comptia cs0-003 practice test
CompTIA CySA+ (CS0-003)
Last exam update: Apr 17 ,2025
Question 1
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host. Which of the following patterns can the security analyst use to search the web server logs for evidence of exploitation of that particular vulnerability?
- A. /etc/shadow
- B. curl localhost
- C. ; printenv
- D. cat /proc/self/
Answer:
a
Question 2
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
- A. Business continuity plan
- B. Vulnerability management plan
- C. Disaster recovery plan
- D. Asset management plan
Answer:
c
Question 3
Which of the following best describes the process of requiring remediation of a known threat within a given time frame?
- A. SLA
- B. MOU
- C. Best-effort patching
- D. Organizational governance
Answer:
a
Question 4
An organization's email account was compromised by a bad actor. Given the following information: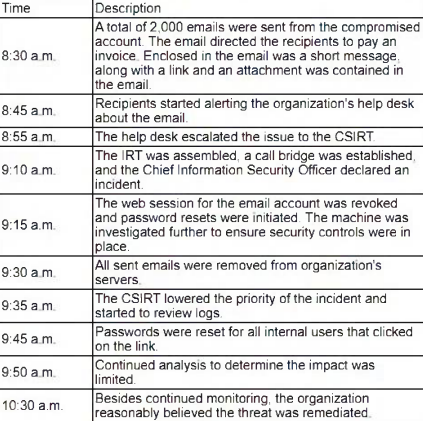
Which of the following is the length of time the team took to detect the threat?
- A. Data masking
- B. Hashing
- C. Watermarking
- D. Encoding
Answer:
c
Question 5
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
- A. False positive
- B. True negative
- C. False negative
- D. True positive
Answer:
c
Question 6
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
- A. Increasing training and awareness for all staff
- B. Ensuring that malicious websites cannot be visited
- C. Blocking all scripts downloaded from the internet
- D. Disabling all staff members ability to run downloaded applications
Answer:
a
Question 7
A company that has a geographically diverse workforce and dynamic IPs wants to implement a vulnerability scanning method with reduced network traffic. Which of the following would best meet this requirement?
- A. External
- B. Agent-based
- C. Non-credentialed
- D. Credentialed
Answer:
b
Question 8
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers. The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_user&role=administrator
Which of the following controls would work best to mitigate the attack represented by this snippet?
- A. Limit user creation to administrators only.
- B. Limit layout creation to administrators only.
- C. Set the directory trx_addons to read only for all users.
- D. Set the directory V2 to read only for all users.
Answer:
a
Question 9
Which of the following would help to minimize human engagement and aid in process improvement in security operations?
- A. OSSTMM
- B. SIEM
- C. SOAR
- D. OWASP
Answer:
c
Question 10
Security analysts review logs on multiple servers on a daily basis. Which of the following implementations will give the best central visibility into the events occurring throughout the corporate environment without logging in to the servers individually?
- A. Deploy a database to aggregate the logging
- B. Configure the servers to forward logs to a SIEM
- C. Share the log directory on each server to allow local access.
- D. Automate the emailing of logs to the analysts.
Answer:
b