Juniper jn0-334 practice test
Security, Specialist Exam
Last exam update: Mar 26 ,2025
Question 1
Which default protocol and port are used for JIMS to SRX client communication?
- A. WMI over TCP; port 389
- B. ADSI over TCP; port 389
- C. HTTPS over TCP: port 443
- D. RPC over TCP, port 135
Answer:
C
Reference:
https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-
certificate-configuring.html#:~:text=By%20default%2C%20the%20HTTPS%20port%20is%20443.&text=The%20JI
MS% 20server%20communicates%20with,Firewall%20to%20allow%20this%20communication
Question 2
Click the Exhibit button.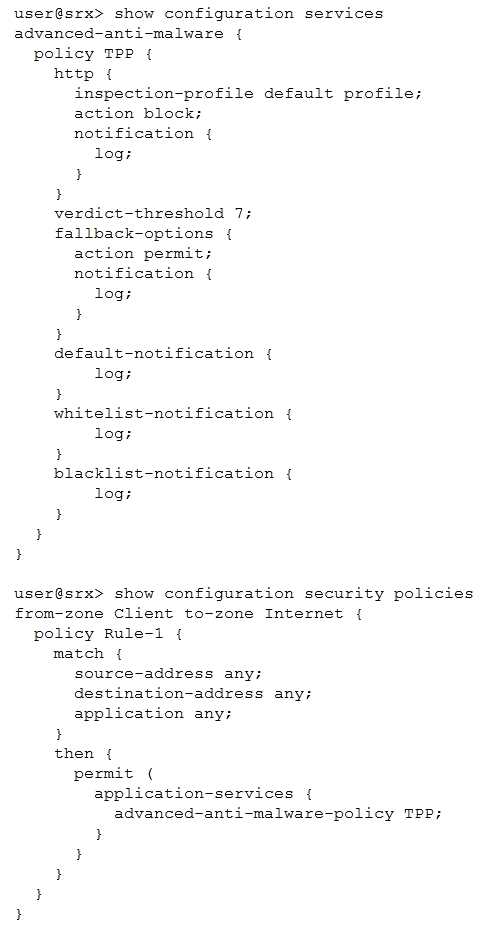
You have deployed Sky ATP to protect your network from attacks so that users are unable to
download malicious files. However, after a user attempts to download a malicious file, they are still
able to communicate through the SRX Series device.
Referring to the exhibit, which statement is correct?
- A. Change the security policy from a standard security policy to a unified security policy.
- B. Remove the fallback options in the advanced anti-malware policy.
- C. Configure a security intelligence policy and apply it to the security policy.
- D. Lower the verdict threshold in the advanced anti-malware policy.
Answer:
C
Question 3
Which two statements apply to policy scheduling? (Choose two.)
- A. A policy refers to many schedules.
- B. A policy refers to one schedule.
- C. Multiple policies can refer to the same schedule.
- D. A policy stays active regardless of when the schedule is active.
Answer:
BC
Reference:
https://www.juniper.net/documentation/en_US/cso5.4.0/topics/concept/cp-about-schedule-overview.html
Question 4
Click the Exhibit button.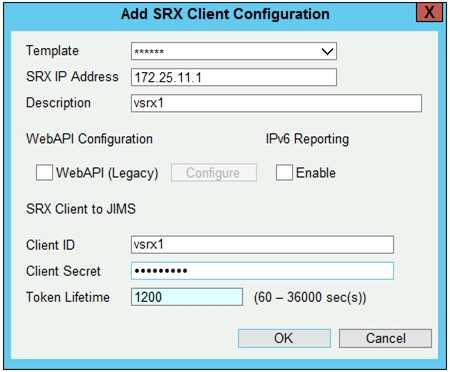
Referring to the exhibit, which two values in the JIMS SRX client configuration must match the values
configured on the SRX client? (Choose two.)
- A. IPv6 Reporting
- B. Client ID
- C. Client Secret
- D. Token Lifetime
Answer:
BC
Reference:
https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-srx-configuring.html
Question 5
Which two statements describe SSL proxy on SRX Series devices? (Choose two.)
- A. SSL proxy supports TLS version 1.2.
- B. Client-protection is also known as reverse proxy.
- C. SSL proxy is supported when enabled within logical systems.
- D. SSL proxy relies on Active Directory to provide secure communication.
Answer:
AC
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-ssl-tls.html
Question 6
You are troubleshooting advanced policy-based routing (APBR).
Which two actions should you perform in this scenario? (Choose two.)
- A. Verify that the APBR profiles are applied to the egress zone.
- B. Verity inet.0 for correct route leaking.
- C. Review the APBR statistics for matching rules and route modifications.
- D. Inspect the application system cache for the application entry.
Answer:
CD
Question 7
When working with network events on a Juniper Secure Analytics device, flow records come from
which source?
- A. tap port
- B. SPAN
- C. switch
- D. mirror
Answer:
B
Reference:
https://www.juniper.net/documentation/en_US/jsa7.3.1/jsa-arch-deployment-guide/topics/concept/jsa-ad-jsa-events-and-flows.html
Question 8
You are deploying a vSRX into a vSphere environment which applies the configuration from a
bootable ISO file containing the juniper.conf file. After the vSRX boots and has the configuration
applied, you make additional device specific configuration changes, commit, and reboot the device.
Once the device finishes rebooting, you notice the specific changes you made are missing but the
original configuration is applied.
In this scenario, what is the problem?
- A. Configuration changes do not persist after reboots on vSRX.
- B. The juniper.conf file was not applied to the vSRX.
- C. The configuration file is corrupt.
- D. The ISO file is still mounted on the vSRX.
Answer:
D
Reference:
https://www.juniper.net/documentation/us/en/software/vsrx/vsrx-kvm/topics/task/security-vsrx-kvm-bootstrap-config.html
Question 9
Which three statements are true about the difference between cSRX-based virtual security
deployments and vSRX-based virtual security deployments? (Choose three.)
- A. vSRX provides Layer 2 to Layer 7 secure services and cSRX provides Layer 4 to Layer 7 secure services.
- B. cSRX requires less storage and memory space for a given deployment than vSRX-based solutions.
- C. cSRX-based solutions are more scalable than vSRX-based solutions.
- D. vSRX and cSRX both provide Layer 2 to Layer 7 secure services.
- E. vSRX provides faster deployment time and faster reboots compared to cSRX.
Answer:
ABC
Reference:
https://www.juniper.net/documentation/en_US/day-one-books/topics/concept/juniper-vsrx-versus-csrx.html
Question 10
Which two statements describe superflows in Juniper Secure Analytics? (Choose two.)
- A. JSA only supports Type A and Type C superflows.
- B. Superflows can negatively impact licensing limitations.
- C. Disk space usage is reduced on the JSA device.
- D. Superflows combine many flows into a single flow.
Answer:
CD
Question 11
Click the Exhibit button.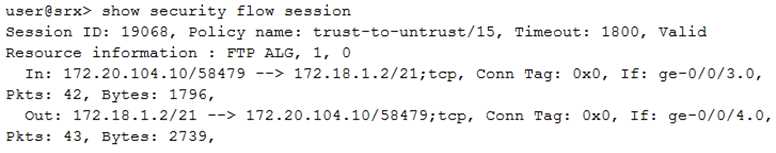
Which two statements are true about the session shown in the exhibit? (Choose two.)
- A. Two security policies are required for bidirectional traffic flow.
- B. The ALG was enabled by manual configuration.
- C. The ALG was enabled by default.
- D. One security policy is required for bidirectional traffic flow.
Answer:
AB
Question 12
After performing a software upgrade on an SRX5800 chassis cluster, you notice that node1 is in the
primary state and node0 is in the backup state. Your network standards dictate that node0 should be
in the primary state.
In this scenario, which command should be used to comply with the network standards?
- A. request chassis cluster failover redundancy-group 254 node 1
- B. request chassis cluster failover redundancy-group 0 node 0
- C. request chassis cluster failover redundancy-group 254 mode 0
- D. request chassis cluster failover redundancy-group 0 node 1
Answer:
B
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-redundancy-group-failover.html
Question 13
Click the Exhibit button.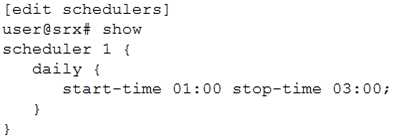
You have configured the scheduler shown in the exhibit to prevent users from accessing certain
websites from 1:00 PM to 3:00 PM Monday through Friday. This policy will remain in place until
further notice. When testing the policy, you determine that the websites are still accessible during
the restricted times.
In this scenario, which two actions should you perform to solve the problem? (Choose two.)
- A. Add the saturday exclude parameter and the sunday exclude parameter to ensure weekends are excluded from the schedule.
- B. Use the 13:00 parameter and the 15:00 parameter when specifying the time.
- C. Use the start-date parameter to specify the date for each Monday and use the stop-date parameter to specify the date for each Friday.
- D. Use the PM parameter when specifying the time in the schedule.
Answer:
AB
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/schedulers-edit-scheduler.html
Question 14
Click the Exhibit button.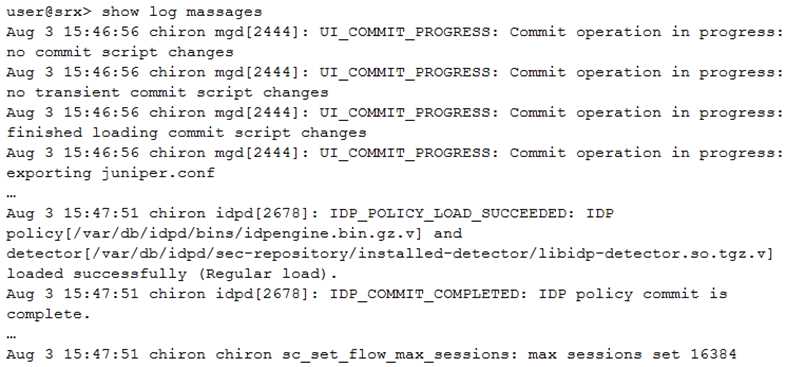
You examine the log file shown in the exhibit after running the set security idp active-policy
command.
Which two statements are true in this scenario? (Choose two.)
- A. The IDP policy compiled successfully.
- B. The IDP policy loaded successfully.
- C. The IDP hit cache is set to 16384.
- D. The entire configuration was committed.
Answer:
AB
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-idp-policies-overview.html
Question 15
Which two session parameters would be used to manage space on the session table? (Choose two.)
- A. low watermark
- B. high watermark
- C. TCP MSS
- D. TCP RST
Answer:
AB
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-flow-based-session-for-srx-series-devices.html