Fortinet nse6-fml-7-2 practice test
fortinet nse 6 - fortimail 7.2
Last exam update: Mar 26 ,2025
Question 1
Refer to the exhibit which shows the output of an email transmission using a telnet session.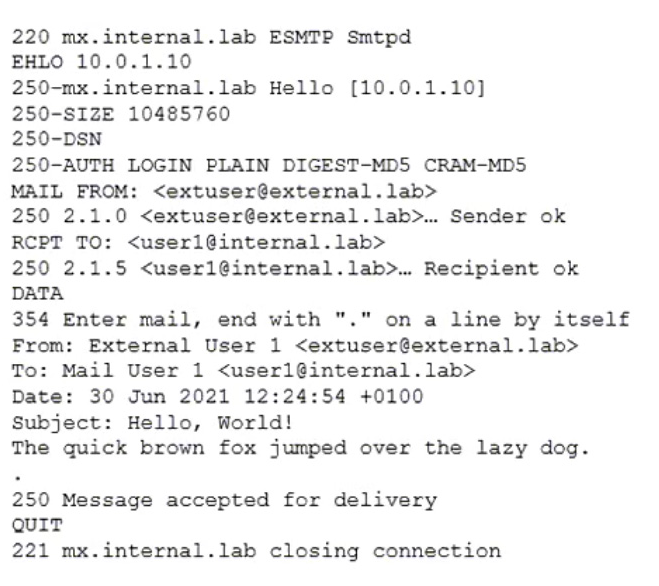
What are two correct observations about this SMTP session? (Choose two.)
- A. The SMTP envelope addresses are different from the message header addresses.
- B. The "250 Message accepted for delivery" message is part of the message body.
- C. The "Subject" is part of the message header.
- D. The "220 mx.internal.lab ESMTP Smtpd" message is part of the SMTP banner.
Answer:
cd
Question 2
Refer to the exhibits showing SMTP limits (Session Profile SMTP Limits), and domain settings (Domain Settings, and Domain Settings Other) of a FortiMail device.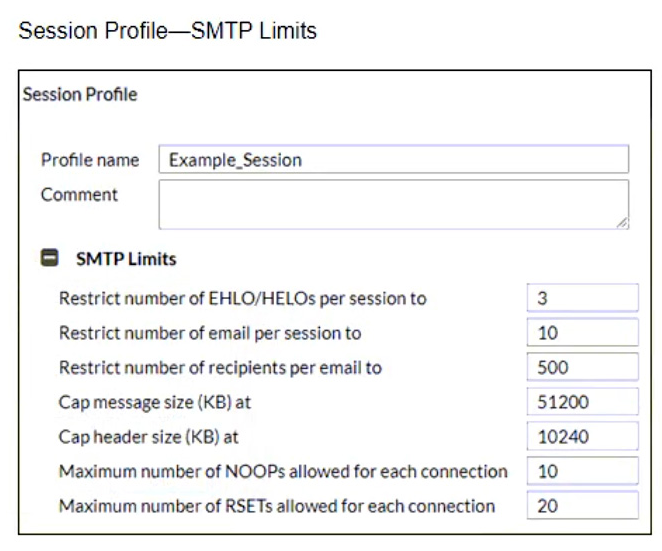
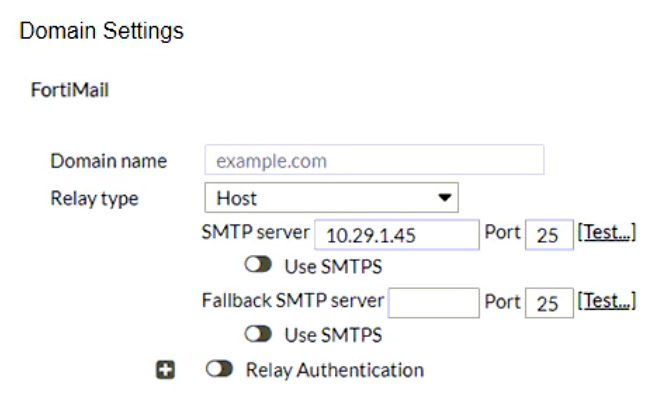
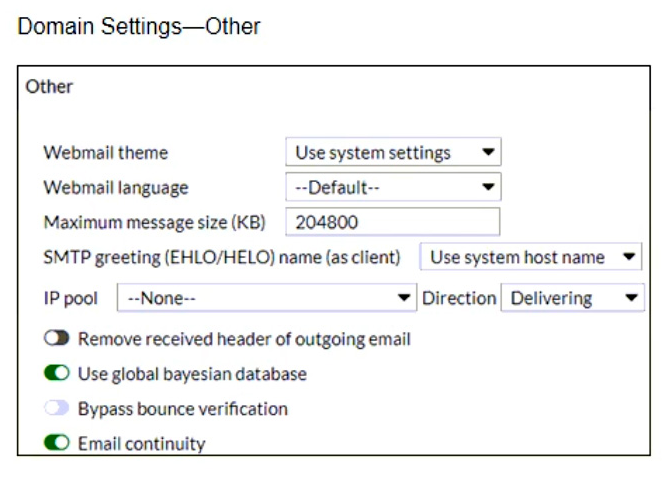
Which message size limit in KB will the FortiMail apply to outbound email?
- A. 204800
- B. There is no message size limit for outbound email from a protected domain.
- C. 10240
- D. 51200
Answer:
d
Question 3
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).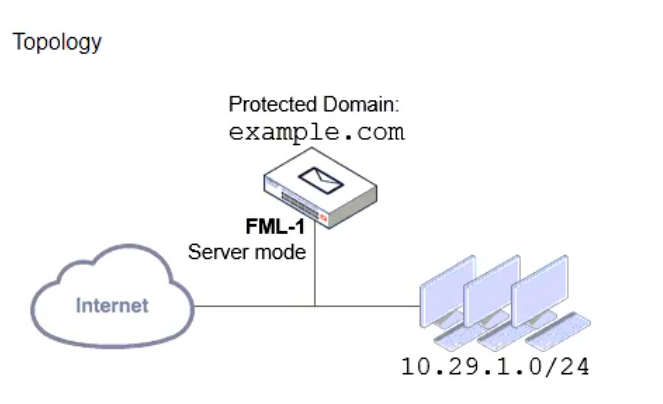
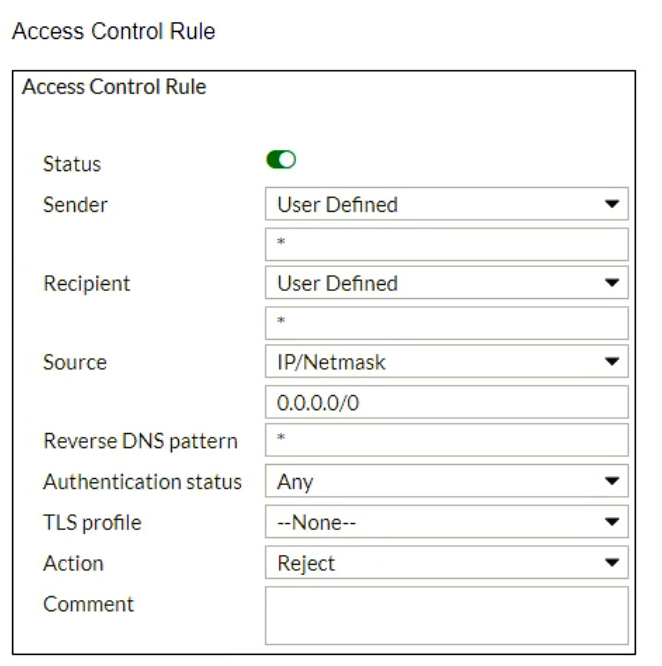
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
- A. The Sender IP/netmask should be set to 10.29.1.0/24.
- B. The Action should be set to Reject.
- C. The Recipient pattern should be set to *@example.com.
- D. The Authentication status should be set to Authenticated.
Answer:
ad
Question 4
Refer to the exhibit which displays a topology diagram.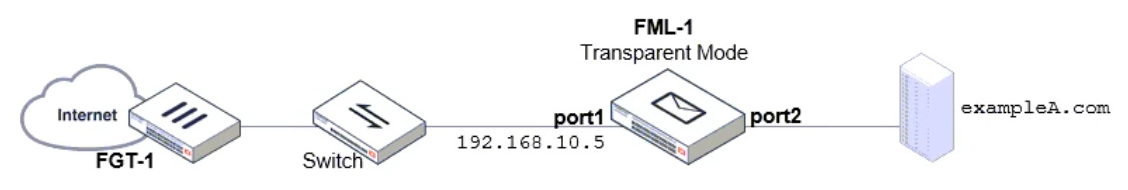
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
- A. If port1 is required to process SMTP traffic, it must be configured as a routed interface.
- B. All bridge member interfaces belong to the same subnet as the management IP.
- C. The management IP is permanently tied to port1, and port1 cannot be removed from the bridge.
- D. Any bridge member interface can be removed from the bridge and configured as a routed interface.
Answer:
bc
Question 5
Refer to the exhibit, which shows a few lines of FortiMail logs.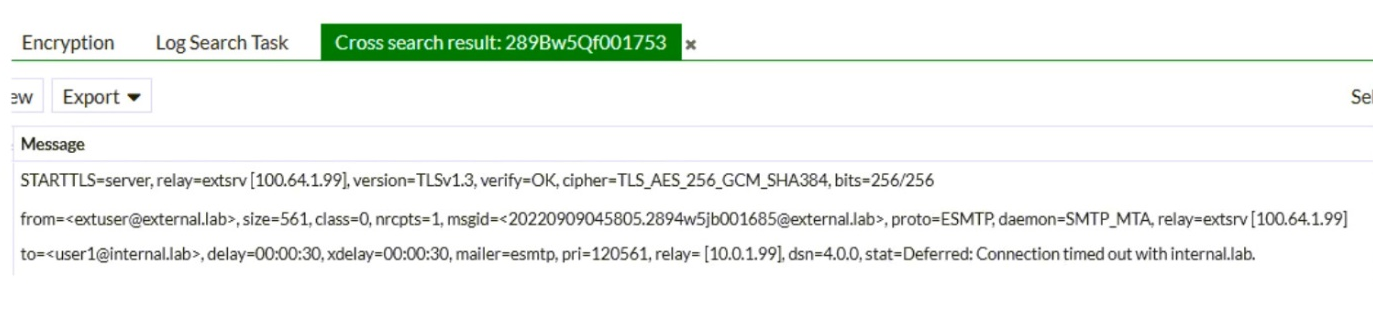
Based on these log entries, which two statements correctly describe the operational status of this FortiMail device? (Choose two.)
- A. FortiMail is experiencing issues delivering the email to the internal.lab MTA.
- B. The FortiMail device is in sever mode.
- C. The FortiMail device is in gateway or transparent mode.
- D. FortiMail is experiencing issues accepting the connection from the external.lab MTA.
Answer:
ac
Question 6
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
- A. Access control policy number 9 was used.
- B. The FortiMail configuration is missing an access delivery rule.
- C. The email was processed using IP-based policy ID 4.
- D. FortiMail is applying the default behavior for relaying inbound email.
Answer:
ac
Question 7
Refer to the exhibit which shows an nslookup output of MX records of the example.com domain.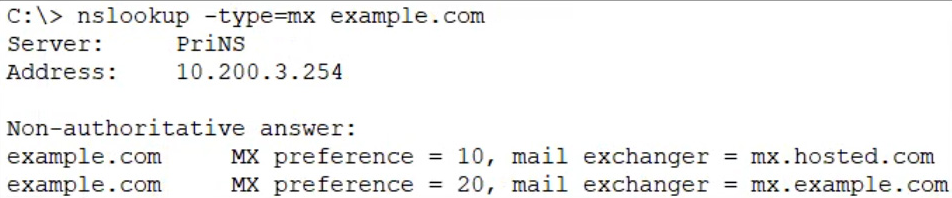
Which two MTA selection behaviors for the example.com domain are correct? (Choose two.)
- A. mx.example.com will receive approximately twice the number of email as mx.hosted.com because of its preference value.
- B. The primary MTA for the example.com domain is mx.hosted.com.
- C. The external MTAs will send email to mx.example.com only if mx.hosted.com is unreachable.
- D. The PriNS server should receive all email for the example.com domain.
Answer:
bc
Question 8
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
- A. IP Policy configuration
- B. Protected Domain configuration
- C. Resource Profile configuration
- D. Session Profile configuration
Answer:
bc
Question 9
Refer to the exhibit which displays a history log entry.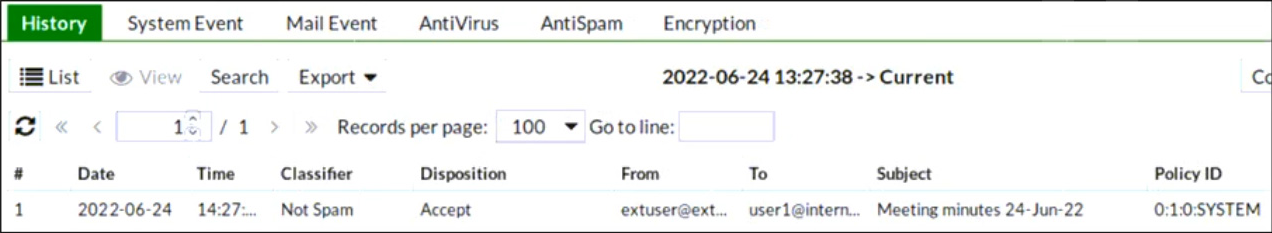
Why does the last field show SYSTEM in the Policy ID column?
- A. The email was dropped by a system blocklist.
- B. It is an inbound email.
- C. The email matched a system-level authentication policy.
- D. The email did not match a recipient-based policy.
Answer:
d
Question 10
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
- A. Impersonation analysis
- B. Dictionary profile with predefined smart identifiers
- C. Bounce tag verification
- D. Content disarm and reconstruction
Answer:
a