Question 1
DRAG DROP
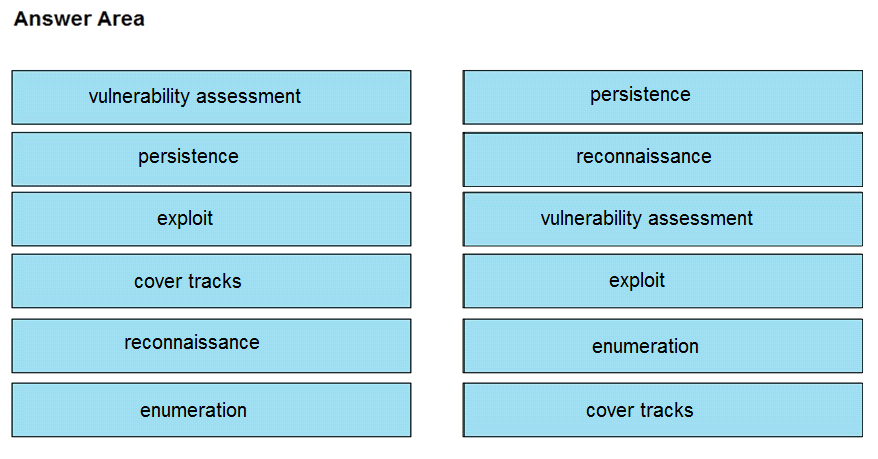
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity
that happens during the phases on the right.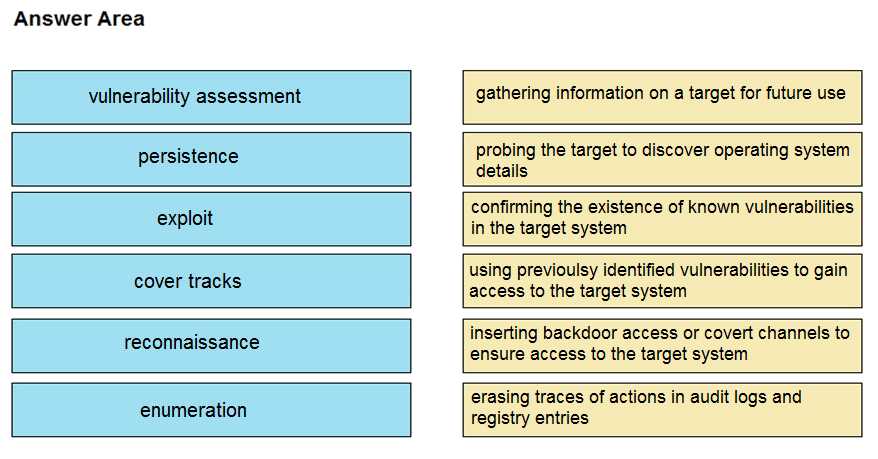
Answer:
Comments
Question 2
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and
availability?
- A. Perform a vulnerability assessment
- B. Conduct a data protection impact assessment
- C. Conduct penetration testing
- D. Perform awareness testing
Answer:
B
Reference:
https://apdcat.gencat.cat/web/.content/03-documentacio/
Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
Comments
Question 3
A payroll administrator noticed unexpected changes within a piece of software and reported the
incident to the incident response team. Which actions should be taken at this step in the incident
response workflow?
- A. Classify the criticality of the information, research the attacker’s motives, and identify missing patches
- B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
- C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
- D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Answer:
B
Comments
Question 4
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20
of its hosted applications. Based on the audit, which recommendation should an engineer make for
patching?
- A. Identify the business applications running on the assets
- B. Update software to patch third-party software
- C. Validate CSRF by executing exploits within Metasploit
- D. Fix applications according to the risk scores
Answer:
D
Comments
Question 5
An engineer is analyzing a possible compromise that happened a week ago when the company ?
(Choose two.)
- A. firewall
- B. Wireshark
- C. autopsy
- D. SHA512
- E. IPS
Answer:
AB
Comments
Question 6
A European-based advertisement company collects tracking information from partner websites and
stores it on a local server to provide tailored ads. Which standard must the company follow to
safeguard the resting data?
- A. HIPAA
- B. PCI-DSS
- C. Sarbanes-Oxley
- D. GDPR
Answer:
D
Reference:
https://www.thesslstore.com/blog/10-data-privacy-and-encryption-laws-every-business-
needs-to
- know/
Comments
Question 7
An organization had a breach due to a phishing attack. An engineer leads a team through the
recovery phase of the incident response process. Which action should be taken during this phase?
- A. Host a discovery meeting and define configuration and policy updates
- B. Update the IDS/IPS signatures and reimage the affected hosts
- C. Identify the systems that have been affected and tools used to detect the attack
- D. Identify the traffic with data capture using Wireshark and review email filters
Answer:
C
Comments
Question 8
An engineer is going through vulnerability triage with company management because of a recent
malware outbreak from which 21 affected assets need to be patched or remediated. Management
decides not to prioritize fixing the assets and accepts the vulnerabilities. What is the next step the
engineer should take?
- A. Investigate the vulnerability to prevent further spread
- B. Acknowledge the vulnerabilities and document the risk
- C. Apply vendor patches or available hot fixes
- D. Isolate the assets affected in a separate network
Answer:
D
Comments
Question 9
The incident response team receives information about the abnormal behavior of a host. A malicious
file is found being executed from an external USB flash drive. The team collects and documents all
the necessary evidence from the computing resource. What is the next step?
- A. Conduct a risk assessment of systems and applications
- B. Isolate the infected host from the rest of the subnet
- C. Install malware prevention software on the host
- D. Analyze network traffic on the host’s subnet
Answer:
B
Comments
Question 10
DRAG DROP
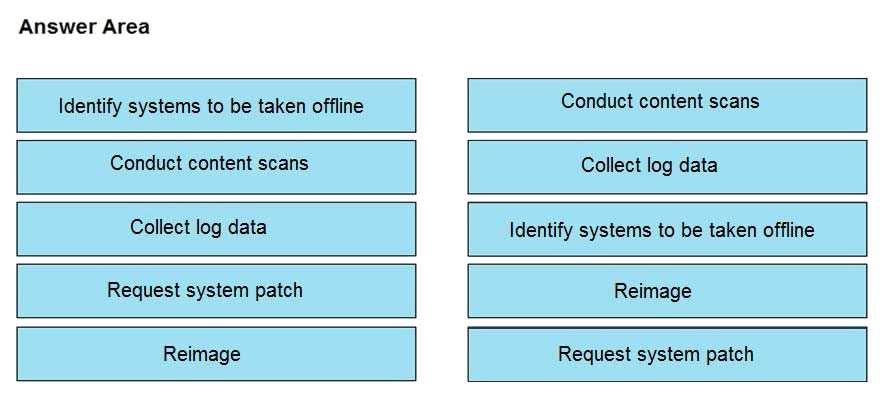
An engineer notices that unauthorized software was installed on the network and discovers that it
was installed by a dormant user account. The engineer suspects an escalation of privilege attack and
responds to the incident. Drag and drop the activities from the left into the order for the response on
the right.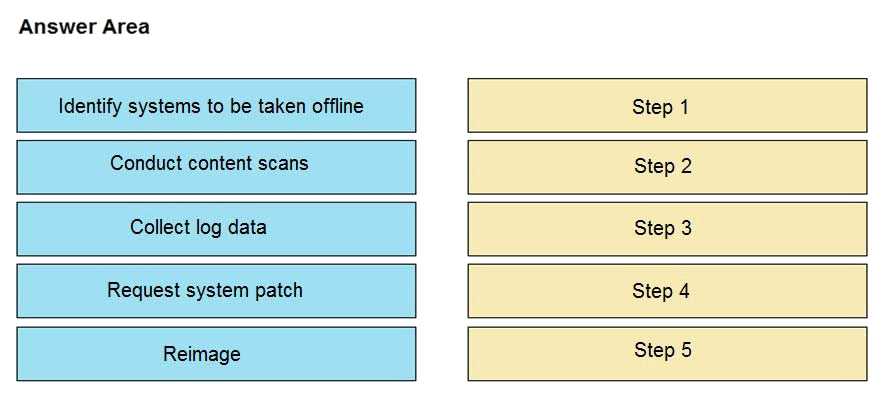
Answer:
Comments
Page 1 out of 13
Viewing questions 1-10 out of 139
page 2