APIC? (Choose two.)
- A. The API call creates a new 10G interface in the APIC.
- B. The API call reads information from a managed object.
- C. The API response is encoded in JSON.
- D. The API call reads information from an object class.
- E. The API response is encoded in XML.
Answer:
be
Question 8
Which two statements apply to authentication when using the Cisco Intersight API? (Choose two.)
- A. Each API Key can be assigned specific roles but not privileges.
- B. Secret Key is only available at API Key creation time.
- C. An API Key is composed of a Key ID and Secret Key.
- D. The user credentials for the cisco.com accounts are shared with the Cisco Intersight Web Service.
- E. An API Key is composed of a keyId and sessionCookie.
Answer:
bc
Question 9
During the process of starting a Python network telemetry collector, which command starts the Cisco bigmuddy-network-telemetry-collector from GitHub?
- A. model driven telemetry
-
B.
telemetry_receiver.py --ip-address
--port -
C.
telemetry_receiver.py --destination
--url - D. streaming telemetry
Answer:
b
Question 10
Which action allows Docker daemon persistence during switchover on the Cisco Nexus 9500 Series Switches running Cisco NX-OS?
- A. Change the Docker configuration to include the live restore option.
- B. Copy the dockerpart file manually to the standby supervisor after performing the switchover.
- C. Copy the dockerpart file manually to the standby supervisor before performing the switchover.
- D. The system takes automatic action.
Answer:
c