HP hpe6-a68 practice test
Aruba Certified Clearpass Professional 6.7 Exam
Last exam update: Mar 26 ,2025
Question 1
Refer to the exhibit.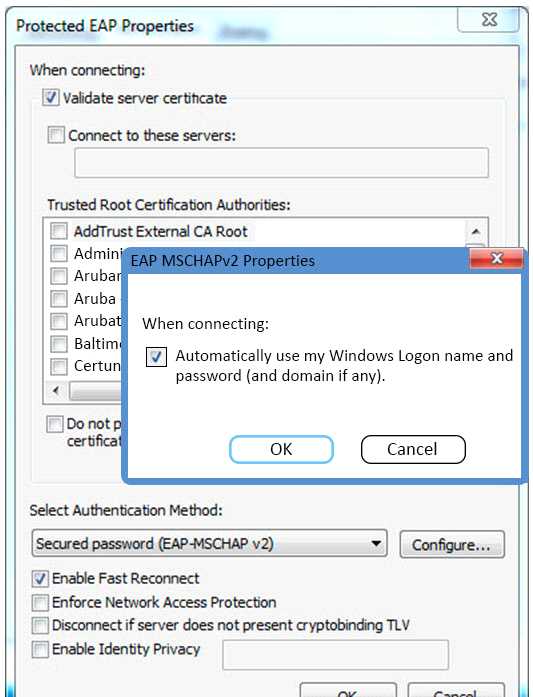
Based on the configuration of a Windows 802.1X supplicant shown, what will be the outcome when
Automatically use my Windows logon name and password are selected?
- A. The client will use machine authentication.
- B. The clients Windows login username and password will be sent inside a certificate to the Active Directory server.
- C. The client’s Windows login username and password will be sent to the Authentication server.
- D. The client will need to re-authenticate every time they connect to the network.
- E. The client will prompt the user to enter the logon username and password.
Answer:
C
Question 2
What is the purpose of ClearPass Onboard?
- A. to provide MAC authentication for devices that don’t support 802.1x
- B. to run health checks on end user devices
- C. to provision personal devices to securely connect to the network
- D. to configure self-registration pages for guest users
- E. to provide guest access for visitors to connect to the network
Answer:
C
Question 3
Refer to the exhibit.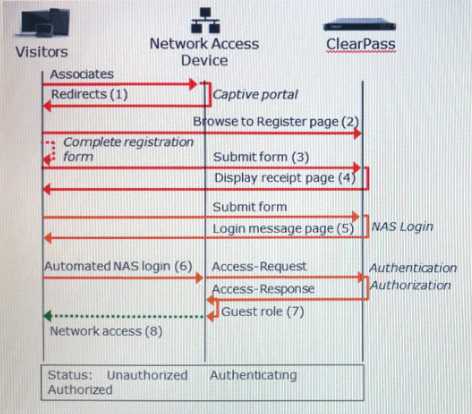
Based on the guest Self-Registration with Sponsor Approval workflow shown, at which stage does the
sponsor approve the users request?
- A. After the RADIUS Access-Request
- B. After the NAS login, but before the RADIUS Access-Request
- C. Before the user can submit the registration form
- D. After the RADIUS Access-Response
- E. After the receipt page is displayed, before the NAS login
Answer:
E
Question 4
Use this form to make changes to the RADIUS Web Login Guest Network.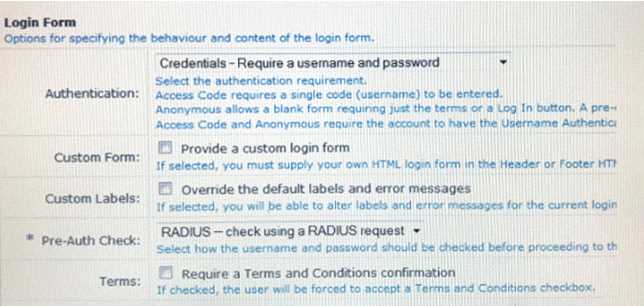
A Web Login page is configured in Clear Pass Guest as shown.
What is the purpose of the Pre-Auth Check?
- A. To authenticate users after the NAD sends an authentication request to ClerPass
- B. To authenticate users before the client sends the credentials to the NAD
- C. To authenticate users when they are roaming from one NAD to another
- D. To authenticate users before they launch the Web Login Page
- E. To replace the need for the NAD to send an authentication request to ClearPass
Answer:
B
Question 5
Refer to the exhibit.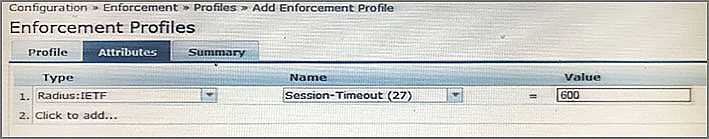
An Enforcement Profile has been created in the Policy Manager as shown.
Which action will ClearPass take based on the Enforcement Profile?
- A. It will send the Session-Timeout attribute in the RADIUS Access-Request packet to the NAD and the NAD will end the users session after 600 seconds.
- B. It will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the User and the users session will be terminated after 600 seconds.
- C. It will count down 600 seconds and send a RADUIS CoA message to the NAD to end the users session after this time is up.
- D. It will count down 600 seconds and send a RADUIUS CoA message to the user to end the users session after this time is up.
- E. It will send the session –Timeout attribute in the RADIUS Access-Accept packet to the NAD and the NAD will end the user’s session after 600 seconds.
Answer:
E
Question 6
Refer to the exhibit.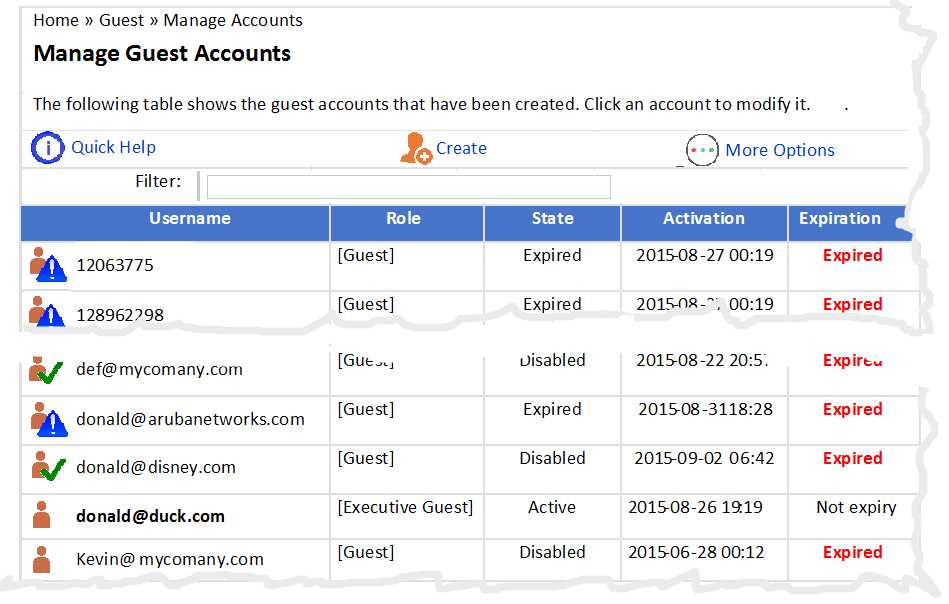
An administrator logs in to the Guest module in ClearPass and Manage Accounts displays as shown.
When a user with username [email protected] attempts to access the Web Login page, what will
be the outcome?
- A. The user will be able to log in and authenticate successfully but will then be immediate disconnected.
- B. The user will be able to log in for the next 4.9. days, but then will no longer be able to log in.
- C. The user will not be able to log in and authenticate.
- D. The user will be able to log in and authenticate successfully, but will then get a quarantine role.
- E. The user will not be able to access the Web Login page.
Answer:
C
Question 7
In which ways can ClearPass derive client roles during policy service processing? (Select two.)
- A. From the attributes configured in Active Directory
- B. From the server derivation rule in the Aruba Controller server group for the client
- C. From the Aruba Network Access Device
- D. From the attributes configured in a Network Access Device
- E. Through a role mapping policy
Answer:
A,E
Question 8
Refer to the exhibit.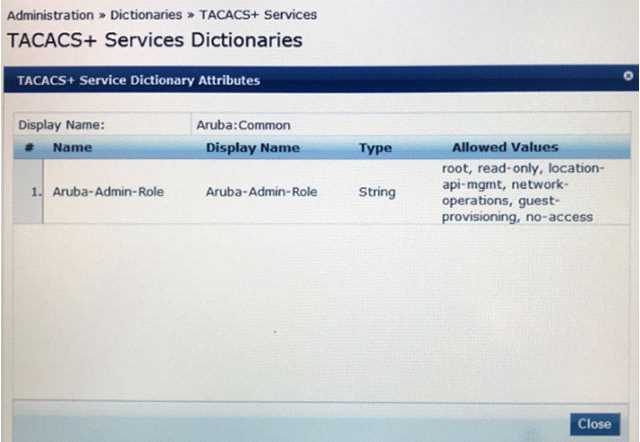
Based on the Aruba TACACS+ dictionary shown, how is the Aruba-Role attribute used?
- A. The Aruba-Admin-Role on the controller is applies to users using TACACS+ to login to the Policy Manager
- B. To assign different privileges to clients during 802.1X authentication
- C. To assign different privileges to administrators logging into an Aruba NAD
- D. It is used by ClearPass to assign TIPS roles to clients during 802.1X authentication
- E. To assign different privileges to administrators logging into ClearPass
Answer:
C
Question 9
Refer to the exhibit.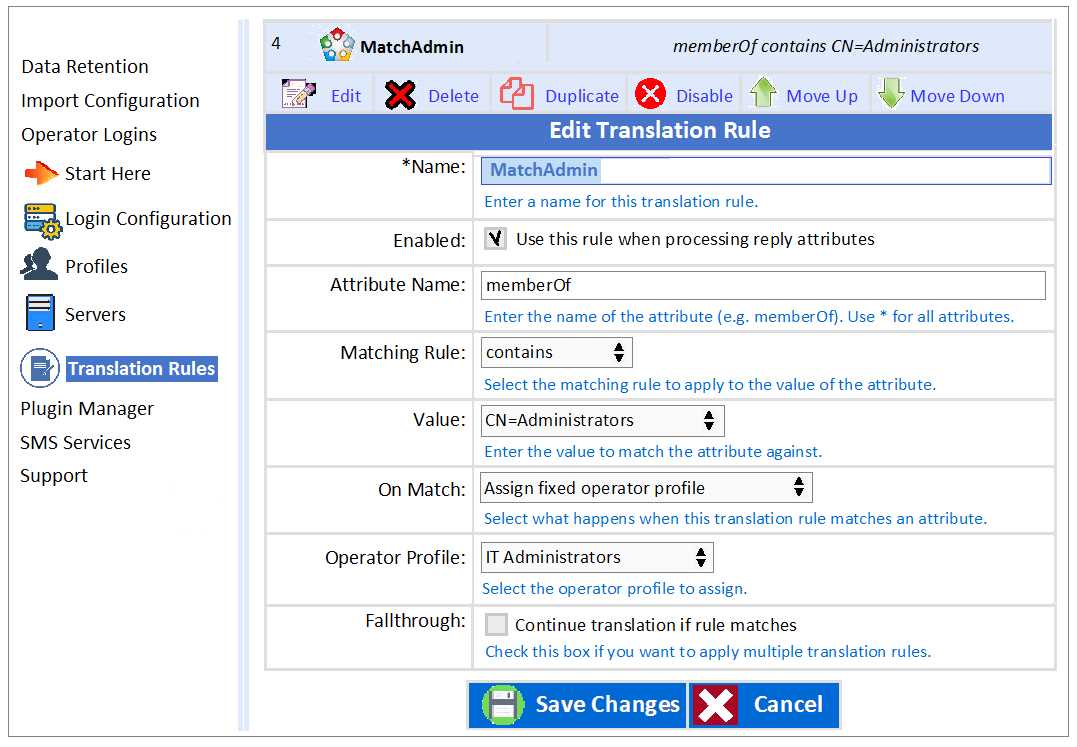
Based on the Translation Rule configuration shown, what will be the outcome?
- A. An AD user from group Administrators will be assigned the operator profile of IT Administrators.
- B. All ClearPass Policy Manager admin users who are members of the Administrators AD group will be assigned the TACACS profile of IT Administrators.
- C. All active directory users will be assigned the operator profile of IT Administrators.
- D. A user from AD group MatchAdmin will be assigned the operator profile of IT Administrators.
Answer:
A
Question 10
A customer would like to deploy ClearPass with these requirements:
-2000 devices need to be Onboarded
-2000 corporate devices need to run posture checks daily
-500 guest users need to authenticate each day using the web login feature
What is the license mix that customer will need to purchase?
- A. CP-HW-5k, 2500 ClearPass Enterprise
- B. CP-HW-25k, 4500 ClearPass Enterprise
- C. CP-HW-500, 2500 ClearPass Enterprise
- D. CP-HW-25k, 4000 ClearPass Enterprise
- E. CP-HW-5k, 4500 ClearPass Enterprise
Answer:
B
Question 11
Which use cases will require a ClearPass Guest application license? (Select two.)
- A. Guest device fingerprinting
- B. Guest endpoint health assessment
- C. Sponsor based guest user access
- D. Guest user self-registration for access
- E. Guest personal device onboarding
Answer:
C,D
Question 12
Refer to the exhibit.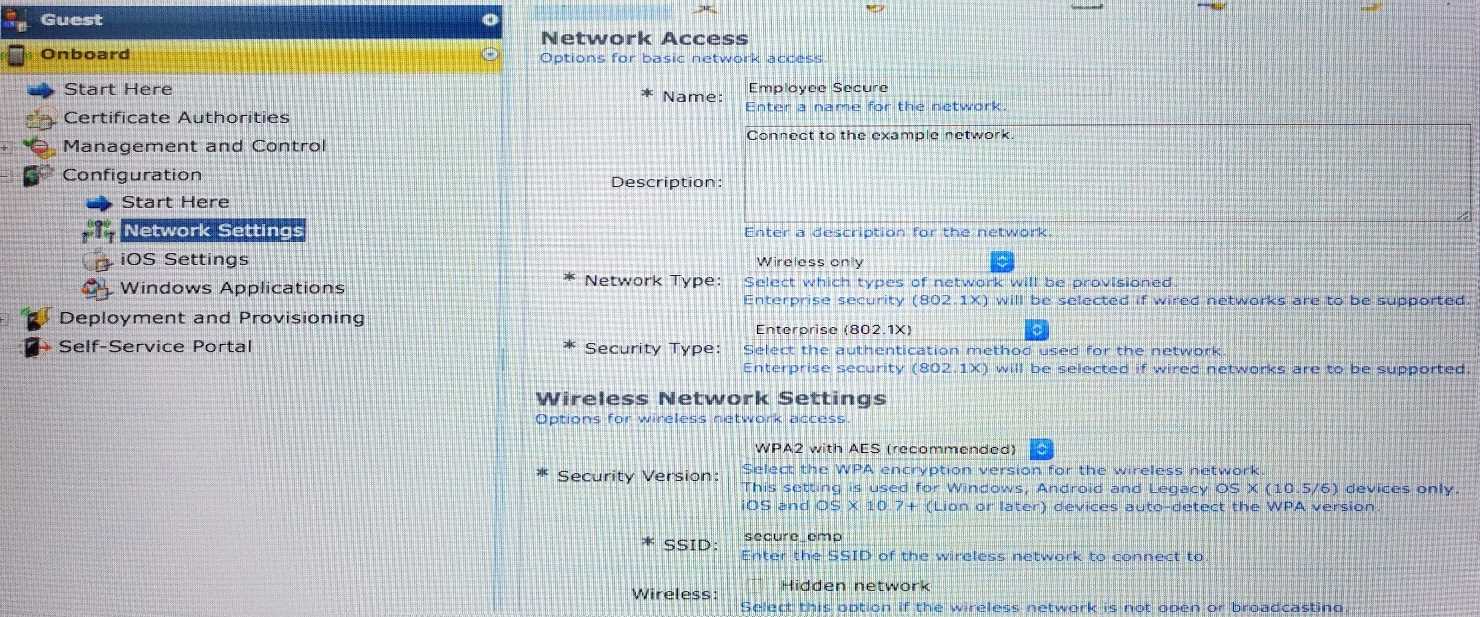
Which statements accurately describe the status of the Onboarded devices in the configuration for
the network settings shown? (Select two.)
- A. They will connect to Employee_Secure SSID after provisioning.
- B. They will connect to Employee_Secure SSID for provisioning their devices.
- C. They will use WPA2-PSK with AES when connecting to the SSID.
- D. They will connect to secure_emp SSID after provisioning.
- E. They will perform 802.1X authentication when connecting to the SSID.
Answer:
D,E
Question 13
An organization implements dual SSID Onboarding. The administrator used the Onboard service
template to create services for dual SSID Onboarding.
Which statement accurately describes the outcome?
- A. The Onboard Provisioning service is triggered when the user connects to the provisioning SSID to Onboard their device.
- B. The Onboard Authorization service is triggered when the user connects to the secure SSID.
- C. The Onboard Authorization service is triggered during the Onboarding process.
- D. The device connects to the secure SSID for provisioning.
- E. The Onboard Authorization service is never triggered.
Answer:
C
Question 14
In a single SSID Onboarding, which method can be used in the Enforcement Policy to distinguish
between a provisioned device and a device that has not gone through the Onboard workflow?
- A. Active Directory Attributes
- B. Network Access Device used
- C. Endpoint OS Category
- D. Onguard Agent used
- E. Authentication Method used
Answer:
E
Question 15
Refer to the exhibit.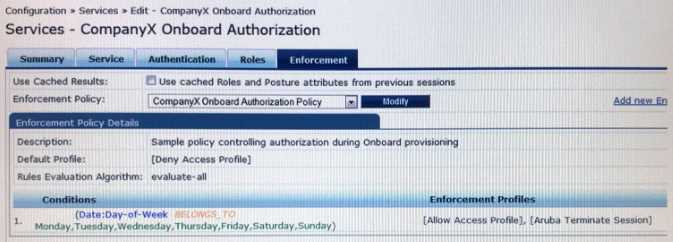
Based on the configuration of the Enforcement Profiles in the Onboard Authorization service shown,
which Onboarding action will occur?
- A. The device will be disconnected from the network after Onboarding so that an EAP-TLS authentication is not performed.
- B. The device will be disconnected from and reconnected to the network after Onboarding is completed.
- C. The device’s onboard authorization request will be denied.
- D. The device will be disconnected after post-Onboarding EAP-TLS authentication, so a second EAP- TLS authentication is performed.
- E. After logging in on the Onboard web login page, the device will be disconnected form and reconnected to the network before Onboard begins.
Answer:
B