Juniper jn0-649 practice test
enterprise routing and switching, professional (jncip-ent)
Last exam update: Mar 26 ,2025
Question 1
Click the Exhibit button.
Referring to the exhibit, a PIM-SM network is set up to enable communication between multicast devices.
Which two statements are true? (Choose two.)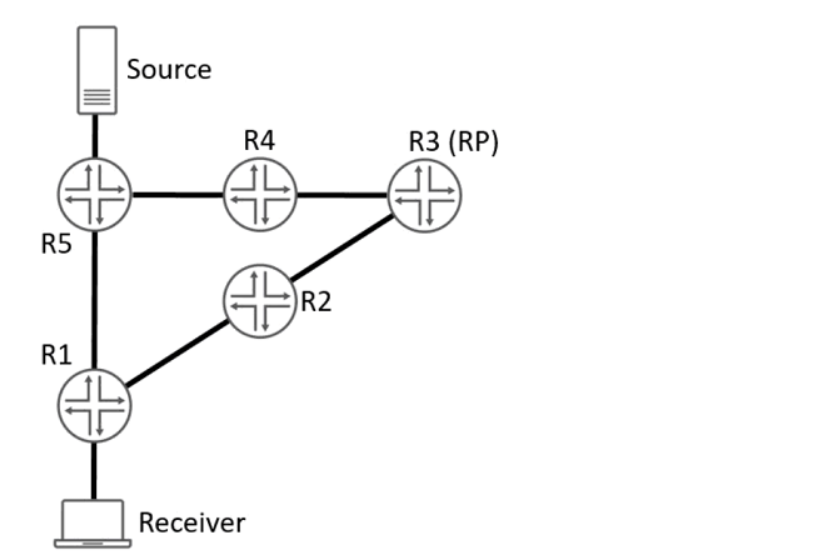
- A. Before the formation of the rendezvous-point tree, a join message is sent from R1 to R3.
- B. Before the formation of the rendezvous-point tree, an IGMP is sent from the Receiver to R1.
- C. Before the formation of the rendezvous-point tree, an IGMP is sent from the Source to R5.
- D. Before the formation of the rendezvous-point tree, a join message is sent from R1 to R5.
Answer:
bc
Question 2
Click the Exhibit button.
You recently committed a change to a router to reject OSPF routes sourced from area 10. However, you are still seeing area 10 routes in the routing table.
Referring to the exhibit, which statement is correct?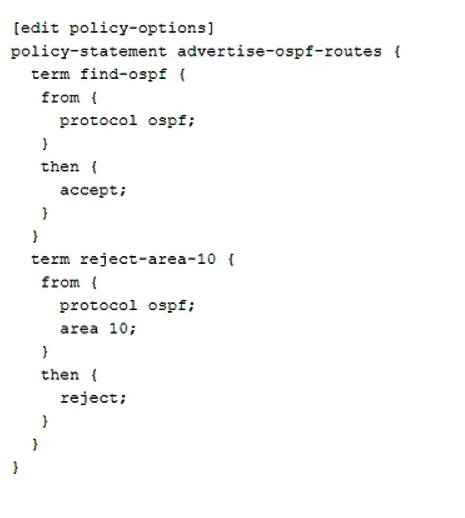
- A. The OSPF protocol is first matched by find-ospf and accepted.
- B. The routes only timeout after 24 hours.
- C. The routes remain in the table until the device is rebooted.
- D. The routes remain in the table until the routing daemon is restarted.
Answer:
d
Question 3
Click the Exhibition button.
You are asked to troubleshoot voice quality issues on your newly implement VoIP network. You notice that the voice packets are being dropped. You have verified that the packets are correctly marked for expedited forwarding queue.
Referring to the exhibit, what must you configure to solve the problem?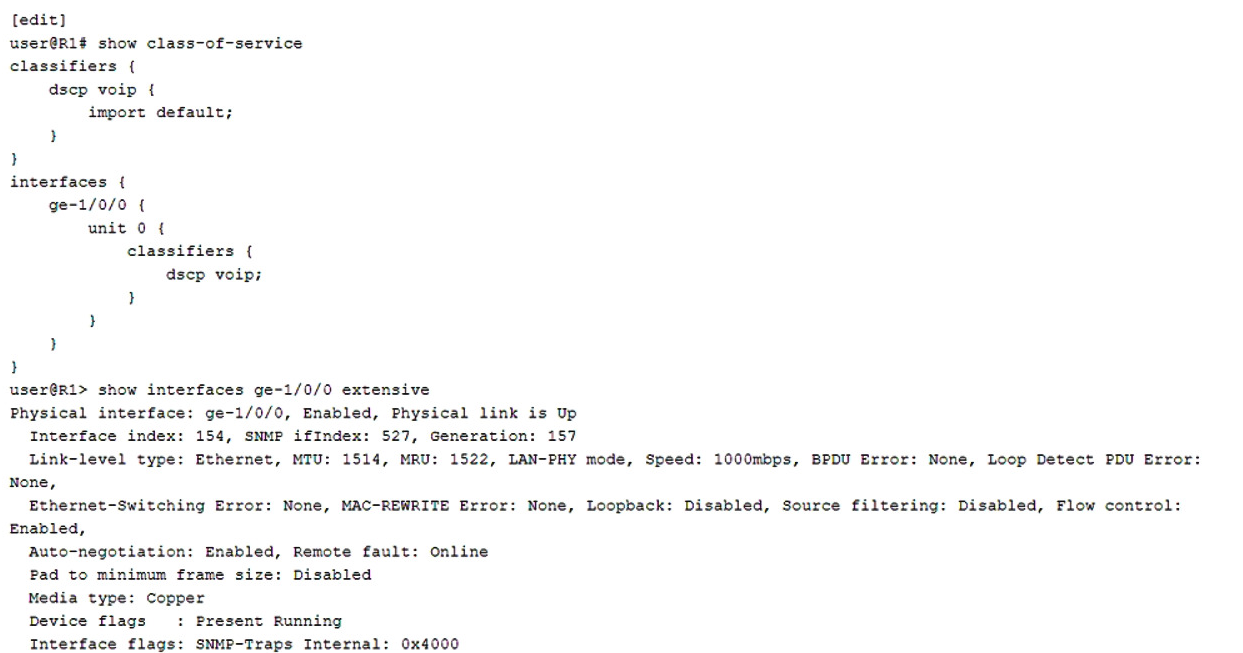
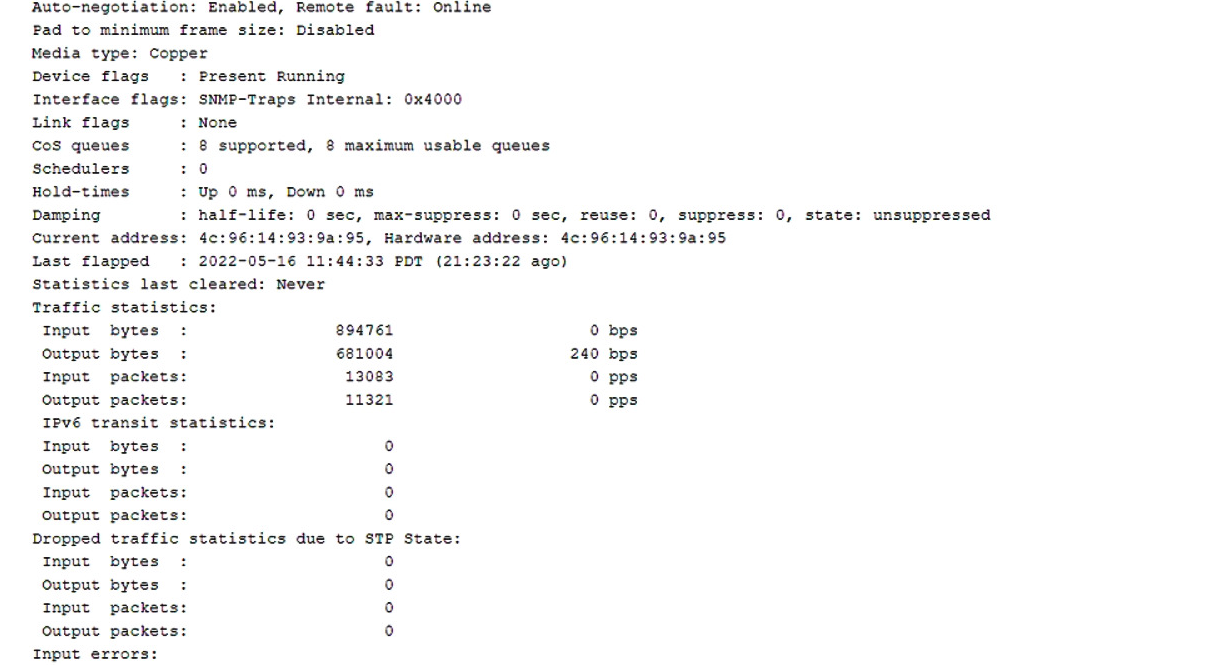
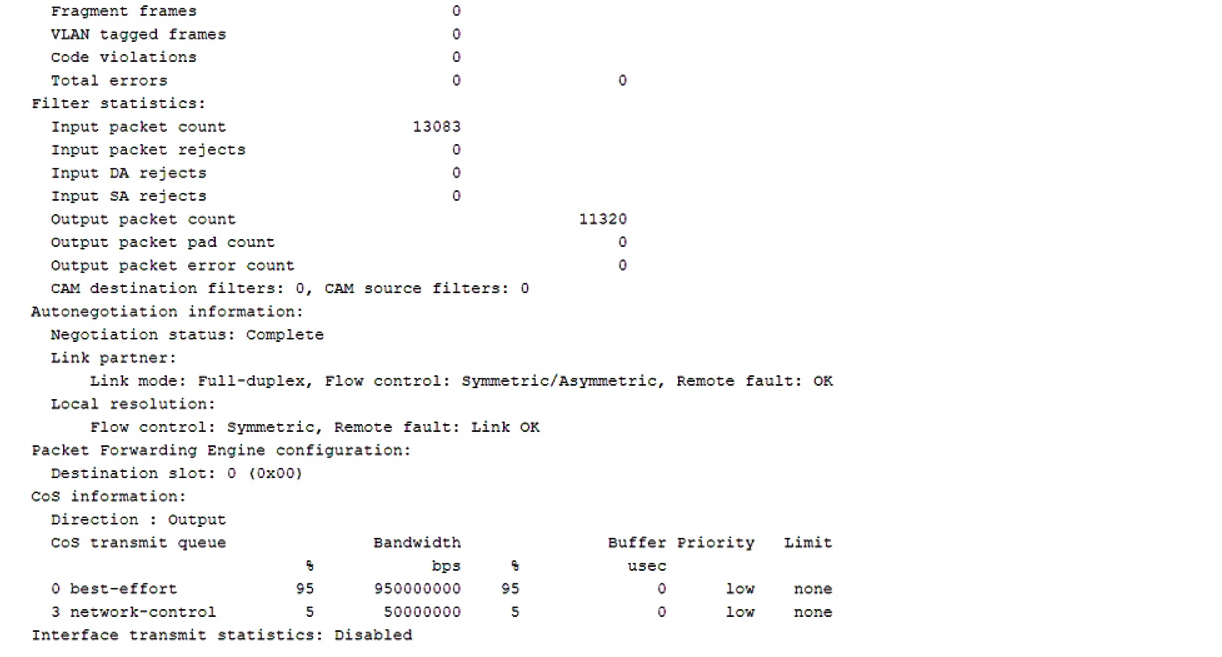
- A. You must configure a multifield classifier to put the VoIP traffic in the correct queue.
- B. You must configure a rewrite rule to ensure that the traffic is scheduled properly in the device.
- C. You must configure a scheduler to allocate bandwidth to the expedited forwarding queue.
- D. You must configure a policer to ensure that the queue is not being starved.
Answer:
c
Question 4
Which two statements are correct about the deployment of EVPN-VXLAN on QFX Series devices? (Choose two.)
- A. Type 1 route advertisements always have the single-active flag set to 1.
- B. Junos OS supports underlay replication for BUM traffic forwarding.
- C. Junos OS supports ingress replication for BUM traffic forwarding.
- D. Type 1 route advertisements always have the single-active flag set to 0.
Answer:
bc
Question 5
Click the Exhibit button.
Referring to the outputs shown in the exhibit, which two statements are correct about the IS-IS adjacency? (Choose two.)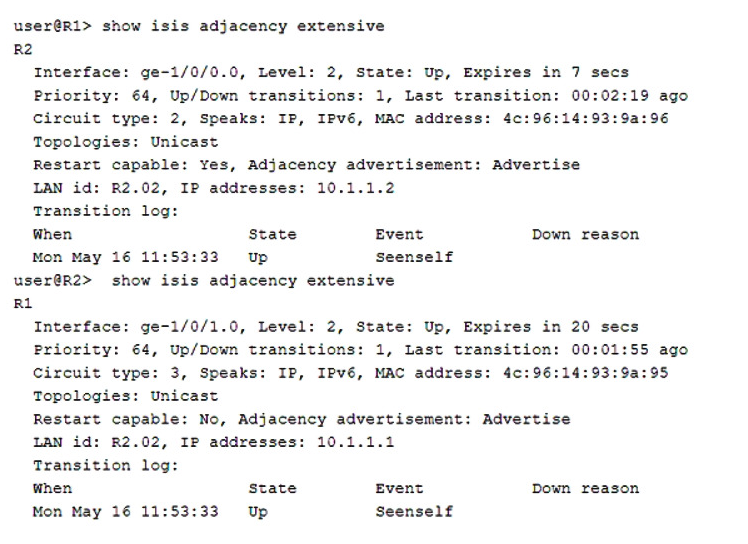
- A. R1 is configured to participate in both Level 1 and Level 2.
- B. R2 is configured to participate in both Level 1 and Level 2.
- C. R1 is configured to participate in Level 2 only.
- D. R2 is configured to participate in Level 2 only.
Answer:
bc
Question 6
You enable the Multiple VLAN Registration Protocol (MVRP) to automate the creation and management of virtual LANs.
Which statement is correct in this scenario?
- A. The forbidden mode does not register or declare VLANs.
- B. When enabled, MVRP affects all interfaces.
- C. Timers dictate when link state changes are propagated.
- D. MVRP works with RSTP and VSTP.
Answer:
b
Question 7
Click the Exhibit button.
Referring to the exhibit, you have placed the cos multifield classifier on all edge interfaces and configured the relevant CoS parameters.
In this scenario, which two statements are correct? (Choose two.)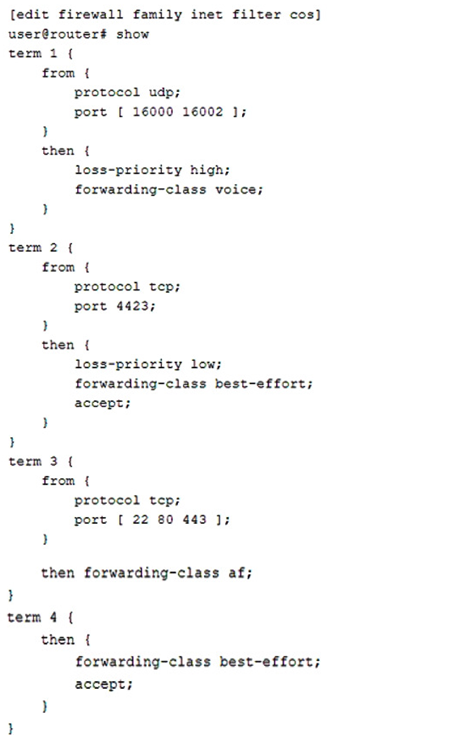
- A. SSH traffic using the default port will be placed in the af forwarding class and accepted.
- B. SSH traffic using the default port will be placed in the best-effort forwarding class and accepted.
- C. UDP traffic using the 16000 port will be placed in the voice forwarding class and accepted.
- D. UDP traffic using the 16000 port will be placed in the best-effort forwarding class and accepted.
Answer:
ac
Question 8
Click the Exhibit button.
Remote branches connect to the corporate WAN through access switches. The access switches connect to access ports on the WAN distribution switch, as shown in the exhibit. L2PT has previously been configured on the tunnel Layer 2 traffic across the WAN. You decide to move the L2PT tunnel endpoints to the access switches. When you apply the L2PT configuration to the access switches, the ports that connect the access switches to the distribution switch shut down.
Which action would solve this problem?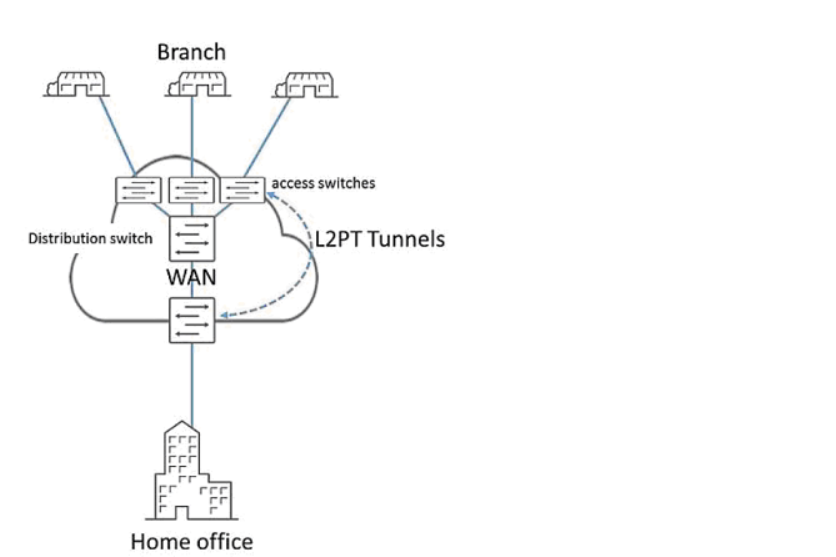
- A. Configure the links between the access switches and the distribution switch as a trunk port.
- B. Disable the BPDU block function on the access switches.
- C. Disable the BPDU block function on the distribution switch.
- D. Configure a GRE tunnel to encapsulate the L2PT traffic across the WAN.
Answer:
a
Question 9
Click the Exhibition button.
Referring to the exhibit, ServerA sends a single IP packet destined to 10.0.0.127.
Which two statements correctly describe the behavior of the resulting outbound VXLAN packets that contain the original packet destined to 10.0.0.127? (Choose two.)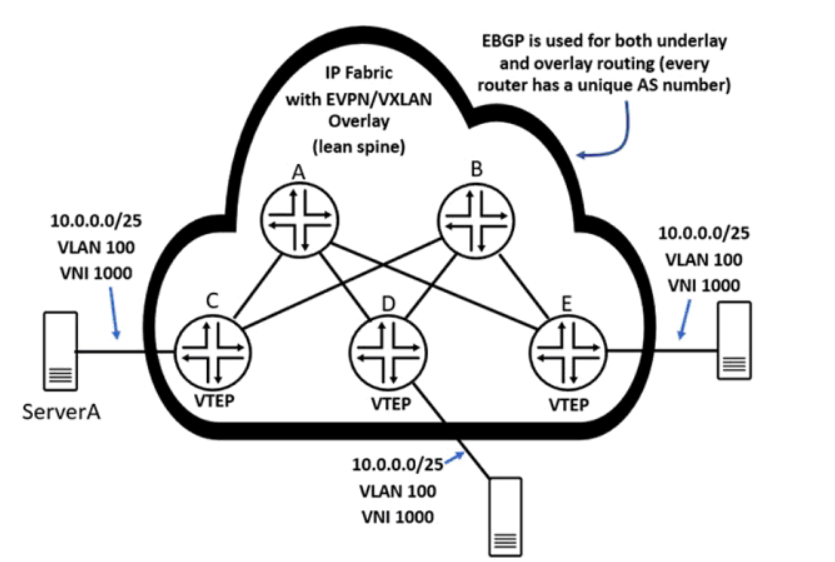
- A. Router E will replicate and send a copy of the received VXLAN packet to router D.
- B. Router C will send a VXLAN packet destined only to router D and router E.
- C. Router D will not replicate and send a copy of the received VXLAN packet to router E.
- D. Router C will send a single VXLAN packet to one remote VTEP.
Answer:
ad
Question 10
You are deploying an 802.1X solution and must determine what would happen if clients are unable to re-authenticate to the RADIUS server.
In this scenario, which configuration would provide access to the network if the supplicant is already authenticated?
- A. move
- B. permit
- C. deny
- D. sustain
Answer:
d