Fortinet nse6-fwf-6-4 practice test
Fortinet NSE 6 - Secure Wireless LAN 6.4 Exam
Last exam update: Mar 06 ,2025
Question 1
Refer to the exhibit.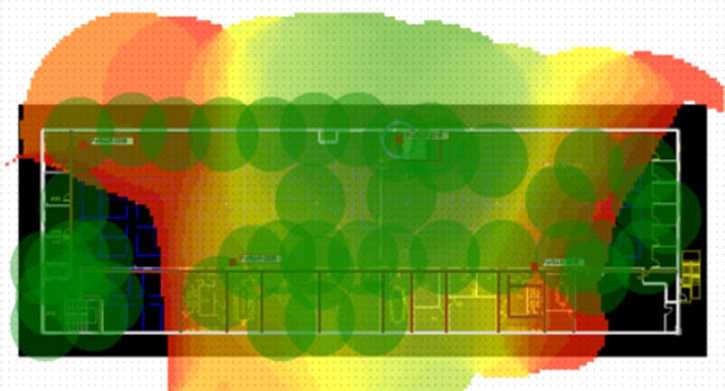
If the signal is set to -68 dB on the FortiPlanner site survey reading, which statement is correct
regarding the coverage area?
- A. Areas with the signal strength equal to -68 dB are zoomed in to provide better visibility
- B. Areas with the signal strength weaker than -68 dB are cut out of the map
- C. Areas with the signal strength equal or stronger than -68 dB are highlighted in multicolor
- D. Areas with the signal strength weaker than -68 dB are highlighted in orange and red to indicate that no signal was propagated by the APs.
Answer:
D
Question 2
Six APs are located in a remotely based branch office and are managed by a centrally hosted
FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote
office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN
connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
- A. Configure a tunnel mode wireless network and enable split tunneling to the local network
- B. Configure a bridge mode wireless network and enable the Local standalone configuration option
- C. Configure a bridge mode wireless network and enable the Local authentication configuration option
- D. Install supported FortiAP and configure a bridge mode wireless network
Answer:
A
Question 3
When using FortiPresence as a captive portal, which two types of public authentication services can
be used to access guest Wi-Fi? (Choose two.)
- A. Social networks authentication
- B. Software security token authentication
- C. Short message service authentication
- D. Hardware security token authentication
Answer:
A, C
Question 4
Refer to the exhibit.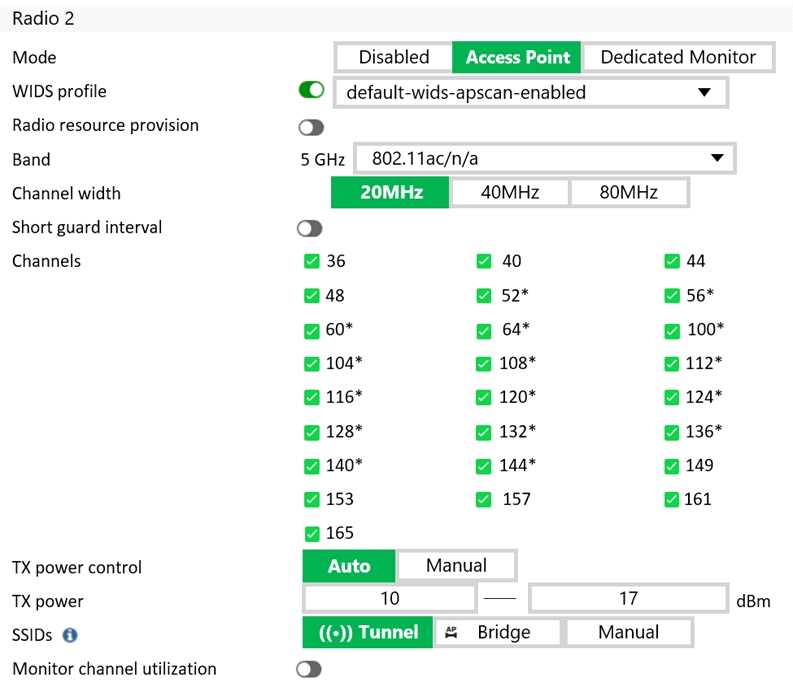
What does the asterisk (*) symbol beside the channel mean?
- A. Indicates channels that can be used only when Radio Resource Provisioning is enabled
- B. Indicates channels that cannot be used because of regulatory channel restrictions
- C. Indicates channels that will be scanned by the Wireless Intrusion Detection System (WIDS)
- D. Indicates channels that are subject to dynamic frequency selection (DFS) regulations
Answer:
D
Question 5
As standard best practice, which configuration should be performed before configuring FortiAPs
using a FortiGate wireless controller?
- A. Create wireless LAN specific policies
- B. Preauthorize APs
- C. Create a custom AP profile
- D. Set the wireless controller country setting
Answer:
D
Question 6
What type of design model does FortiPlanner use in wireless design project?
- A. Architectural model
- B. Predictive model
- C. Analytical model
- D. Integration model
Answer:
B
Question 7
Which two roles does FortiPresence analytics assist in generating presence reports? (Choose two.)
- A. Gathering details about on site visitors
- B. Predicting the number of guest users visiting on-site
- C. Comparing current data with historical records
- D. Reporting potential threats by guests on site
Answer:
A, C
Explanation:
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/457ebad4-
2437-11e9-b20a-f8bc1258b856/FortiPresence-v2.0-getting-started.pdf
Question 8
You are investigating a wireless performance issue and you are trying to audit the neighboring APs in
the PF environment. You review the Rogue APs widget on the GUI but it is empty, despite the known
presence of other APs.
Which configuration change will allow neighboring APs to be successfully detected?
- A. Enable Locate WiFi clients when not connected in the relevant AP profiles.
- B. Enable Monitor channel utilization on the relevant AP profiles.
- C. Ensure that all allowed channels are enabled for the AP radios.
- D. Enable Radio resource provisioning on the relevant AP profiles.
Answer:
D
Explanation:
The ARRP (Automatic Radio Resource Provisioning) profile improves upon DARRP (Distributed
Automatic Radio Resource Provisioning) by allowing more factors to be considered to optimize
channel selection among FortiAPs. DARRP uses the neighbor APs channels and signal strength
collected from the background scan for channel selection.
Reference:
https://docs.fortinet.com/document/fortigate/6.4.0/new-features/228374/add-arrp-
profile-for-wireless-controller-6-4-2
Question 9
Which administrative access method must be enabled on a FortiGate interface to allow APs to
connect and function?
- A. Security Fabric
- B. SSH
- C. HTTPS
- D. FortiTelemetry
Answer:
A
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.9/cookbook/788897/configuring-the-
root-fortigate-and-downstream-fortigates
Question 10
Where in the controller interface can you find a wireless clients upstream and downstream link
rates?
- A. On the AP CLI, using the cw_diag ksta command
- B. On the controller CLI, using the diag wireless-controller wlac -d sta command
- C. On the AP CLI, using the cw_diag -d sta command
- D. On the controller CLI, using the WiFi Client monitor
Answer:
A
Question 11
Which two configurations are compatible for Wireless Single Sign-On (WSSO)? (Choose two.)
- A. A VAP configured for captive portal authentication
- B. A VAP configured for WPA2 or 3 Enterprise
- C. A VAP configured to authenticate locally on FortiGate
- D. A VAP configured to authenticate using a radius server
Answer:
B, D
Explanation:
In the SSID choose WPA2-Enterprise authentication.
WSSO is RADIUS-based authentication that passes the user's user group memberships to the
FortiGate.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/b92a67f9-
73a6-11ea-9384-00505692583a/FortiWiFi_and_FortiAP-6.4.2-Configuration_Guide.pdf
Question 12
Part of the location service registration process is to link FortiAPs in FortiPresence.
Which two management services can configure the discovered AP registration information from the
FortiPresence cloud? (Choose two.)
- A. AP Manager
- B. FortiAP Cloud
- C. FortiSwitch
- D. FortiGate
Answer:
B, D
Explanation:
FortiGate, FortiCloud wireless access points (send visitor data in the form of station reports directly
to FortiPresence)
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/df877622-
c976-11e9-8977-00505692583a/FortiPresence-v4.3-release-notes.pdf
Question 13
When enabling security fabric on the FortiGate interface to manage FortiAPs, which two types of
communication channels are established between FortiGate and FortiAPs? (Choose two.)
- A. Control channels
- B. Security channels
- C. FortLink channels
- D. Data channels
Answer:
A, D
Explanation:
The control channel for managing traffic, which is always encrypted by DTLS. l The data channel for
carrying client data packets.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/ac61f4d3-
ce67-11e9-8977-00505692583a/FortiWiFi_and_FortiAP-6.2-Cookbook.pdf
Question 14
Which two phases are part of the process to plan a wireless design project? (Choose two.)
- A. Project information phase
- B. Hardware selection phase
- C. Site survey phase
- D. Installation phase
Answer:
AC
Question 15
When configuring a wireless network for dynamic VLAN allocation, which three IETF attributes must
be supplied by the radius server? (Choose three.)
- A. 81 Tunnel-Private-Group-ID
- B. 65 Tunnel-Medium-Type
- C. 83 Tunnel-Preference
- D. 58 Egress-VLAN-Name
- E. 64 Tunnel-Type
Answer:
A, B, E
Explanation:
The RADIUS user attributes used for the VLAN ID assignment are:
IETF 64 (Tunnel Type)Set this to VLAN.
IETF 65 (Tunnel Medium Type)Set this to 802
IETF 81 (Tunnel Private Group ID)Set this to VLAN ID.
Reference:
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-vlan/71683-dynamicvlan-config.html