Juniper jn0-105 practice test
junos, associate (jncia-junos)
Last exam update: Mar 26 ,2025
Question 1
What will the request system configuration rescue save command do?
- A. It saves the candidate configuration as the rescue configuration.
- B. It saves the most recently committed configuration as the rescue configuration.
- C. It saves a configuration version prior to the configuration most recently committed as the rescue configuration.
- D. It activates the rescue configuration.
Answer:
b
Question 2
What is the maximum number of rollback configuration files that the Junos OS will store?
- A. 25
- B. 65
- C. 50
- D. 19
Answer:
c
Question 3
You configured your system authentication order using the set authentication-order tacplus radius password command.
Which statement is correct in this scenario?
- A. A rejection by TACACS+ will prevent a login and bypass the other two authentication methods.
- B. The password authentication will only be used if the TACACS+ and RADIUS servers fail to respond.
- C. All authentication methods are used with the most restrictive permission set used.
- D. The password authentication method is evaluated if the TACACS+ and RADIUS servers respond with a reject message.
Answer:
c
Question 4
Which two statements are correct regarding Layer 2 network switches? (Choose two.)
- A. Switches flood broadcast traffic.
- B. Switches are susceptible to traffic loops.
- C. Switches do not learn MAC addresses.
- D. Switches create a single collision domain.
Answer:
ad
Question 5
What are two attributes of the UDP protocol? (Choose two.)
- A. UDP is best effort.
- B. UDP is always slower than TCP.
- C. UDP is connectionless.
- D. UDP is more reliable than TCP.
Answer:
ac
Question 6
Which two fields are you required to enter when you create a new user account? (Choose two.)
- A. login class
- B. username
- C. user ID
- D. full name
Answer:
bd
Question 7
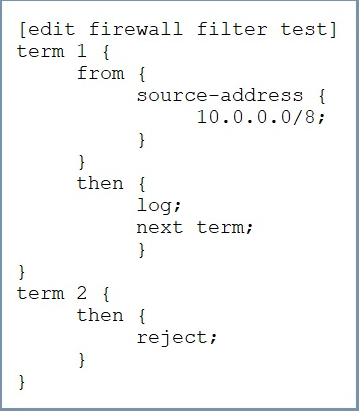
Click the Exhibit button.
How is traffic, sourced from 10.0.0.0/8, treated by the firewall filter shown in the exhibit?
- A. logged with no further action
- B. logged and accepted
- C. logged and rejected
- D. logged and discarded
Answer:
d
Question 8
Click the Exhibit button.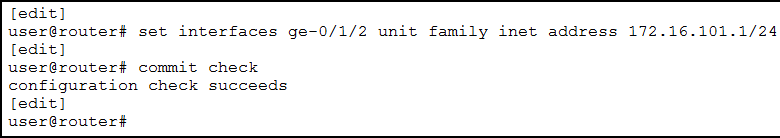
You need to configure interface ge-0/1/2 with an IP address of 172.16.100.1/24. You have accidentally entered 172.16.101.1/24 as shown in the exhibit.
Which command should you issue to solve the problem?
- A. [edit]user@router# rollback rescue
- B. [edit]user@router# rollback 1
- C. [edit]user@router# rollback 0
- D. [edit]user@router# rollback 2
Answer:
c
Question 9
Which two statements describe the result when you enter ? at the command-line prompt? (Choose two.)
- A. It displays help about a text string contained in a statement.
- B. It lists the available commands and options.
- C. It displays summary information about the commands and options.
- D. It lists tips for the help menu.
Answer:
ab
Question 10
Which two statements are correct about MAC addresses? (Choose two.)
- A. Switches use the Address Resolution Protocol table to assign MAC addresses to network interface cards in the forwarding frame.
- B. Switches use the destination MAC address to identify the next-hop destination and to change the destination MAC address in the frame.
- C. The source and destination MAC addresses always remains static to the final destination.
- D. The MAC address identifies the physical hardware.
Answer:
bd