HP hpe6-a78 practice test
Aruba Certified Network Security Associate Exam
Last exam update: Mar 26 ,2025
Question 1
What is symmetric encryption?
- A. It simultaneously creates ciphertext and a same-size MAC.
- B. It any form of encryption mat ensures that thee ciphertext Is the same length as the plaintext.
- C. It uses the same key to encrypt plaintext as to decrypt ciphertext.
- D. It uses a Key that is double the size of the message which it encrypts.
Answer:
C
Question 2
What is one way that WPA3-PerSonal enhances security when compared to WPA2-Personal?
- A. WPA3-Perscn3i is more secure against password leaking Because all users nave their own username and password
- B. WPA3-Personai prevents eavesdropping on other users' wireless traffic by a user who knows the passphrase for the WLAN.
- C. WPA3-Personai is more resistant to passphrase cracking Because it requires passphrases to be at least 12 characters
- D. WPA3-Personal is more complicated to deploy because it requires a backend authentication server
Answer:
A
Question 3
Refer to the exhibit, which shows the current network topology.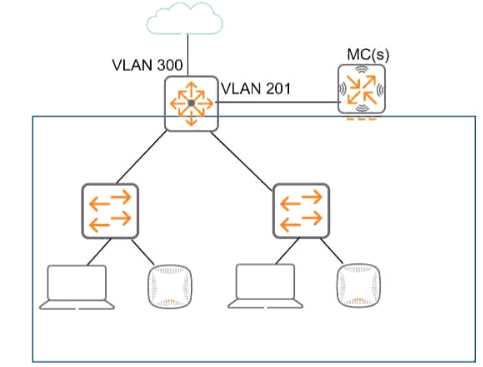
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility
Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the
forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
- A. Assign the WLAN to a single new VLAN which is dedicated to wireless users
- B. Use wireless user roles to assign the devices to different VLANs in the 100-150 range
- C. Assign the WLAN to a named VLAN which specified 100-150 as the range of IDs.
- D. Use wireless user roles to assign the devices to a range of new vlan IDs.
Answer:
B
Question 4
What is one difference between EAP-Tunneled Layer security (EAP-TLS) and Protected EAP (PEAP)?
- A. EAP-TLS creates a TLS tunnel for transmitting user credentials, while PEAP authenticates the server and supplicant during a TLS handshake.
- B. EAP-TLS requires the supplicant to authenticate with a certificate, hut PEAP allows the supplicant to use a username and password.
- C. EAP-TLS begins with the establishment of a TLS tunnel, but PEAP does not use a TLS tunnel as part of Its process
- D. EAP-TLS creates a TLS tunnel for transmitting user credentials securely while PEAP protects user credentials with TKIP encryption.
Answer:
B
Question 5
You are deploying an Aruba Mobility Controller (MC). What is a best practice for setting up secure
management access to the ArubaOS Web UP
- A. Avoid using external manager authentication tor the Web UI.
- B. Change the default 4343 port tor the web UI to TCP 443.
- C. Install a CA-signed certificate to use for the Web UI server certificate.
- D. Make sure to enable HTTPS for the Web UI and select the self-signed certificate Installed in the factory.
Answer:
C
Question 6
What correctly describes the Pairwise Master Key (PMK) in thee specified wireless security protocol?
- A. In WPA3-Enterprise, the PMK is unique per session and derived using Simultaneous Authentication of Equals.
- B. In WPA3-Personal, the PMK is unique per session and derived using Simultaneous Authentication of Equals.
- C. In WPA3-Personal, the PMK is derived directly from the passphrase and is the same tor every session.
- D. In WPA3-Personal, the PMK is the same for each session and is communicated to clients that authenticate
Answer:
A
Question 7
What are the roles of 802.1X authenticators and authentication servers?
- A. The authenticator stores the user account database, while the server stores access policies.
- B. The authenticator supports only EAP, while the authentication server supports only RADIUS.
- C. The authenticator is a RADIUS client and the authentication server is a RADIUS server.
- D. The authenticator makes access decisions and the server communicates them to the supplicant.
Answer:
D
Question 8
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
- A. a client that has a certificate issued by a trusted Certification Authority (CA)
- B. a client that is not on the WIP blacklist
- C. a client that has successfully authenticated to an authorized AP and passed encrypted traffic
- D. a client that is on the WIP whitelist.
Answer:
C
Question 9
What is a guideline for creating certificate signing requests (CSRs) and deploying server Certificates
on ArubaOS Mobility Controllers (MCs)?
- A. Create the CSR online using the MC Web Ul if your company requires you to archive the private key.
- B. if you create the CSR and public/private Keypair offline, create a matching private key online on the MC.
- C. Create the CSR and public/private keypair offline If you want to install the same certificate on multiple MCs.
- D. Generate the private key online, but the public key and CSR offline, to install the same certificate on multiple MCs.
Answer:
A
Question 10
How should admins deal with vulnerabilities that they find in their systems?
- A. They should apply fixes, such as patches, to close the vulnerability before a hacker exploits it.
- B. They should add the vulnerability to their Common Vulnerabilities and Exposures (CVE).
- C. They should classify the vulnerability as malware. a DoS attack or a phishing attack.
- D. They should notify the security team as soon as possible that the network has already been breached.
Answer:
A
Question 11
A company has an ArubaOS controller-based solution with a WPA3-Enterprise WLAN. which
authenticates wireless clients to Aruba ClearPass Policy Manager (CPPM). The company has decided
to use digital certificates for authentication A user's Windows domain computer has had certificates
installed on it However, the Networks and Connections window shows that authentication has tailed
for the user. The Mobility Controllers (MC's) RADIUS events show that it is receiving Access-Rejects
for the authentication attempt.
What is one place that you can you look for deeper insight into why this authentication attempt is
failing?
- A. the reports generated by Aruba ClearPass Insight
- B. the RADIUS events within the CPPM Event Viewer
- C. the Alerts tab in the authentication record in CPPM Access Tracker
- D. the packets captured on the MC control plane destined to UDP 1812
Answer:
C
Question 12
Refer to the exhibit.
How can you use the thumbprint?
- A. Install this thumbprint on management stations to use as two-factor authentication along with manager usernames and passwords, this will ensure managers connect from valid stations
- B. Copy the thumbprint to other Aruba switches to establish a consistent SSH Key for all switches this will enable managers to connect to the switches securely with less effort
- C. When you first connect to the switch with SSH from a management station, make sure that the thumbprint matches to ensure that a man-in-t he-mid die (MITM) attack is not occurring
- D. install this thumbprint on management stations the stations can then authenticate with the thumbprint instead of admins having to enter usernames and passwords.
Answer:
C
Question 13
Your Aruba Mobility Master-based solution has detected a rogue AP Among other information the
ArubaOS Detected Radios page lists this Information for the AP
SSID = PubllcWiFI
BSSID = a8M27 12 34:56
Match method = Exact match
Match type = Eth-GW-wired-Mac-Table
The security team asks you to explain why this AP is classified as a rogue. What should you explain?
- A. The AP Is connected to your LAN because It is transmitting wireless traffic with your network's default gateway's MAC address as a source MAC Because it does not belong to the company, it is a rogue
- B. The ap has a BSSID mat matches authorized client MAC addresses. This indicates that the AP is spoofing the MAC address to gam unauthorized access to your company's wireless services, so It is a rogue
- C. The AP has been detected as launching a DoS attack against your company's default gateway. This qualities it as a rogue which needs to be contained with wireless association frames immediately
- D. The AP is spoofing a routers MAC address as its BSSID. This indicates mat, even though WIP cannot determine whether the AP is connected to your LAN. it is a rogue.
Answer:
D
Question 14
Refer to the exhibit.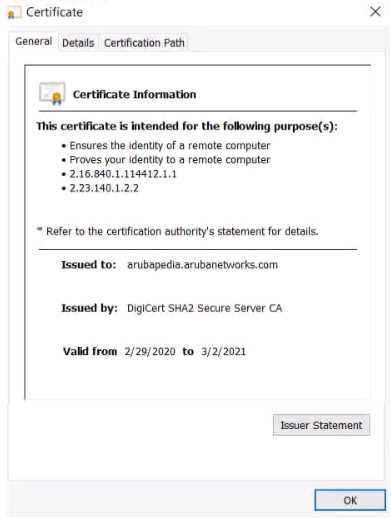
Device A is establishing an HTTPS session with the Arubapedia web sue using Chrome. The
Arubapedia web server sends the certificate shown in the exhibit
What does the browser do as part of vacating the web server certificate?
- A. It uses the public key in the DigCen SHA2 Secure Server CA certificate to check the certificate's signature.
- B. It uses the public key in the DigCert root CA certificate to check the certificate signature
- C. It uses the private key in the DigiCert SHA2 Secure Server CA to check the certificate's signature.
- D. It uses the private key in the Arubapedia web site's certificate to check that certificate's signature
Answer:
A
Question 15
A company is deploying ArubaOS-CX switches to support 135 employees, which will tunnel client
traffic to an Aruba Mobility Controller (MC) for the MC to apply firewall policies and deep packet
inspection (DPI). This MC will be dedicated to receiving traffic from the ArubaOS-CX switches.
What are the licensing requirements for the MC?
- A. one AP license per-switch
- B. one PEF license per-switch
- C. one PEF license per-switch. and one WCC license per-switch
- D. one AP license per-switch. and one PEF license per-switch
Answer:
D