cisco 350-701 practice test
implementing and operating cisco security core technologies
Last exam update: Apr 14 ,2025
Question 1
How does Cisco Advanced Phishing Protection protect users?
- A. It utilizes sensors that send messages securely.
- B. It uses machine learning and real-time behavior analytics.
- C. It validates the sender by using DKIM.
- D. It determines which identities are perceived by the sender.
Answer:
b
Question 2
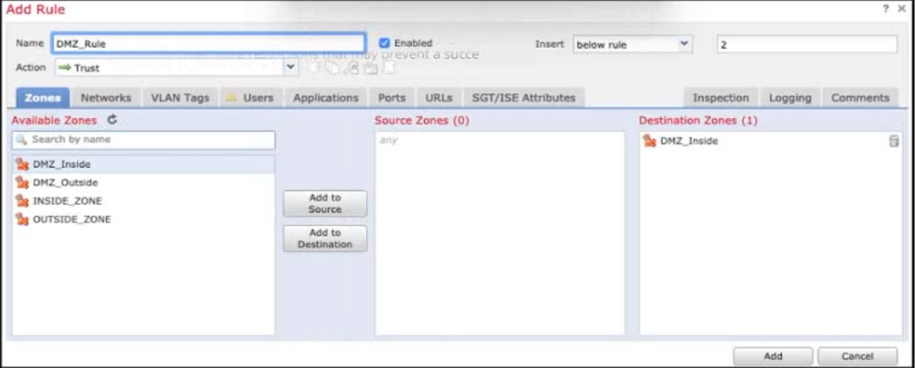
Refer to the exhibit. When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZ_inside zone once the configuration is deployed?
- A. No traffic will be allowed through to the DMZ_inside zone regardless of if its trusted or not.
- B. All traffic from any zone will be allowed to the DMZ_inside zone only after inspection.
- C. All traffic from any zone to the DMZ_inside zone will be permitted with no further inspection.
- D. No traffic will be allowed through to the DMZ_inside zone unless it's already trusted.
Answer:
c
Question 3

Refer to the exhibit. An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
- A. dot1x reauthentication
- B. cisp enable
- C. dot1x pae authenticator
- D. authentication open
Answer:
c
Question 4
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
- A. smurf
- B. distributed denial of service
- C. cross-site scripting
- D. rootkit exploit
Answer:
c
Question 5
Which compliance status is shown when a configured posture policy requirement is not met?
- A. authorized
- B. compliant
- C. unknown
- D. noncompliant
Answer:
d
Question 6

Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
- A. interesting traffic was not applied
- B. encryption algorithm mismatch
- C. authentication key mismatch
- D. hashing algorithm mismatch
Answer:
c
Question 7
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
- A. SDLC
- B. Lambda
- C. Contiv
- D. Docker
Answer:
d
Reference:
https://www.cisco.com/c/dam/global/es_es/pdfs/Cisco-cloudcenter-architecture-wp-c11-737224.pdf
Question 8
What is provided by the Secure Hash Algorithm in a VPN?
- A. authentication
- B. encryption
- C. integrity
- D. key exchange
Answer:
c
Question 9
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
- A. sFlow
- B. NetFlow
- C. mirror port
- D. VPC flow logs
Answer:
d
Question 10
DRAG DROP Drag and drop the deployment models from the left onto the corresponding explanations on the right.
Select and Place:
Answer:
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/ inline_sets_and_passive_interfaces_for_firepower_threat_defense.html#concept_835CD87FE5ED4CD9BAEE2118D588AC58