Huawei h12-831-v1-0 practice test
HCIP-Datacom-Advanced Routing & Switching Technology V1.0 Exam
Last exam update: Mar 26 ,2025
Question 1
A company purchased private lines from two operators. In order to optimize the lines, the company
used the 6GP protocol to learn from two
Route entries that operate off. However, after the enterprise found that this configuration, the traffic
of the port route increased greatly, and the network engineering arrangement
After investigation, it was found that the traffic of the two operators was passed to each other
through the enterprise egress router. Therefore, the enterprise intends to use the routing strategy so
that the traffic of the packets of different carriers is no longer passed to each other. Is the
configuration in the following figure correct?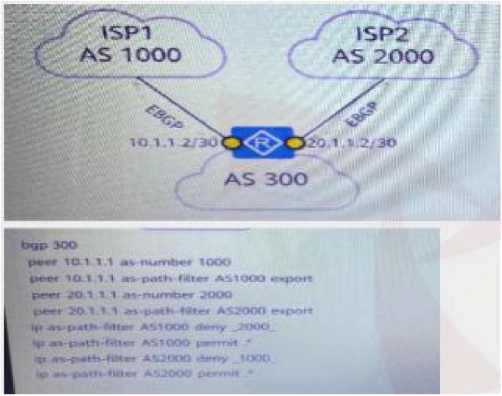
- A. True
- B. False
Answer:
A
Question 2
The routing policy tools that can be used by BGP mainly include Filterpolicy and oRoute-policy.
Fiterpolicy can only filter routes, Rote - policy can only modify routes
- A. True
- B. False
Answer:
B
Explanation:
Question 3
A campus deploys OSPF to implement network interworking. The LSDB of R2 is shown in the figure.
From this LSDB. it is possible to
What information was obtained?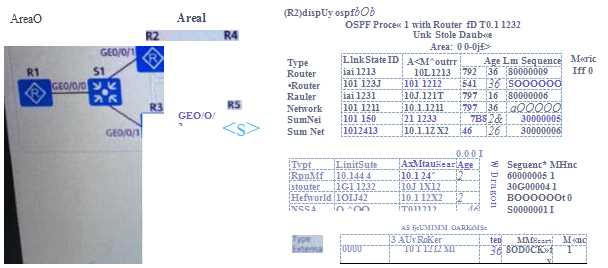
- A. ArealNone inType3 LSA. maybeR2in the area1In the correct directiontype3 LSAfiltered
- B. Area 1forNSSAarea
- C. R2WillType7 LSAThe default route is converted toType5 LSAdefault route for
- D. R2existOSPFThe default route is delivered in the process
Answer:
B, D
Question 4
Which of the following are static information coke analysis?
- A. Interface Type
- B. Packet loss rate
- C. License
- D. Equipment type
Answer:
A, C, D
Question 5
According to this diagram, can we break the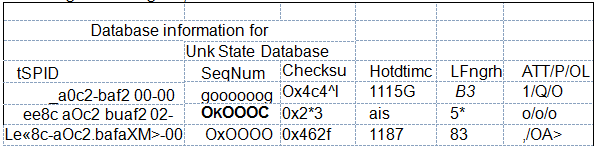
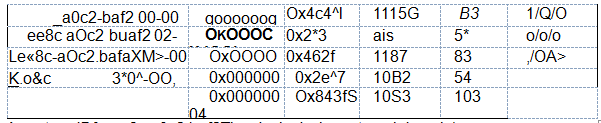
- A. system-IDforee8c.a0c2.baf2The device' whose type isLevel-1
- B. system-IDforee8c.a0c2.baf2device whose type isLevel-1-2
- C. R4belong only toLevel-1
- D. R4dry onlyLevel2
Answer:
B, C
Question 6
According to this picture, cooked I'] can be judged?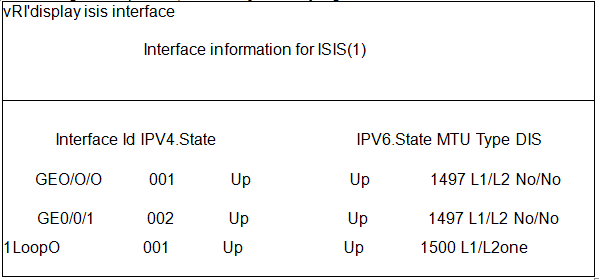
- A. R1ofGE0/0/1Interface is not enabledIS-IS IPv6
- B. R1ofGE0/0/1interfaceIS-ISThe interface type isLeve-1
- C. R1ofGEO/O/OinterfaceIS-ISThe interface type isLevel-1-2
- D. R1ofGEO/O/Ointerface is enabledIS-IS IPv6
Answer:
C, D
Question 7
Which of the following actions may affect the normal operation of the customer's network?
- A. Device naming
- B. software upgrade
- C. Hardware expansion
- D. Routing Protocol Configuration Changes
Answer:
B, C, D
Question 8
Which of the following information can the DHCP binding table contain?
- A. port andUDPport
- B. MA, Caddress
- C. IPaddress
- D. lease time
Answer:
B, C, D
Question 9
The Discovery message of LDP is used for neighbor discovery, and LDP has different discovery
mechanisms when discovering neighbors. The following statement about the Discovery message in
the basic discovery mechanism is correct
- A. TCPAfter the connection is establisheD. LSRdo not continue sendingHello Message
- B. Purpose of the messageIPaddress is multicastIPaddress224.0.0.2
- C. This message is encapsulated inUDPIn the message, the destination port number is646
- D. The message is sent to the specifiedLDP Peer
Answer:
B, C
Question 10
When troubleshooting a network, if you need to confirm the business traffic path, which of the
following may need to be done ()
- A. Confirm data link layer service traffic path
- B. Confirm the network layer service traffic path
- C. Investigate service traffic path planning in the network design phase
- D. Confirm the frequency of failure
Answer:
A, B, C
Question 11
As shown below: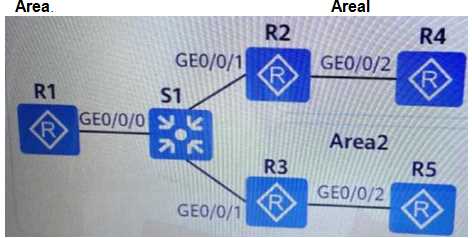
IR2] ad 2000
[R2-ad-basic-2000]rule deny
[R2-ad-basic-2000]quit
#
[R2] ospf
[R2-ospf1]area 1
[R2-ospM-area-0.0.0.1] filter 2000 import
[R2-ospf-1-area-0.0.0,1] quit
[R2-ospf-1] default-route-advertise always
- A. Area2containsType5LSAflood
- B. Area2no insideType3 LSAflood
- C. ArealcontainsType5 LSAflood
- D. Arealno insideType3 LSAflood
Answer:
D
Question 12
About the difference between NSR and NSF, which is correct?
- A. NSFCan be done without neighbor routers
- B. NSRMust rely on neighbor routers to complete
- C. NSFMust rely on neighbor routers to complete
- D. NSRandNSFBy6Requires neighbor router to complete
Answer:
C
Question 13
In the multi-level RR scenario, a large number of secondary RRs will be connected to the primary RR,
which may lead to BGP of the primary RR. The routing table overflows, what method can be used to
reduce the risk of overflowing the routing table of the advanced RR BGP?
- A. ORF
- B. route aggregation
- C. routing control
- D. set the sameCluster-ID
Answer:
B
Question 14
What fields are added in Update in order to advertise IPv6 routes in BGP4+.
- A. a new oneNLRITypes of"Pv6_NLR,which carryIPv6 NLRI prefix lengthandIPv6 NLRI prefix
- B. A new path attribute:MP_UNREA, CH_NLRI
- C. A new path attribute:MP_REA, CH_NLRI
- D. a new path attribute:IPv6_REA, CH_NLRI
Answer:
C
Question 15
When deploying MPLS/BGP IP VPN, which of the following descriptions is wrong about using BGP to
exchange routing information between PEs and CEs?
- A. existCEIn the case of multi-homing, enableBGP ASThe number substitution function may cause routing loops that can be passed throughBGP SoDpreventVPNIntra-site routing loops
- B. whenPEandCEbetweenBGPWhen exchanging routing information, if twoVPNThe autonomous system the site is in uses the same privateASnumber, can be passed throughASThe number replacement function is to use any specifiedASreplace the received private network route with theASnumber to preventASRoutes are discarded due to duplicate numbers C. existHub&Spokescene, whenHub-CEandHub-PEuseIGPTimeSpoke-PEandSpake-CEcannot makeEBGP
- D. whenPEandCEbetweenBGPWhen exchanging routing information, you do not need toPEPerform private network route import on theBGPoperation
Answer:
B