microsoft 98-368 practice test
Mobility and Devices Fundamentals
Last exam update: Apr 17 ,2025
Question 1
You have an external monitor connected to a laptop computer that is running Windows 10. The monitors are configured to
provide a panoramic display that continues across both monitors.
You want to move the system tray to the secondary monitor. Both monitors must continue to display screen data.
Which Display setting you select?
- A. Custom scaling
- B. Show only on 2
- C. Extend desktop to this display
- D. Make this my main display
Answer:
D
Explanation:
References: https://www.tenforums.com/tutorials/3871-change-main-display-windows-10-a.html
Question 2
Your new Windows 8.1 computer is connected to your home wireless network.
You want to share music and photos on your new computer with other members of your family. You want to avoid setting up
separate user accounts for each member of your family. A single password for all the shared files will suffice.
Which Windows 8.1 networking feature satisfies these requirements?
- A. Network Discovery
- B. HomeGroup
- C. Virtual Private Network
- D. Broadband (PPPoE)
Answer:
B
Explanation:
A homegroup makes it easier to share files and printers on a home network. You can share pictures, music, videos,
documents, and printers with other people in your homegroup. Other people can't change the files that you share, unless you
give them permission to do so.
Reference: http://windows.microsoft.com/en-us/windows7/what-is-a-homegroup
Question 3
What is an example of the way in which a Trojan horse commonly spreads to other computers?
- A. It inserts copies of itself into other computer programs
- B. It traverses a network by exploiting a vulnerability
- C. It pretends to be a document from a friend
- D. It downloads from an infected web page
Answer:
D
Explanation:
Trojan horses are commonly found on websites that offer free software, such as shareware programs. These communal
gathering spots on the Web give Trojan horse writers a degree of anonymity along with the chance of attacking as many
random victims as possible. Since website operators rarely have time to thoroughly examine every file posted, an occasional
Trojan horse can slip through the checking procedures unnoticed. -
Reference: HOW TROJAN HORSES SPREAD
http://etutorials.org/Misc/computer+book/Part+2+Dangerous+Threats+on+the+Internet/Chapter+8 +Trojan+Horses-
+Beware+of+Geeks+Bearing+Gifts/HOW+TROJAN+HORSES+SPREAD/
Question 4
You manage Windows 8 Pro desktop and laptop computers. Which volume types can you encrypt by using BitLocker?
- A. dynamic volumes
- B. simple volumes
- C. virtual hard disks
- D. software-used RAID
Answer:
B
Explanation:
Bitlocker supports Basic (simple) volumes.
Incorrect answers:
Not A: Dynamic disks are not supported by BitLocker.
Not C: Bootable and non-bootable virtual hard disks (VHDs)
Not D: Software-based RAID systems are not supported by Bitlocker.
Reference: BitLocker Frequently Asked Questions (FAQ) https://technet.microsoft.com/en-us/library/hh831507.aspx
Question 5
Your universitys IT department currently has no Active Directory strategy.
The university needs a solution that allows you to manage users and groups to secure access to Microsoft online services
such as Microsoft Office 365.
Which Active Directory strategy should the university use?
- A. Active Directory Federation services
- B. Active Directory Lightweight Directory services
- C. Active Directory Certificate services
- D. Azure Active Directory
Answer:
D
Explanation:
Azure Active Directory is preintegrated with Salesforce.com, Office 365, Box and many more.
Question 6
HOTSPOT
You want to use a Microsoft Account to log into devices on your home network.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area: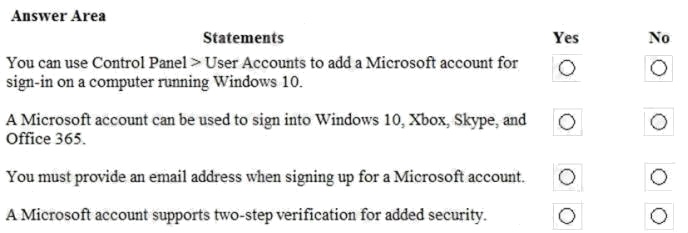
Answer:
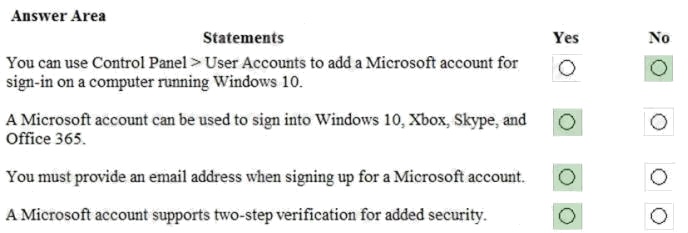
Explanation:
References: https://account.microsoft.com/account
https://support.microsoft.com/en-us/help/12408/microsoft-account-how-to-use-two-step-verification
Question 7
Your parents want you to help them protect a tax return file that is on their computer. You use BitLocker to encrypt the hard
drive that contains the file. You then make a backup copy of the file.
What will occur if you attempt to copy the backup copy to a USB flash drive?
- A. The backup copy will remain encrypted
- B. BitLocker will encrypt the USB flash drive
- C. BitLocker will prevent you from moving the file
- D. The backup copy will be decrypted
Answer:
A
Explanation:
References:
https://social.technet.microsoft.com/Forums/en-US/94951675-b9ac-4ba2-880d-2da98defd560/ bitlocker-does-not-decrypt-
files-when-moving-file-from-hard-drive-to-another-device
Question 8
You need to create an Azure storage account through Azure Storage Services to support an Azure Windows virtual machine
(VM). You want to keep subscription costs to a minimum.
What type of storage account should you create?
- A. Standard storage performance tier
- B. Blob cool access tier
- C. Premium storage performance tier
- D. Blob hot access tier
Answer:
D
Explanation:
References: https://www.petri.com/choosing-azure-storage-account-type https://docs.microsoft.com/en-
us/azure/storage/common/storage-introduction
Question 9
You are using dual monitors on a Windows 8.1 computer. You want to move system tray to the secondary monitor.
Which Display option in Control Panel should you select?
- A. Make this my main display
- B. Landscape orientation
- C. PC Screen only
- D. Extend desktop to this display
Answer:
A
Question 10
You are tracking hardware and software inventory on various devices.
You need to identify the requirements to support communication between the devices and the Microsoft Intune administrative
console.
Which device requirement must be met?
- A. All devices must be domain members
- B. Windows computers must run Windows 8.1 or later
- C. Microsoft Intune agent must be installed
- D. All enrolled devices must be in the same organizational unit (OU)
Answer:
C
Explanation:
The devices need the Microsoft Intune client installed. This software is also known as Microsoft Intune agent.
Question 11
Your company wants to implement file and document security for domain member clients and registered bring your own
device (BYOD) devices. Administrators should be able to apply permissions based on well-defined rules, including the
automatic classification of files. Policies need to be distributed through group policy.
The solution should include auditing to support forensic analysis.
What should you use?
- A. Software Restriction Policies
- B. Active Directory Federated Services
- C. Dynamic Access Control
- D. Azure Rights Management
Answer:
C
Explanation:
References: https://docs.microsoft.com/en-us/windows-server/identity/solution-guides/dynamic-access-controloverview
https://docs.microsoft.com/en-us/windows-server/identity/solution-guides/dynamic-accesscontrol--scenario-overview
Question 12
Your company uses Windows 10 Work Folders on personal devices. The devices are all registered in Microsoft Intune.
You need to enforce the following security requirements on the personal devices:
Company data can be removed if an employee is terminated.
Company data cannot be accessed if a devise is lost or stolen.
What should you do?
- A. Enable selective wipe, and enforce a lock screen and password
- B. Enable selective wipe, and secure files transfers with SSL
- C. Enable selective wipe, and enforce encryption
- D. Enforce encryption and enforce a lock screen and password
Answer:
C
Explanation:
* Microsoft Intune provides selective wipe, full wipe, remote lock, and passcode reset capabilities.A selective wipe to remove
only company data.
* Encryption on Mobile Devices can be managed with Configuration Manager and Intune
Reference: Help protect your data with remote wipe, remote lock, or passcode reset using Microsoft Intune
https://technet.microsoft.com/en-us/library/jj676679.aspx
Reference: Managing Encryption on Mobile Devices with Configuration Manager and Intune
http://blogs.technet.com/b/pauljones/archive/2014/08/04/managing-encryption-on-mobile-deviceswith-configuration-
manager-and-intune.aspx
Question 13
This question requires that you evaluate the underlined text to determine if it is correct.
The OneDrive service is used to create a private, enterprise-based social network.
Review the underlined text. If it makes the statement correct, select No change is needed. If the statement is incorrect,
select the answer choice than makes the statement correct.
- A. No change is needed
- B. Skype for Business
- C. Yammer
- D. Azure
Answer:
C
Explanation:
References: https://products.office.com/en-za/yammer/yammer-overview
Question 14
DRAG DROP
Match each Microsoft cloud service to the feature it provides.
Instructions: To answer, drag the appropriate Microsoft cloud service from the column of the left to its feature on the right.
Each service may be used once, more than once, or not at all. Each correct match is worth one point.
Select and Place: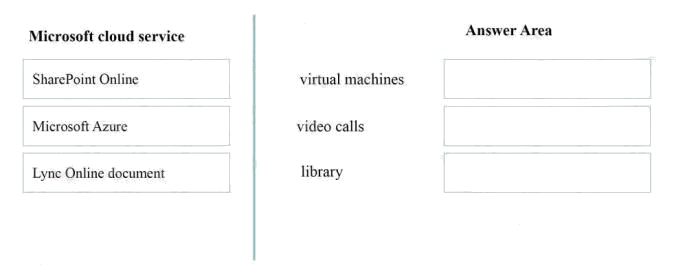
Answer:
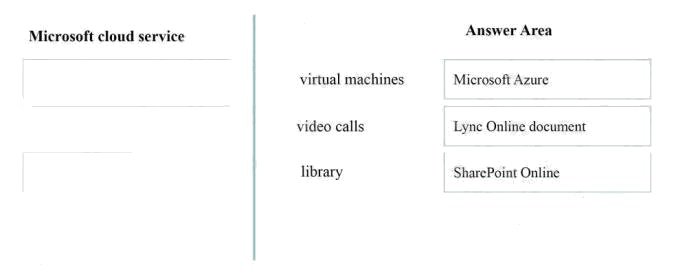
Explanation:
* Microsoft Azure Virtual Machines allow you to deploy a wide range of computing solutions in anagile way. With Virtual
Machines, you can deploy nearly instantaneously and you pay only by the minute.
* Present a document online using Lync
If you have Lync installed, you can present a document in an online conversation or meeting, work with other people on it in
real time, and even let someone else take control of it.
* A library is a collection of files. In SharePoint, a library is a type of list. Each file is a content item.Libraries have extra
features, such as synchronisation, viewing/editing, or managing files.
Question 15
You perform a bare metal installation of Microsoft Windows 10 Enterprise on a new computer. The computer has a single 1
TB hard disk that you configure as a single partition.
Which file system should you use to format the disk partition?
- A. NTFS
- B. ReFS
- C. FAT32
- D. exFAT
Answer:
A