Question 1
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified.
Which of the following character combinations should be used on the first line of the script to accomplish this goal?
- A. <#
- B. <$
- C. ##
- D. #$
- E. #!
Answer:
e
Reference:
https://linuxconfig.org/bash-scripting-tutorial-for-beginners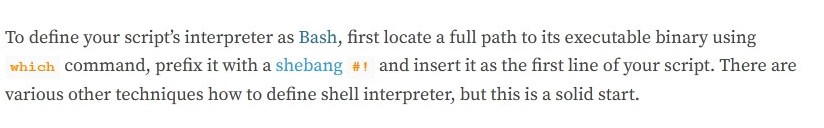
Comments
Question 2
A new client hired a penetration-testing company for a month-long contract for various security assessments against the client's new service. The client is expecting to make the new service publicly available shortly after the assessment is complete and is planning to fix any findings, except for critical issues, after the service is made public. The client wants a simple report structure and does not want to receive daily findings.
Which of the following is most important for the penetration tester to define FIRST?
- A. Establish the format required by the client.
- B. Establish the threshold of risk to escalate to the client immediately.
- C. Establish the method of potential false positives.
- D. Establish the preferred day of the week for reporting.
Answer:
a
Comments
Question 3
A penetration tester opened a reverse shell on a Linux web server and successfully escalated privileges to root. During the engagement, the tester noticed that another user logged in frequently as root to perform work tasks. To avoid disrupting this users work, which of the following is the BEST option for the penetration tester to maintain root-level persistence on this server during the test?
- A. Add a web shell to the root of the website.
- B. Upgrade the reverse shell to a true TTY terminal.
- C. Add a new user with ID 0 to the /etc/passwd file.
- D. Change the password of the root user and revert after the test.
Answer:
c
Comments
Question 4
DRAG DROP During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
Answer:
None

Comments
Question 5
Which of the following situations would require a penetration tester to notify the emergency contact for the engagement?
- A. The team exploits a critical server within the organization.
- B. The team exfiltrates PII or credit card data from the organization.
- C. The team loses access to the network remotely.
- D. The team discovers another actor on a system on the network.
Answer:
d
Comments
Question 6
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
- A. /var/log/messages
- B. /var/log/last_user
- C. /var/log/user_log
- D. /var/log/lastlog
Answer:
d
Comments
Question 7
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP.
Which of the following steps should the tester take NEXT?
- A. Send deauthentication frames to the stations.
- B. Perform jamming on all 2.4GHz and 5GHz channels.
- C. Set the malicious AP to broadcast within dynamic frequency selection channels.
- D. Modify the malicious AP configuration to not use a preshared key.
Answer:
c
Comments
Question 8
A penetration-testing team needs to test the security of electronic records in a company's office. Per the terms of engagement, the penetration test is to be conducted after hours and should not include circumventing the alarm or performing destructive entry. During outside reconnaissance, the team sees an open door from an adjoining building. Which of the following would be allowed under the terms of the engagement?
- A. Prying the lock open on the records room
- B. Climbing in an open window of the adjoining building
- C. Presenting a false employee ID to the night guard
- D. Obstructing the motion sensors in the hallway of the records room
Answer:
b
Comments
Question 9
Appending string values onto another string is called:
- A. compilation
- B. connection
- C. concatenation
- D. conjunction
Answer:
c
Comments
Question 10
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format:
- A. Create a custom password dictionary as preparation for password spray testing.
- B. Recommend using a password manager/vault instead of text files to store passwords securely.
- C. Recommend configuring password complexity rules in all the systems and applications.
- D. Create a TPM-backed sealed storage location within which the unprotected file repository can be reported.
Answer:
b
Comments
Page 1 out of 25
Viewing questions 1-10 out of 255
page 2