Juniper jn0-635 practice test
Security, Professional Exam
Last exam update: Mar 26 ,2025
Question 1
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
- A. The collector must have a minimum of two interfaces.
- B. The collector must have a minimum of three interfaces.
- C. The collector must have a minimum of five interfaces.
- D. The collector must have a minimum of four interfaces.
Answer:
D
Explanation:
https://www.juniper.net/documentation/en_US/release-independent/jatp/topics/task/configuration/jatp-traffic-collectorsetting-ssh-honeypot-detection.html
Question 2
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static
NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement
DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario?
(Choose two.)
- A. The DNS doctoring ALG is not enabled by default.
- B. The Proxy ARP feature must be configured.
- C. The DNS doctoring ALG is enabled by default.
- D. The DNS CNAME record is translated.
Answer:
B, C
Question 3
The monitor traffic interface command is being used to capture the packets destined to and the from
the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
- A. This feature does not capture transit traffic.
- B. This feature captures ICMP traffic to and from the SRX Series device.
- C. This feature is supported on high-end SRX Series devices only.
- D. This feature is supported on both branch and high-end SRX Series devices.
Answer:
A, D
Explanation:
https://forums.juniper.net/t5/Ethernet-Switching/monitor-traffic-interface/td-p/462528
Question 4
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access
to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request?
(Choose three.)
- A. Enable JTAC remote access
- B. Create a temporary root account.
- C. Enable a JATP support account.
- D. Create a temporary admin account.
- E. Enable remote support.
Answer:
C, D,E
Explanation:
https://kb.juniper.net/InfoCenter/index?page=content&id=TN326&cat=&actp=LIST&showDraft=false
Question 5
Exhibit.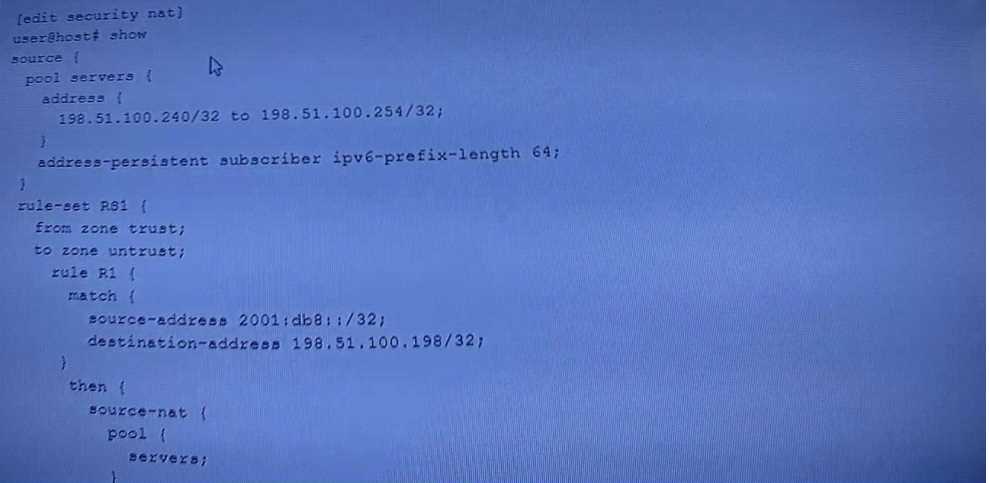
Referring to the exhibit, which two statements are true? (Choose two.)
- A. The configured solution allows IPv6 to IPv4 translation.
- B. The configured solution allows IPv4 to IPv6 translation.
- C. The IPv6 address is invalid.
- D. External hosts cannot initiate contact.
Answer:
A, C
Question 6
According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
- A. Mismatched proxy ID
- B. Mismatched peer ID
- C. Mismatched preshared key
- D. Incorrect peer address.
Answer:
B
Explanation:
https://www.juniper.net/documentation/en_US/release-independent/nce/topics/example/policy-based-vpn-using-j-series-srxseries-device-configuring.html
Question 7
Your organization has multiple Active Directory domain to control user access. You must ensure that
security polices are passing traffic based upon the users access rights.
What would you use to assist your SRX series devices to accomplish this task?
- A. JIMS
- B. Junos Space
- C. JSA
- D. JATP Appliance
Answer:
A
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-configure-jims.html
Question 8
Exhibit.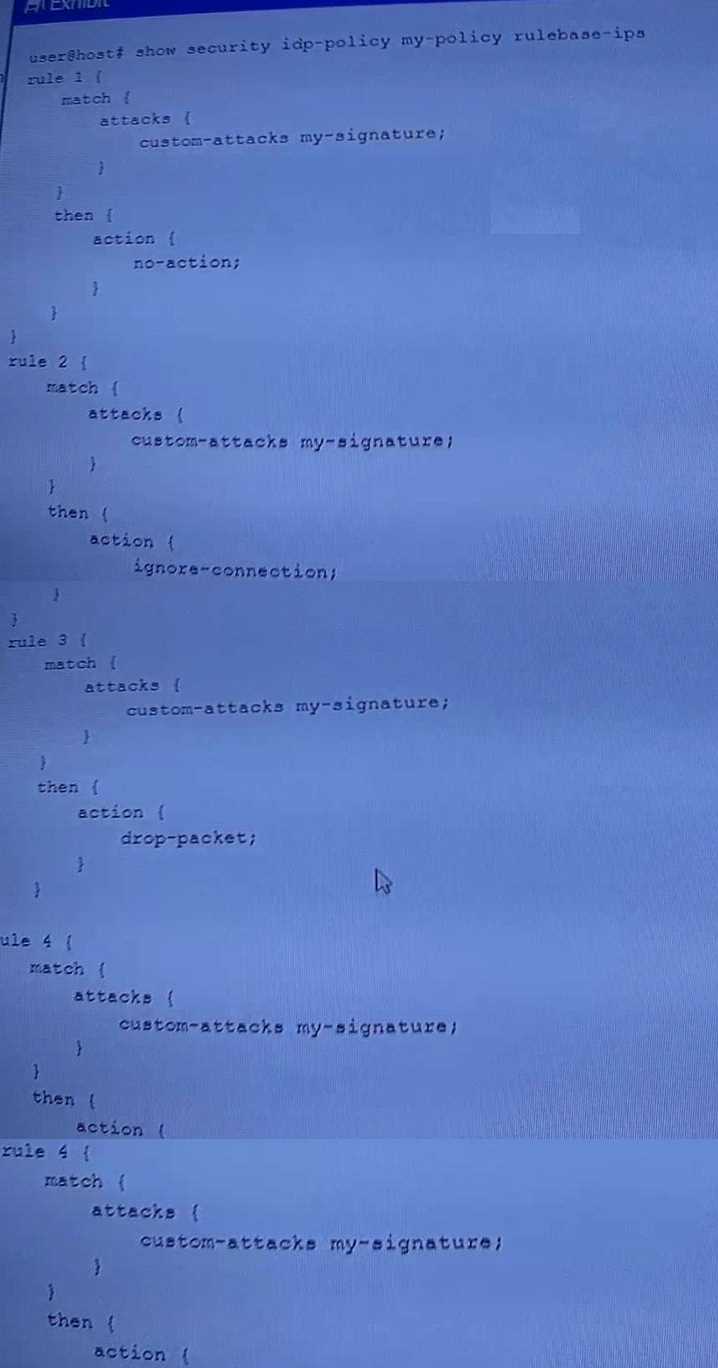
A hub member of an ADVPN is not functioning correctly.
Referring the exhibit, which action should you take to solve the problem?
- A. [edit interfaces] root@vSRX-1# delete st0.0 multipoint
- B. [edit interfaces] user@hub-1# delete ipsec vpn advpn-vpn traffic-selector
- C. [edit security] user@hub-1# set ike gateway advpn-gateway advpn suggester disable
- D. [edit security] user@hub-1# delete ike gateway advpn-gateway advpn partner
Answer:
B
Question 9
Which two log format types are supported by the JATP appliance? (Choose two.)
- A. YAML
- B. XML
- C. CSV
- D. YANG
Answer:
B, C
Explanation:
https://www.juniper.net/documentation/en_US/release-independent/jatp/topics/topic-map/jatp-custom-log-ingestion.html
Question 10
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You
are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
- A. Network
- B. Signature
- C. Protocol anomaly
- D. host
Answer:
B, C
Question 11
You have designed the firewall filter shown in the exhibit to limit SSH control traffic to yours SRX
Series device without affecting other traffic.
Which two statement are true in this scenario? (Choose two.)
- A. The filter should be applied as an output filter on the loopback interface.
- B. Applying the filter will achieve the desired result.
- C. Applying the filter will not achieve the desired result.
- D. The filter should be applied as an input filter on the loopback interface.
Answer:
C, D
Explanation:
https://www.juniper.net/documentation//en_US/junos/topics/concept/firewall-filter-ex-series-evaluation-understanding.html
Question 12
You issue the command shown in the exhibit.
Which policy will be active for the identified traffic?
- A. Policy p4
- B. Policy p7
- C. Policy p1
- D. Policy p12
Answer:
B
Question 13
Which two additional configuration actions are necessary for the third-party feed shown in the
exhibit to work properly? (Choose two.)
- A. You must create a dynamic address entry with the IP filter category and the ipfilter_office365 value.
- B. You must create a dynamic address entry with the C&C category and the cc_offic365 value.
- C. You must apply the dynamic address entry in a security policy.
- D. You must apply the dynamic address entry in a security intelligence policy.
Answer:
A, C
Question 14
Click the Exhibit button.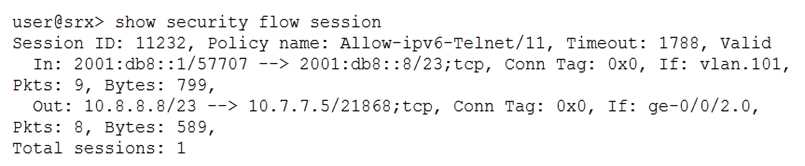
Which type of NAT is shown in the exhibit?
- A. NAT46
- B. NAT64
- C. persistent NAT
- D. DS-Lite
Answer:
B
Question 15
Click the Exhibit button.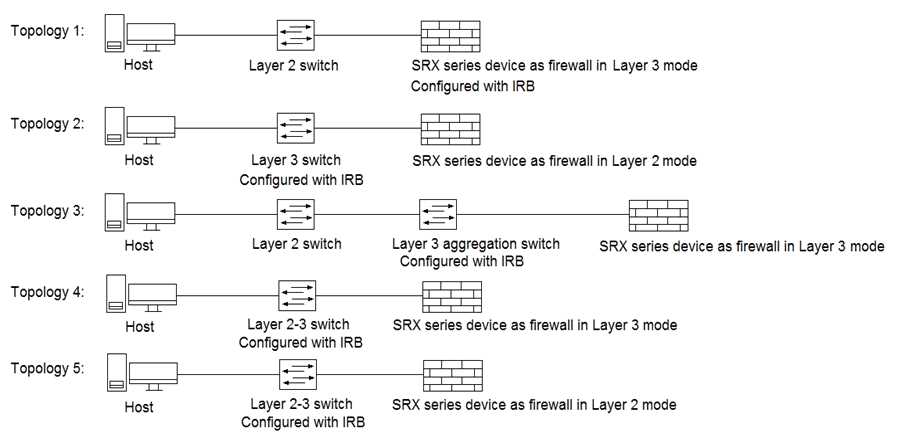
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
- A. Topology 3
- B. Topology 5
- C. Topology 2
- D. Topology 4
- E. Topology 1
Answer:
ADE
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos-space17.2/policy-enforcer/topics/concept/policy-enforcer-deployment-supported-topologies.html