cisco 500-220 practice test
cisco meraki solutions specialist
Last exam update: Apr 14 ,2025
Question 1
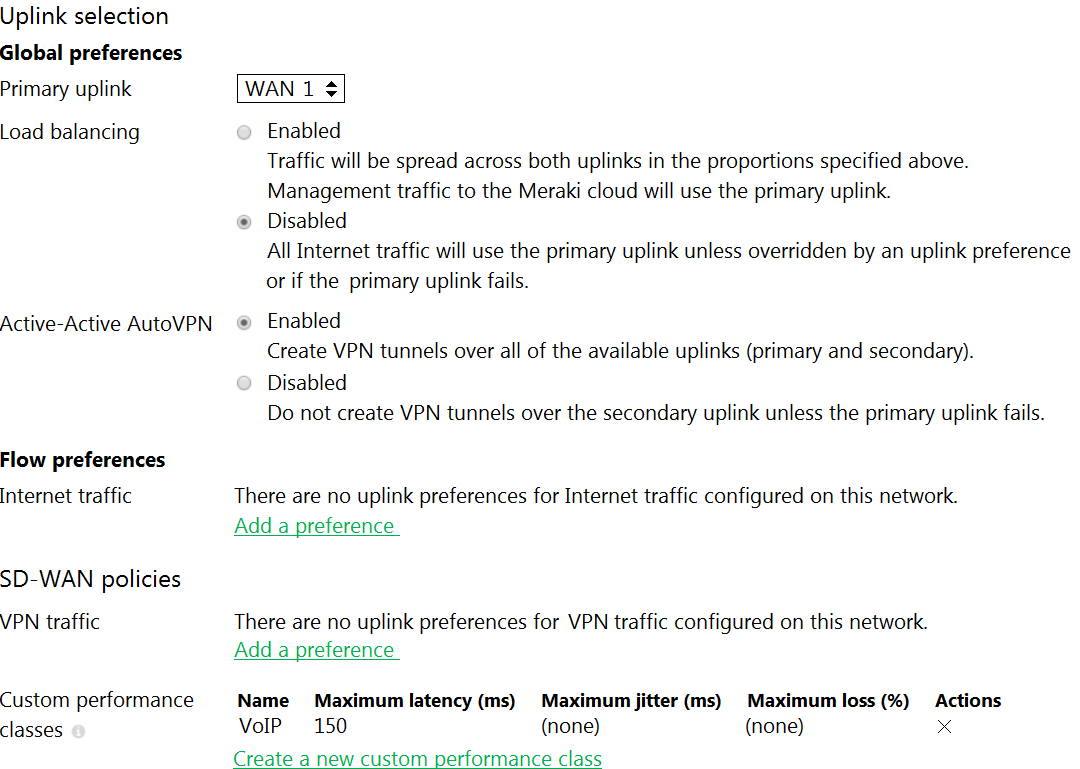
Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
- A. 1000-byte TCP probes every second, through VPN tunnels that are established over the primary WAN link.
- B. 100-byte UDP probes every second, through VPN tunnels that are established over every WAN link.
- C. 100-byte UDP probes every second, through VPN tunnels that are established over the primary WAN link.
- D. 1000-byte TCP probes every second, through VPN tunnels that are established over every WAN link.
Answer:
d
Question 2
DRAG DROP
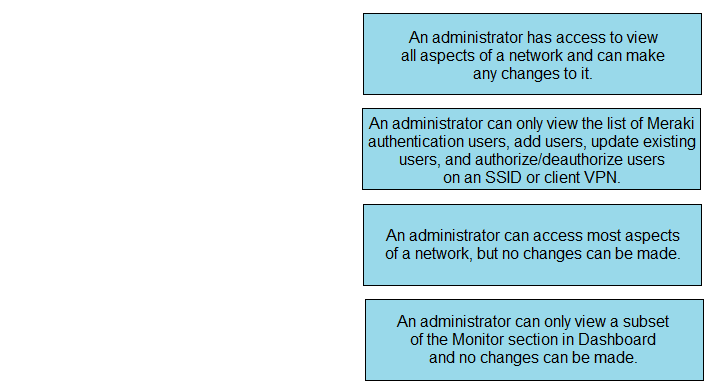
Drag and drop the descriptions from the left onto the permission types on the right.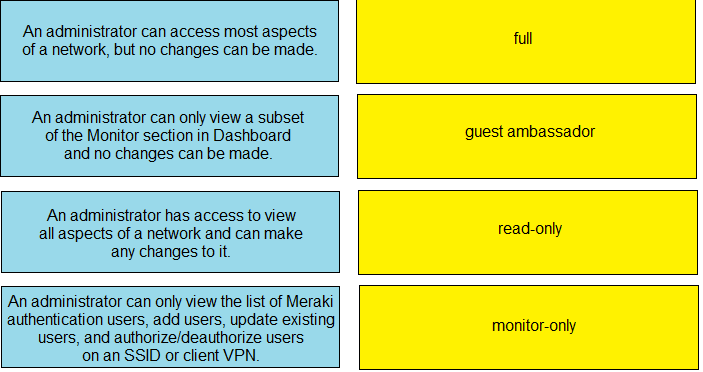
Answer:
Question 3
What are two methods of targeting and applying management profiles to System Manager clients? (Choose two.)
- A. by defining a range of serial numbers
- B. by defining the scope
- C. by using device tags
- D. by using Wi-Fi tags
- E. by using dynamic IP tags
Answer:
bc
Question 4
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
- A. highest VLAN ID that is configured and set to NO to use VPN
- B. lowest VLAN ID that is configured and set to YES to use VPN
- C. highest VLAN ID that is configured and set to YES to use VPN
- D. lowest VLAN ID configured and set to NO to use VPN
Answer:
c
Question 5
The WAN connection of a Cisco Meraki MX security appliance is congested, and the MX appliance is buffering the traffic from LAN ports going to the WAN ports. High, normal, and low priority queue buffers are all full. Which proportion of the normal traffic is forwarded compared to the other queues?
- A. 4/10 packets
- B. 2/10 packets
- C. 2/7 packets
- D. 5/15 packets
Answer:
c
Question 6
What happens to an unsupervised iOS device when the Meraki management profile is removed?
- A. The Meraki management profile is removed. All configuration profiles that Systems Manager pushed remain.
- B. The Meraki management profile is removed. All configuration profiles that Systems Manager pushed are also removed.
- C. The Meraki management profile is removed and then pushed automatically by Systems Manager.
- D. The Meraki management profile cannot be removed.
Answer:
b
Question 7
A Cisco Meraki MX security appliance is trying to route a packet to the destination IP address of 172.18.24.12. Which routes contained in its routing table does it select?
- A. Auto VPN route 172.18.0.0/16
- B. non-Meraki VPN route 172.18.24.0/24
- C. directly connected 172.18.16.0/20
- D. static route 172.16.0.0/12
Answer:
b
Question 8
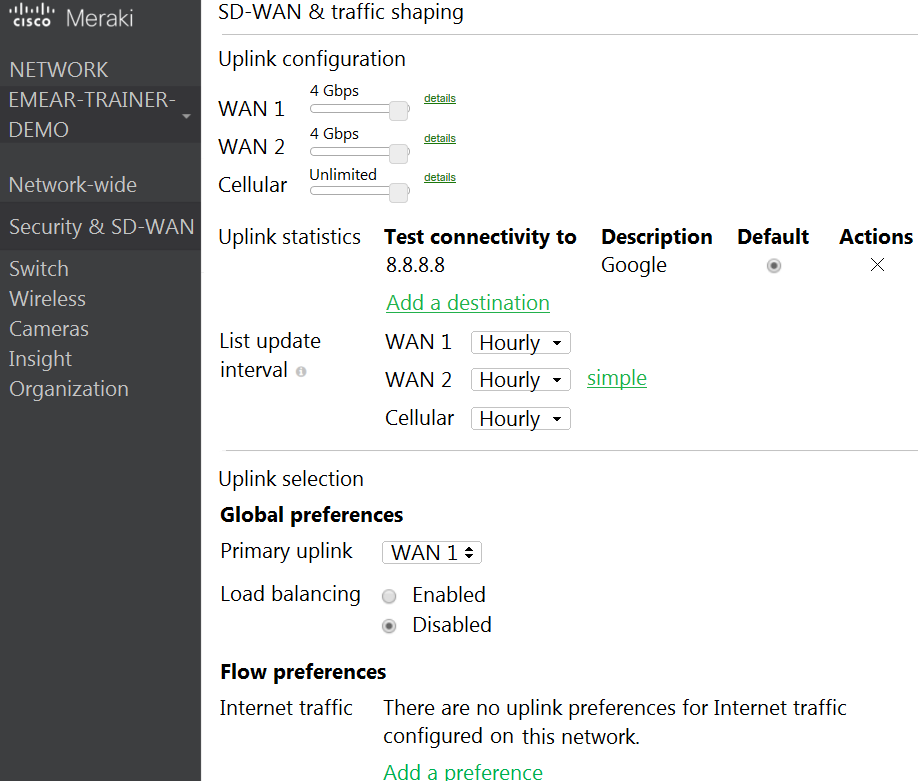
Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
- A. Change the primary uplink to "none".
- B. Add an internet traffic preference that defines the load-balancing ratio as 4:1.
- C. Enable load balancing.
- D. Set the speed of the cellular uplink to zero.
- E. Change the assigned speeds of WAN 1 and WAN 2 so that the ratio is 4:1.
Answer:
bc
Question 9
What occurs when a configuration change is made to an MX network that is bound to a configuration template?
- A. The configuration change in the bound network is combined with the template configuration inside the template.
- B. The more restrictive configuration is preferred.
- C. The configuration change in the bound network overrides the template configuration.
- D. The template configuration overrides the configuration change in the bound network.
Answer:
a
Question 10
Which Meraki Dashboard menu section is accessed to enable Sentry enrollment on an SSID?
- A. Wireless > Configure > Access Control
- B. Wireless > Configure > Splash page
- C. Wireless > Configure > Firewall & Traffic Shaping
- D. Wireless > Configure > SSIDs
Answer:
a