CyberArk cau201 practice test
Defender Exam
Last exam update: Mar 26 ,2025
Question 1
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use
to set the full or relative path of the SSH private key file that will be attached to the account?
- A. KeyPath
- B. KeyFile
- C. ObjectName
- D. Address
Answer:
B
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/10.10/en/Content/PASIMP/Adding-Accounts-with-SSH-Keys-using-the-
AccountUploader-Utility-Appendix.htm
Question 2
In PVWA, you are attempting to play a recording made of a session by user jsmith, but there is no
option to Fast Forward within the video. It plays and only allows you to skip between commands
instead. You are also unable to download the video.
What could be the cause?
- A. Recording is of a PSM for SSH session.
- B. The browser you are using is out of date and needs an update to be supported.
- C. You do not have the “View Audit” permission on the safe where the account is stored.
- D. You need to update the recorder settings in the platform to enable screen capture every 10000ms or less.
Answer:
B
Explanation:
Reference:
https://cyberark-customers.force.com/s/article/00004935
Question 3
When onboarding multiple accounts from the Pending Accounts list, which associated setting must
be the same across the selected accounts?
- A. Platform
- B. Connection Component
- C. CPM
- D. Vault
Answer:
A
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Onboarding-Accounts-and-SSH-
Keys.htm?Highlight=safe%20does%20not%20support%20properties
Question 4
Your organization has a requirement to allow users to check out passwords and connect to targets
with the same account through the PSM.
What needs to be configured in the Master policy to ensure this will happen?
- A. Enforce check-in/check-out exclusive access = active; Require privileged session monitoring and isolation = active
- B. Enforce check-in/check-out exclusive access = inactive; Require privileged session monitoring and isolation = inactive
- C. Enforce check-in/check-out exclusive access = inactive; Record and save session activity = active
- D. Enforce check-in/check-out exclusive access = active; Record and save session activity = inactive
Answer:
C
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PrivCloud/Latest/en/Content/Privilege%20Cloud/privCloud-master-policy-
rules.htm
Question 5
To manage automated onboarding rules, a CyberArk user must be a member of which group?
- A. Vault Admins
- B. CPM User
- C. Auditors
- D. Administrators
Answer:
A
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/11.2/en/Content/PASIMP/automatic_onboarding_rules.htm#:~:text=To%20ma
nage%20onboarding%20rules%2C%20users,to%20the%20Vault%20admins%20group
Question 6
Which permissions are needed for the Active Directory user required by the Windows Discovery
process?
- A. Domain Admin
- B. LDAP Admin
- C. Read/Write
- D. Read
Answer:
D
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/10.10/en/Content/PASIMP/Supported-Target-Machines.htm
Question 7
Which command configures email alerts within PTA if settings need to be changed post install?
- A. /opt/tomcat/utility/emailConfiguration.sh
- B. /opt/PTA/emailConfiguration.sh
- C. /opt/PTA/utility/emailConfig.sh
- D. /opt/tomcat/utility/emailSetup.sh
Answer:
A
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/11.2/en/Content/PTA/Outbound-Sending-PTA-Alerts-to-Email.htm
Question 8
You are creating a new Rest API user that utilizes CyberArk Authentication.
What is a correct process to provision this user?
- A. Private Ark Client > Tools > Administrative Tools > Users and Groups > New > User
- B. Private Ark Client > Tools > Administrative Tools > Directory Mapping > Add
- C. PVWA > User Provisioning > LDAP Integration > Add Mapping
- D. PVWA > User Provisioning > Users and Groups > New > User
Answer:
B
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/WebServices/Implementing%20Privileged%20Account%20S
ecurity%20Web%20Services%20.htm
Question 9
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is
unable to log in directly with the root account and will need to use a secondary account.
How should this be configured to allow for password management using least privilege?
- A. Configure each CPM to use the correct logon account.
- B. Configure each CPM to use the correct reconcile account.
- C. Configure the UNIX platform to use the correct logon account.
- D. Configure the UNIX platform to use the correct reconcile account.
Answer:
C
Explanation:
Reference:https://docs.cyberark.com/Product-
Doc/OnlineHelp/PrivCloud/Latest/en/Content/PASIMP/Linked-PAS-Accounts.htm#Overview
Question 10
DRAG DROP
Match each permission to where it can be found.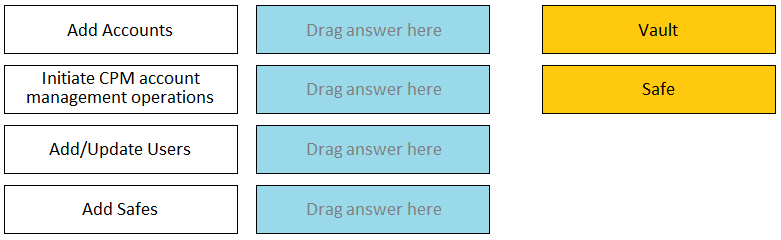
Answer:
None
Explanation: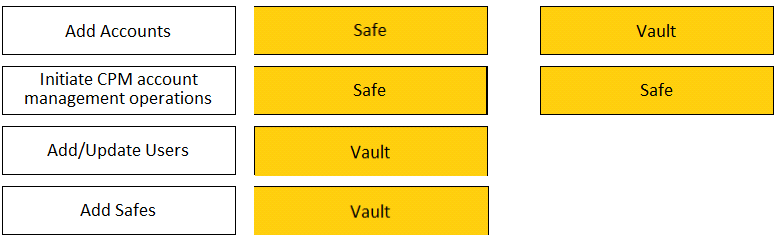
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Safes-add-a-safe-
member.htm?TocPath=Administration%7CPrivileged%20Accounts%7CAccess%20Control%7CSafes%
20and%20Safe%20members%7C_____3
Question 11
In a default CyberArk installation, which group must a user be a member of to view the reports
page in PVWA?
- A. PVWAMonitor
- B. ReportUsers
- C. PVWAReports
- D. Operators
Answer:
A
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/ReportsInPVWA.htm?TocPath=End%20User%7CRe
ports%20and%20Audits%7C_____1#:~:text=Reports%20can%20be%20generated%20in,this%20is%2
0the%20PVWAMonitor%20group
Question 12
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group
will need?
- A. List Accounts, Use Accounts
- B. List Accounts, Use Accounts, Retrieve Accounts
- C. Use Accounts
- D. List Accounts, Use Accounts, Retrieve Accounts, Access Safe without confirmation
Answer:
C
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/PSSO-
PSMConnecPVWA.htm?TocPath=End%20User%7CConnect%20to%20Accounts%7CPrivileged%20Sing
le%20Sign-On%7C_____2
Question 13
Which built-in report from the reports page in PVWA displays the number of days until a password is
due to expire?
- A. Privileged Accounts Inventory
- B. Privileged Accounts Compliance Status
- C. Activity Log
- D. Privileged Accounts CPM Status
Answer:
B
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/ReportsInPVWA.htm?TocPath=End%20User%7CRe
ports%20and%20Audits%7C_____1
Question 14
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
- A. Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details > Add PSM Gateway
- B. Administration > Options > Privileged Session Management > Add Configured PSM Gateway Servers
- C. Administration > Options > Privileged Session Management > Configured PSM Servers > Add PSM Gateway
- D. Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details
Answer:
A
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/PSM_HTML5.htm?TocPath=Administration%7CCo
mponents%7CPrivileged%20Session%20Manager
%7CConfiguration%7C_____10
Question 15
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile
Utility? (Choose three.)
- A. Operating System Username
- B. Host IP Address
- C. Client Hostname
- D. Operating System Type (Linux/Windows/HP-UX)
- E. Vault IP Address
- F. Time Frame
Answer:
A, B, C
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/PAS/11.2/en/Content/PASIMP/CreateCredFile-Utility.htm