my Answer is B
When sizing a Dell EMC Unity Hybrid array, what are considerations for performance?
A
Explanation:
Reference:
https://www.delltechnologies.com/en-us/collaterals/unauth/white-
papers/products/storage/h15093
- dell-emc-unity-best-practices-guide.pdf
A Dell EMC Unity storage administrator has 10 hosts. One of the hosts experiences occasional, huge
IO bursts.
What is a best practice for avoiding performance issues during these burst periods?
D
A customer wants to provision a file system while creating a NAS server in a Dell EMC PowerStore T
system. What information is needed to create the NAS server?
C
Explanation:
The NAS server DNS can be enabled on the next page. For Directory Services, DNS configuration is
required. Add at least one DNS server for the domain.
Reference:
https://topics-cdn.dell.com/pdf/pwrstr-cfg-smb_en-us.pdf
A customer requests a proposal for a new Dell EMC SC Series storage system with the following
specifications:
IO type: Random
Existing data: 100 TB
Rate of change: 2 TB per day
Growth rate: 100 GB per day
Snapshot retention: 1 week
What storage capacity should be specified to scope the system with Tier 1 RAID 10 protection?
C
Which Dell EMC Midrange storage platforms support NVMe SCM drives?
B
my Answer is B
DRAG DROP
In vCenter, what is the correct order of steps to create a VM in a storage container provisioned on a
Dell EMC PowerStore system?
None
Explanation:
STEP1:VASA
STEP2 :POWERSTORE CONNECTIVITY
STEP3:Create vvol datastore
STEP4:create vm storage policies
STEP5:Provision VMs based on vvol datastore
Reference:
https://www.delltechnologies.com/en-us/collaterals/unauth/white-
papers/products/storage/h18152-dell-emc- powerstore-virtualization-integration.pdf
A Dell EMC PowerStore customer wants to schedule snapshots daily at 6 AM. Which snapshot
frequency interval (in minutes) is available?
A
Explanation:
Reference:
https://www.delltechnologies.com/en-us/collaterals/unauth/white-
papers/products/storage/h18156
- dell-emc-powerstore-snapshots-thin-clones.pdf (27)
In Dell EMC PowerStore storage, if the remote cluster has multiple appliances, then what
automatically chooses the destination appliance for the resource?
B
Explanation:
From the POWERSTORE ADMINISTRATION PARTICIPANT GUIDE,
" Resource balancer also considers the the following when placing volumes:
Whether the appliance is offline
Appliance failure status
Capacity utilization
DRAG DROP
Match each term with its description.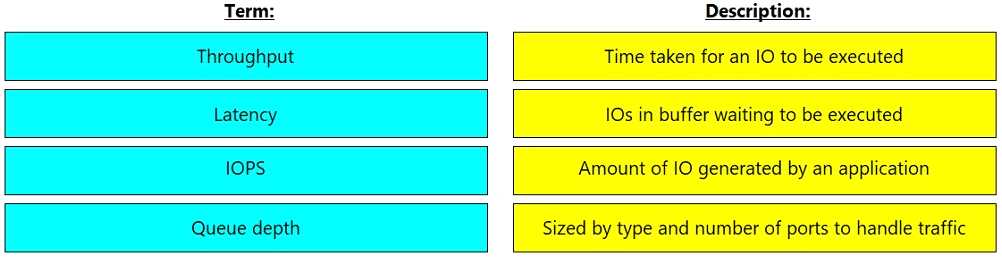
None
Explanation:
Throughput = Sized by type and number of ports to handle traffic
Latency = Time taken for an IO to be executed
IOPS = Amount IO generated by application
Queue depth = IOS in buffer waiting to be executed
What is a feature of Dell EMC Unity unified snapshots?
C
Explanation:
Reference;
https://www.delltechnologies.com/en-ba/collaterals/unauth/white-
papers/products/storage/h15089
- dell_emc_unity-snapshots_and_thin_clones.pdf (7)
Which NVMe SSDs are supported by Dell EMC PowerStore?
D
Explanation:
https://www.delltechnologies.com/resources/en-us/asset/data-sheets/products/storage/h18143-
dell-emc-powerstore-family-spec-sheet.pdf
Which feature helps to enable file service High Availability on Dell EMC PowerStore?
A
Explanation:
Reference:
https://www.delltechnologies.com/resources/en-us/asset/white-
papers/products/storage/h18157
- dell-emc-powerstore-clustering-high-availability.pdf
What is a characteristic of tenant traffic on a Dell EMC Unity array?
A
A customer is managing a Dell EMC SC7020 array running SCOS 7.2. The array is running out of
capacity. The customer asks you to begin scoping the system for additional drives. What disk drive
redundancy rule applies to 3.84 TB SSDs?
B
What are characteristics of D@RE on a Dell EMC Unity array?
D
Explanation:
controller-based D@RE has minimal performance impact for typical mixed workloads, and no impact
to other Dell EMC Unity data services due to the level at which the encryption is performed, which is
after
all
data
services
have
been
applied.
https://www.delltechnologies.com/en-
us/collaterals/unauth/white-papers/products/storage/h15090-dell-emc-unity-data-at-rest-
encryption.pdf