Question 1
The marketing department at a retail company wants to publish an internal website to the internet so it is reachable by a limited number of specific, external service providers in a secure manner. Which of the following configurations would be BEST to fulfil this requirement?
- A. NAC
- B. ACL
- C. WAF
- D. NAT
Answer:
b
Comments
Question 2
A Chief Information Security Officer (CISO) is concerned about the organization's ability to continue business operations in the event of a prolonged DDoS attack on its local datacenter that consumes database resources. Which of the following will the CISO MOST likely recommend to mitigate this risk?
- A. Upgrade the bandwidth available into the datacenter.
- B. Implement a hot-site failover location.
- C. Switch to a complete SaaS offering to customers.
- D. Implement a challenge response test on all end-user queries.
Answer:
b
Comments
Question 3
While troubleshooting service disruption on a mission-critical server, a technician discovered the user account that was configured to run automated processes was disabled because the user s password failed to meet password complexity requirements. Which of the following would be the best solution to securely prevent future issues?
- A. Using an administrator account to run the processes and disabling the account when it is not in use
- B. Implementing a shared account the team can use to run automated processes
- C. Configuring a service account to run the processes
- D. Removing the password complexity requirements for the user account
Answer:
c
Comments
Question 4
Which of the following would provide guidelines on how to label new network devices as part of the initial configuration?
- A. IP schema
- B. Application baseline configuration
- C. Standard naming convention policy
- D. Wireless LAN and network perimeter diagram
Answer:
c
Comments
Question 5
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs, the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
- A. Segmentation
- B. Firewall whitelisting
- C. Containment
- D. Isolation
Answer:
b
Comments
Question 6
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
- A. Document the collection and require a sign-off when possession changes.
- B. Lock the device in a safe or other secure location to prevent theft or alteration.
- C. Place the device in a Faraday cage to prevent corruption of the data.
- D. Record the collection in a blockchain-protected public ledger.
Answer:
a
Comments
Question 7
Several users have opened tickets with the help desk. The help desk has reassigned the tickets to a security analyst for further review. The security analyst reviews the following metrics: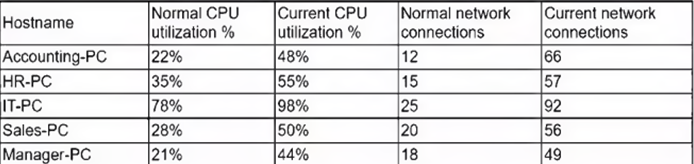
Which of the following is most likely the result of the security analyst's review?
- A. The ISP is dropping outbound connections.
- B. The user of the Sales-PC fell for a phishing attack
- C. Corporate PCs have been turned into a botnet.
- D. An on-path attack is taking place between PCs and the router.
Answer:
c
Comments
Question 8
Which of the following algorithms has the SMALLEST key size?
- A. DES
- B. Twofish
- C. RSA
- D. AES
Answer:
a
Comments
Question 9
Recent changes to a company's BYOD policy require all personal mobile devices to use a two-factor authentication method that is not something you know or have. Which of the following will meet this requirement?
- A. Facial recognition
- B. Six-digit PIN
- C. PKI certificate
- D. Smart card
Answer:
a
Comments
Question 10
In the middle of a cyberattack, a security engineer removes the infected devices from the network and locks down all compromised accounts. In which of the following incident response phases is the security engineer currently operating?
- A. Identification
- B. Preparation
- C. Lessons learned
- D. Eradication
- E. Recovery
- F. Containment
Answer:
f
Comments
Page 1 out of 71
Viewing questions 1-10 out of 711
page 2