HP hpe6-a82 practice test
Aruba Certified ClearPass Associate Exam
Last exam update: Mar 26 ,2025
Question 1
What is true regarding Posturing and Profiling?
- A. Both Posturing and Profiling describe the same thing, what is the health of the client endpoinst?
- B. Profiling describes categorizing the user based on their department while Posturing validates the user as authenticated
- C. Posturing and Profiling are role assignments in ClearPass used internally to map to enforcement policies.
- D. Profiling is the act of identifying the endpoint type while Posturing is assigning a status as to the health of the endpoint
Answer:
D
Question 2
Refer to the exhibit.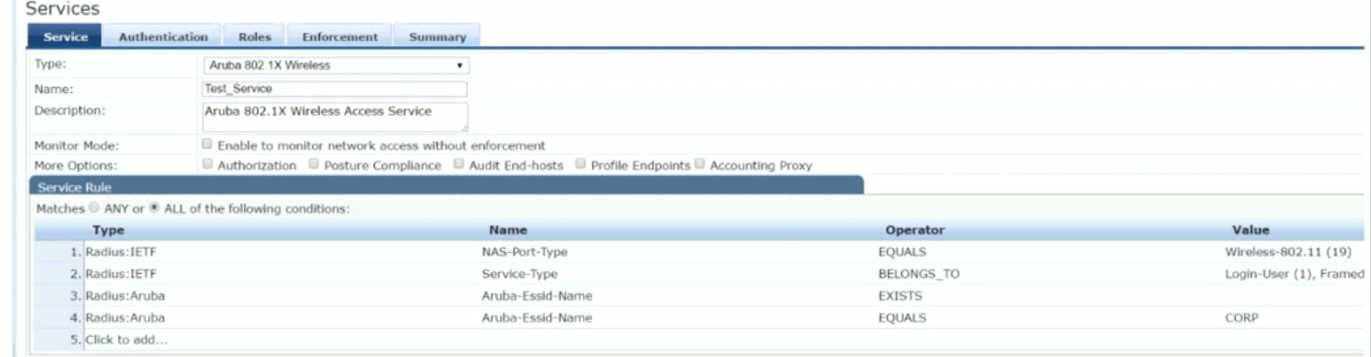
Which user authentication request will match the service rules of the Policy Service shown?
- A. a wireless user connection would fail because of miss-configured service rules
- B. a wireless user connected to any SSID named "CORP"
- C. a wireless user connecting to any SSID on an Aruba Controller
- D. a wireless user connecting to an Aruba IAP on the SSID "CORP"
Answer:
D
Question 3
What is the significance of using the [Allow ALL MAC AUTH] as an Authentication Method for Guests?
- A. This removes the reliance on the known or unknown status for MAC authentication.
- B. All clients with unknown endpoints will be granted guest access regardless of authorization
- C. Client attempts will fail without an additional Authentication method applied.
- D. All clients with known endpoints will be granted guest access regardless of authorization.
Answer:
A
Explanation:
https://www.arubanetworks.com/techdocs/Instant_83_WebHelp/Content/Instant_UG/
Authentication/AuthenticationMethods.htm
Question 4
What happens when a client successfully authenticates but does not match any Enforcement Policy
rules?
- A. A RADIUS Accept is returned and the default Enforcement Profile is applied.
- B. A RADIUS reject is returned for the client.
- C. A RADIUS Accept is retuned, and the default rule is applied to the device.
- D. A RADIUS Accept is returned with no Enforcement Profile applied
Answer:
A
Question 5
Which configuration options are necessary to add a Network Access Device into the ClearPass Policy
Manager? (Select two.)
- A. ClearPass Admin Password
- B. https certificate
- C. NAD IP Address
- D. Shared Secret
- E. CLI Console Password
Answer:
CD
Question 6
Which statement is true about OnGuard? (Select two.)
- A. It is used to identify and remove any malware/viruses
- B. It is used to ensure that Antivirus/Antispyware programs are running
- C. It supports Doth Windows and Mac OS X clients
- D. It only supports 802 1X authentication
Answer:
BC
Question 7
Which are valid enforcement profile types? (Select two)
- A. Policy Service Enforcement
- B. RADIUS Change of Authorization (CoA)
- C. Aruba Script Enforcement
- D. ClearPass Entity Update Enforcement
Answer:
BD
Question 8
Which ClearPass feature assesses endpoint context and client device type?
- A. Profiling
- B. Posture
- C. Captive Portal
- D. Onboard
Answer:
A
Explanation:
Reference:
https://www.arubanetworks.com/techdocs/ClearPass/6.7/Aruba_DeployGd_HTML/Content/About%
20ClearPass/About_ClearPass.htm
Question 9
Which must be taken into account if a customer wants to use the DHCP collector with 802.1X
authentication?
- A. Because DHCP fingerprinted is a Layer-3 function, it cannot t>e used with an 802 1X authentication service.
- B. The client needs to be granted limited access before the enforcement policy can take into account the device type
- C. When a client sends an authentication request to ClearPass, the profiler will also gather DHCP information
- D. The client needs to connect to an open network first to be profiled, then shifted to the secure 802.1x network.
Answer:
C
Question 10
When joining ClearPass to an Active Directory (AD) domain, what information is required? (Select
two.)
- A. ClearPass Policy Manager (CPPM) enterprise credentials.
- B. Domain Administrator credentials with at least read access
- C. Domain User credentials with read-write access
- D. Cache Timeout value set to at least 10 hours
- E. Fully Qualified Domain Name (FQDN) of the AD Domain Controller.
Answer:
BE
Question 11
What is a function of the posture token in ClearPass OnGuard? (Select two )
- A. Identifies clients that are not security compliant
- B. Initiates the Auto-Remediation process
- C. Controls access to network resources
- D. Denies access to unhealthy clients
- E. indicates the Health Status of the Client
Answer:
AE
Question 12
Which fingerprint collectors can help to distinguish between an iPhone and an iPad? (Select two.)
- A. IF-MAP
- B. MAC OUI
- C. HTTP
- D. TCP header capture
- E. SNMP
Answer:
AC
Explanation:
In some cases, DHCP fingerprinting alone cannot fully classify a device. A common example is the
Apple family of smart devices; for example, DHCP fingerprints cannot distinguish between an iPad
and an iPhone. In these scenarios, user-agent strings sent by browsers in the HTTP protocol are
useful to further refine classification results. User-agent strings are collected from the following:
ClearPass Guest ClearPass Onboard Aruba controller through an IF-MAP (Interface for Metadata
Access Points) interface
Question 13
What needs to be configured for ClearPass use an enforcement rule base on client Data Cap?
- A. Interim Accounting on the Network Access Device (NAD).
- B. Enable Active Sessions in ClearPass Guest
- C. Enable Logging of Accounting Start-Stop packets.
- D. Make sure the Endpoint Profiling is configured
Answer:
A
Question 14
A customer is setting up Guest access with ClearPass. They are considering using 802.1X for both the
Employee network and the Guest network. What are two issues the customer may encounter when
deploying 802.1X with the Guest network? (Select two)
- A. the lack of encryption during the authentication process
- B. ClearPass win not be able to enforce individual Access Control policies.
- C. the high level of complexity for users to join the guest network
- D. Guests will not be able to be uniquely identified.
- E. difficult to maintain in an environment with a large number of transient guest users
Answer:
CE
Question 15
DRAG DROP
Match the ClearPass system description to the best term Options are used only once.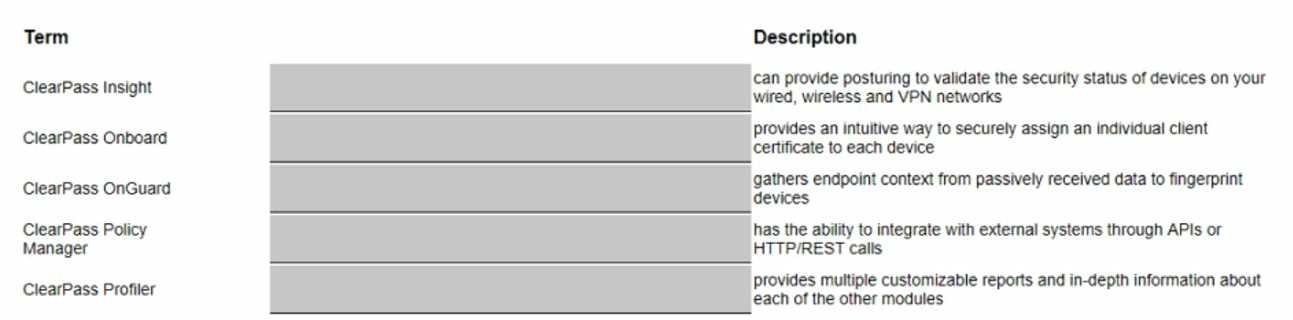
Answer:
None
Explanation:
The correct order is: OnGuard, OnBoard, Profiler, Policy Manager, Insight