Fortinet nse6-fac-6-1 practice test
Fortinet NSE 6 - FortiAuthenticator 6.1 Exam
Last exam update: Mar 26 ,2025
Question 1
Which two features of FortiAuthenticator are used for EAP deployment? (Choose two)
- A. Certificate authority
- B. LDAP server
- C. MAC authentication bypass
- D. RADIUS server
Answer:
A, D
Question 2
Which behaviors exist for certificate revocation lists (CRLs) on FortiAuthenticator? (Choose two)
- A. CRLs contain the serial number of the certificate that has been revoked
- B. Revoked certificates are automaticlly placed on the CRL
- C. CRLs can be exported only through the SCEP server
- D. All local CAs share the same CRLs
Answer:
A, B
Question 3
You are a FortiAuthenticator administrator for a large organization. Users who are configured to use
FortiToken 200 for two-factor authentication can no longer authenticate. You have verified that only
the users with two-factor authentication are experiencing the issue.
What can couse this issue?
- A. On of the FortiAuthenticator devices in the active-active cluster has failed
- B. FortiAuthenticator has lose contact with the FortiToken Cloud servers
- C. FortiToken 200 licence has expired
- D. Time drift between FortiAuthenticator and hardware tokens
Answer:
D
Question 4
Which two statements about the EAP-TTLS authentication method are true? (Choose two)
- A. Uses mutual authentication
- B. Uses digital certificates only on the server side
- C. Requires an EAP server certificate
- D. Support a port access control (wired) solution only
Answer:
B, C
Question 5
When you are setting up two FortiAuthenticator devices in active-passive HA, which HA role must
you select on the master FortiAuthenticator?
- A. Active-passive master
- B. Standalone master
- C. Cluster member
- D. Load balancing master
Answer:
C
Question 6
Which EAP method is known as the outer authentication method?
- A. PEAP
- B. EAP-GTC
- C. EAP-TLS
- D. MSCHAPV2
Answer:
A
Question 7
Refer to the exhibit.
Examine the screenshot shown in the exhibit.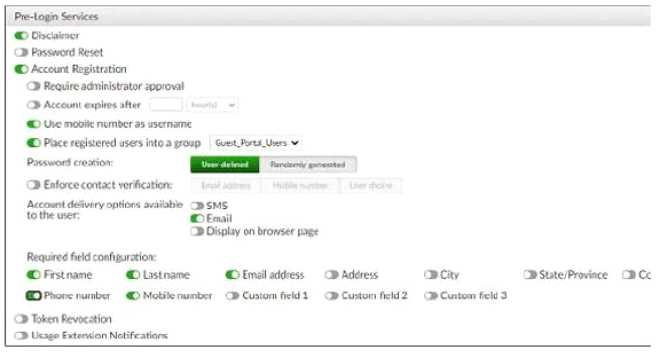
Which two statements regarding the configuration are true? (Choose two)
- A. All guest accounts created using the account registration feature will be placed under the Guest_Portal_Users group
- B. All accounts registered through the guest portal must be validated through email
- C. Guest users must fill in all the fields on the registration form
- D. Guest user account will expire after eight hours
Answer:
A, B
Question 8
Which statement about the guest portal policies is true?
- A. Guest portal policies apply only to authentication requests coming from unknown RADIUS clients
- B. Guest portal policies can be used only for BYODs
- C. Conditions in the policy apply only to guest wireless users
- D. All conditions in the policy must match before a user is presented with the guest portal
Answer:
D
Question 9
Which two capabilities does FortiAuthenticator offer when acting as a self-signed or local CA?
(Choose two)
- A. Validating other CA CRLs using OSCP
- B. Importing other CA certificates and CRLs
- C. Merging local and remote CRLs using SCEP
- D. Creating, signing, and revoking of X.509 certificates
Answer:
B, D
Question 10
Which three of the following can be used as SSO sources? (Choose three)
- A. FortiClient SSO Mobility Agent
- B. SSH Sessions
- C. FortiAuthenticator in SAML SP role
- D. Fortigate
- E. RADIUS accounting
Answer:
A, C, E
Question 11
You are the administrator of a large network that includes a large local user datadabase on the
current Fortiauthenticatior. You want to import all the local users into a new Fortiauthenticator
device.
Which method should you use to migrate the local users?
- A. Import users using RADIUS accounting updates.
- B. Import the current directory structure.
- C. Import users from RADUIS.
- D. Import users using a CSV file.
Answer:
D
Question 12
Which two types of digital certificates can you create in Fortiauthenticator? (Choose two)
- A. User certificate
- B. Organization validation certificate
- C. Third-party root certificate
- D. Local service certificate
Answer:
A, D
Question 13
What happens when a certificate is revoked? (Choose two)
- A. Revoked certificates cannot be reinstated for any reason
- B. All certificates signed by a revoked CA certificate are automatically revoked
- C. Revoked certificates are automatically added to the CRL
- D. External CAs will priodically query Fortiauthenticator and automatically download revoked certificates
Answer:
C, D
Question 14
Which two SAML roles can Fortiauthenticator be configured as? (Choose two)
- A. Idendity provider
- B. Principal
- C. Assertion server
- D. Service provider
Answer:
A, D
Question 15
A device or user identity cannot be established transparently, such as with non-domain BYOD
devices, and allow users to create their own credentialis.
In this case, which user idendity discovery method can Fortiauthenticator use?
- A. Syslog messaging or SAML IDP
- B. Kerberos-base authentication
- C. Radius accounting
- D. Portal authentication
Answer:
D