Juniper jn0-231 practice test
security, associate (jncia-sec)
Last exam update: Mar 26 ,2025
Question 1
Which two services does Juniper Connected Security provide? (Choose two.)
- A. protection against zero-day threats
- B. IPsec VPNs
- C. Layer 2 VPN tunnels
- D. inline malware blocking
Answer:
ad
Question 2
What are two characteristics of a null zone? (Choose two.)
- A. The null zone is configured by the super user.
- B. By default, all unassigned interfaces are placed in the null zone.
- C. All ingress and egress traffic on an interface in a null zone is permitted.
- D. When an interface is deleted from a zone, it is assigned back to the null zone.
Answer:
bd
Question 3
Which two statements are correct about the default behavior on SRX Series devices? (Choose two.)
- A. The SRX Series device is in flow mode.
- B. The SRX Series device supports stateless firewalls filters.
- C. The SRX Series device is in packet mode.
- D. The SRX Series device does not support stateless firewall filters.
Answer:
ab
Question 4
The UTM features are performed during which process of the SRX Series devices packet flow?
- A. security policies
- B. services
- C. zones
- D. screens
Answer:
a
Question 5
Which two statements are correct about IPsec security associations? (Choose two.)
- A. IPsec security associations are bidirectional.
- B. IPsec security associations are unidirectional.
- C. IPsec security associations are established during IKE Phase 1 negotiations.
- D. IPsec security associations are established during IKE Phase 2 negotiations.
Answer:
ac
Question 6
Which two user authentication methods are supported when using a Juniper Secure Connect VPN? (Choose two.)
- A. certificate-based
- B. multi-factor authentication
- C. local authentication
- D. active directory
Answer:
ac
Question 7
Which two statements are correct about IKE security associations? (Choose two.)
- A. IKE security associations are established during IKE Phase 1 negotiations.
- B. IKE security associations are unidirectional.
- C. IKE security associations are established during IKE Phase 2 negotiations.
- D. IKE security associations are bidirectional.
Answer:
ad
Question 8
Which statement is correct about static NAT?
- A. Static NAT supports port translation.
- B. Static NAT rules are evaluated after source NAT rules.
- C. Static NAT implements unidirectional one-to-one mappings.
- D. Static NAT implements unidirectional one-to-many mappings.
Answer:
c
Question 9
Corporate security requests that you implement a policy to block all POP3 traffic from traversing the Internet firewall.
In this scenario, which security feature would you use to satisfy this request?
- A. antivirus
- B. Web filtering
- C. content filtering
- D. antispam
Answer:
c
Question 10
Click the Exhibit button.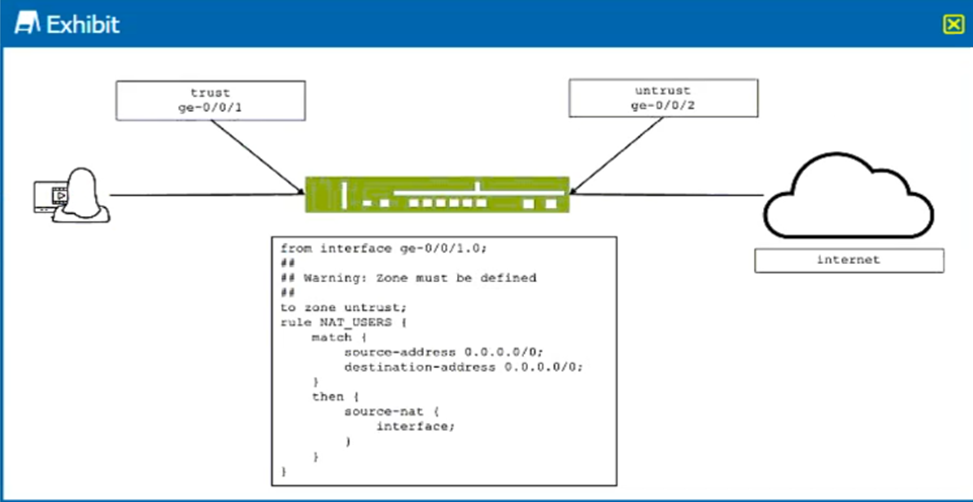
You are configuring an SRX firewall to NAT user traffic to the Internet.
Referring to the exhibit, which configuration change will enable the NAT policy?
- A. delete security nat source rule-set NAT_USERS to zone
- B. set security nat source rule-set NAT_USERS from zone NAT
- C. set security zones security-zone untrust interfaces ge-0/0/2.0
- D. delete security zone security-zone untrust interfaces ge-0/0/1.0
Answer:
c