Question 1 Topic 5, Case Study 5Case Study Question View Case
DRAG DROP
You need to ensure disaster recovery requirements are met.
What code should you add at line PC16?
To answer, drag the appropriate code fragments to the correct locations. Each code fragment may be used once, more than
once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: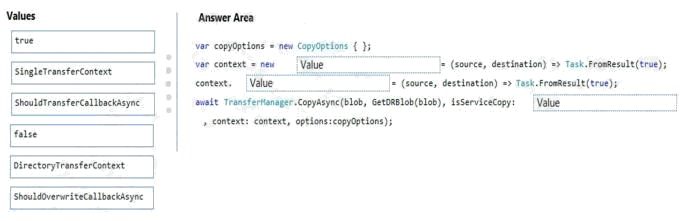
Answer:
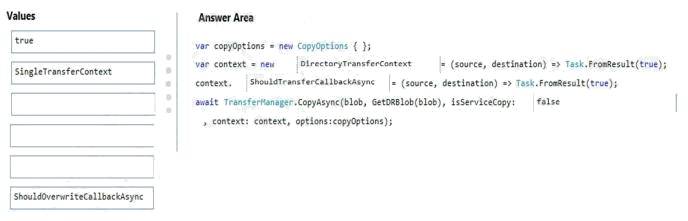
Explanation:
Scenario: Disaster recovery. Regional outage must not impact application availability. All DR operations must not be
dependent on application running and must ensure that data in the DR region is up to date.
Box 1: DirectoryTransferContext
We transfer all files in the directory.
Note: The TransferContext object comes in two forms: SingleTransferContext and DirectoryTransferContext. The former is
for transferring a single file and the latter is for transferring a directory of files.
Box 2: ShouldTransferCallbackAsync
The DirectoryTransferContext.ShouldTransferCallbackAsync delegate callback is invoked to tell whether a transfer should be
done.
Box 3: False
If you want to use the retry policy in Copy, and want the copy can be resume if break in the middle, you can use SyncCopy
(isServiceCopy = false).
Note that if you choose to use service side copy ('isServiceCopy' set to true), Azure (currently) doesn't provide SLA for that.
Setting 'isServiceCopy' to false will download the source blob loca
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-use-data-movement-library
https://docs.microsoft.com/en-
us/dotnet/api/microsoft.windowsazure.storage.datamovement.directorytransfercontext.shouldtransfercallbackasync?view=az
ure-dotnet
Develop for Azure storage
Comments
Question 2 Topic 6, Case Study 6Case Study Question View Case
HOTSPOT
You need to configure Azure Cosmos DB.
Which settings should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: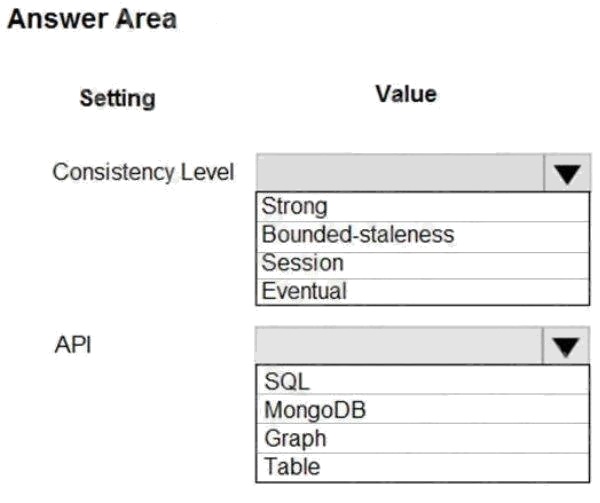
Answer:
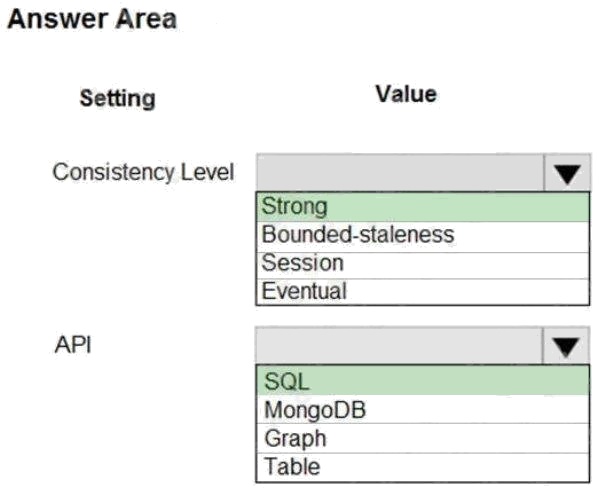
Explanation:
Box 1: Strong
When the consistency level is set to strong, the staleness window is equivalent to zero, and the clients are guaranteed to
read the latest committed value of the write operation.
Scenario: Changes to the Order data must reflect immediately across all partitions. All reads to the Order data must fetch the
most recent writes.
Note: You can choose from five well-defined models on the consistency spectrum. From strongest to weakest, the models
are: Strong, Bounded staleness, Session, Consistent prefix, Eventual
Box 2: SQL
Scenario: You identify the following requirements for data management and manipulation: Order data is stored as
nonrelational JSON and must be queried using Structured Query Language (SQL).
Comments
Question 3 Topic 6, Case Study 6Case Study Question View Case
HOTSPOT
You need to retrieve all order line items from Order.json and sort the data alphabetically by the city.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: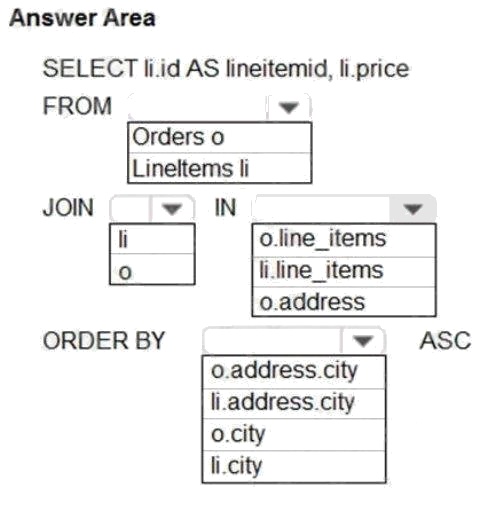
Answer:
Explanation:
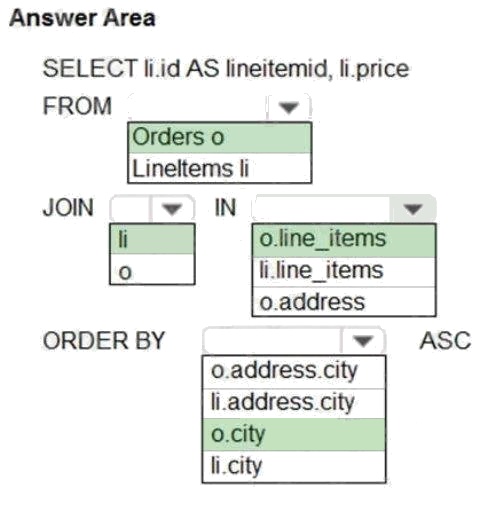
Box 1: orders o
Scenario: Order data is stored as nonrelational JSON and must be queried using SQL.
Box 2:li
Box 3: o.line_items
Box 4: o.city
The city field is in Order, not in the 2s.
Develop for Azure storage
Comments
Question 4 Topic 7, Case Study 7Case Study Question View Case
DRAG DROP
You need to add markup at line AM04 to implement the ContentReview role.
How should you complete the markup? To answer, drag the appropriate json segments to the correct locations. Each json
segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to
view content.
NOTE: Each correct selection is worth one point.
Select and Place: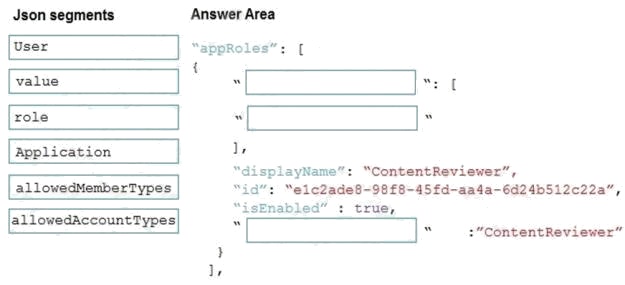
Answer:
Explanation:
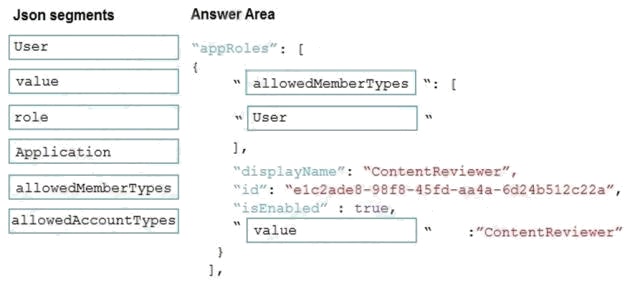
Box 1: allowedMemberTypes allowedMemberTypes specifies whether this app role definition can be assigned to users and
groups by setting to "User", or to other applications (that are accessing this application in daemon service scenarios) by
setting to "Application", or to both.
Note: The following example shows the appRoles that you can assign to users. "appId": "8763f1c4-f988-489c-a51e-
158e9ef97d6a",
"appRoles": [
{
"allowedMemberTypes": [
"User"
],
"displayName": "Writer",
"id": "d1c2ade8-98f8-45fd-aa4a-6d06b947c66f",
"isEnabled": true,
"description": "Writers Have the ability to create tasks.", "value": "Writer"
}
],
"availableToOtherTenants": false,
Box 2: User
Scenario: In order to review content a user must be part of a ContentReviewer role.
Box 3: value value specifies the value which will be included in the roles claim in authentication and access tokens.
Reference:
https://docs.microsoft.com/en-us/graph/api/resources/approle
Comments
Question 5 Topic 7, Case Study 7Case Study Question View Case
HOTSPOT
You need to add code at line AM09 to ensure that users can review content using ContentAnalysisService.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: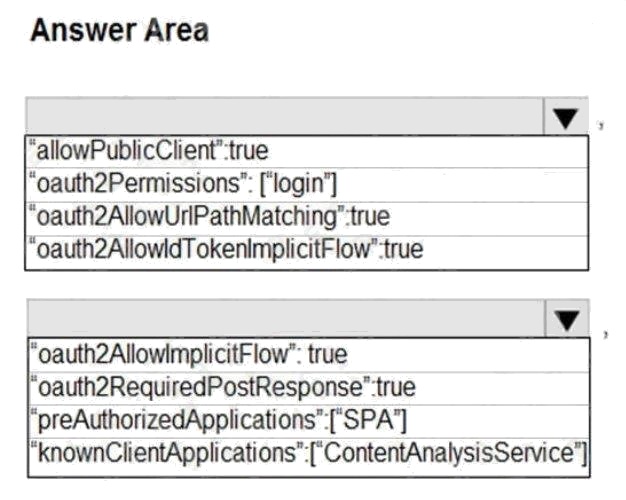
Answer:
Explanation:
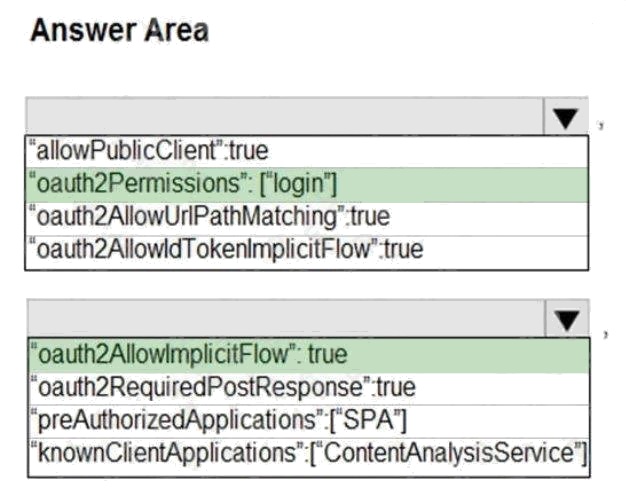
Box 1: "oauth2Permissions": ["login"]
oauth2Permissions specifies the collection of OAuth 2.0 permission scopes that the web API (resource) app exposes to
client apps. These permission scopes may be granted to client apps during consent.
Box 2: "oauth2AllowImplicitFlow":true
For applications (Angular, Ember.js, React.js, and so on), Microsoft identity platform supports the OAuth 2.0 Implicit Grant
flow.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/develop/reference-app-manifest
Comments
Question 6 Topic 7, Case Study 7Case Study Question View Case
HOTSPOT
You need to ensure that network security policies are met.
How should you configure network security? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: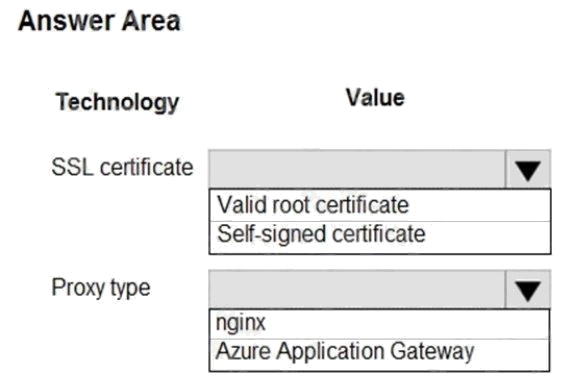
Answer:
Explanation:
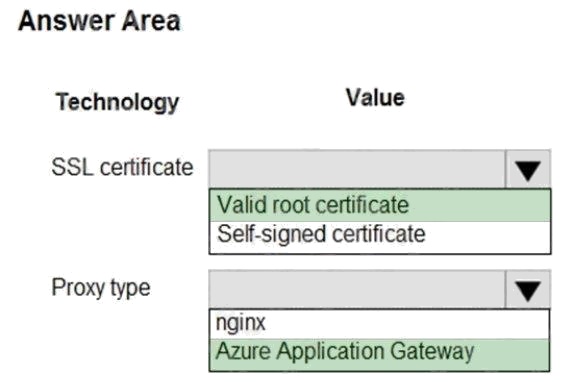
Box 1: Valid root certificate
Scenario: All websites and services must use SSL from a valid root certificate authority.
Box 2: Azure Application Gateway Scenario:
Any web service accessible over the Internet must be protected from cross site scripting attacks. All Internal services

must only be accessible from Internal Virtual Networks (VNets) All parts of the system must support inbound and outbound
traffic restrictions.
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web
applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that
exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
Application Gateway supports autoscaling, SSL offloading, and end-to-end SSL, a web application firewall (WAF), cookie-
based session affinity, URL path-based routing, multisite hosting, redirection, rewrite HTTP headers and other features.
Note: Both Nginx and Azure Application Gateway act as a reverse proxy with Layer 7 load-balancing features plus a WAF to
ensure strong protection against common web vulnerabilities and exploits.
You can modify Nginx web server configuration/SSL for X-XSS protection. This helps to prevent cross-site scripting exploits
by forcing the injection of HTTP headers with X-XSS protection.
Reference:
https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/ag-overview https://www.upguard.com/articles/10-tips-for-
securing-your-nginx-deployment
Implement Azure security
Comments
Question 7 Topic 7, Case Study 7Case Study Question View Case
DRAG DROP
You need to add YAML markup at line CS17 to ensure that the ContentUploadService can access Azure Storage access
keys.
How should you complete the YAML markup? To answer, drag the appropriate YAML segments to the correct locations.
Each YAML segment may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: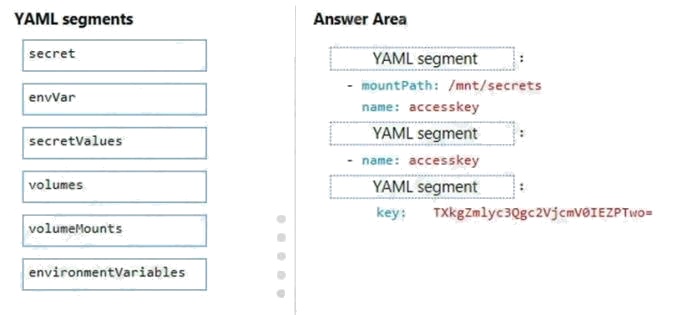
Answer:
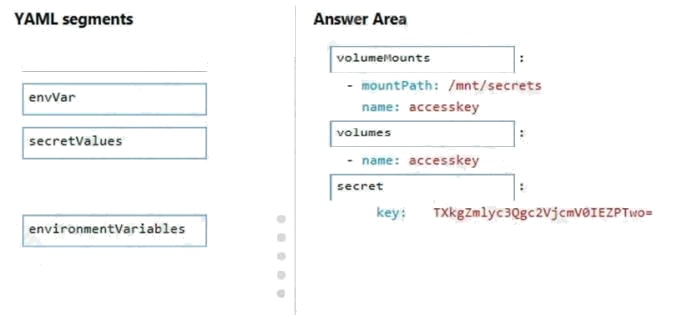
Explanation:
Box 1: volumeMounts Example:
volumeMounts:
- mountPath: /mnt/secrets name: secretvolume1 volumes:
- name: secretvolume1secret: mysecret1: TXkgZmlyc3Qgc2VjcmV0IEZPTwo=
Box 2: volumes
Box 3: secret
Reference: https://docs.microsoft.com/en-us/azure/container-instances/container-instances-volume-secret
Comments
Question 8 Topic 7, Case Study 7Case Study Question View Case
HOTSPOT
You need to add code at line AM10 of the application manifest to ensure that the requirement for manually reviewing content
can be met.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: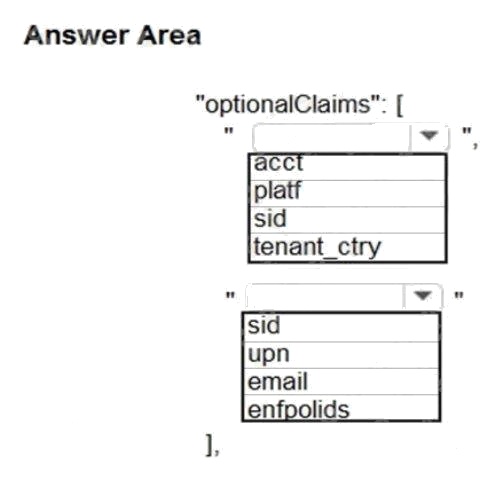
Answer:
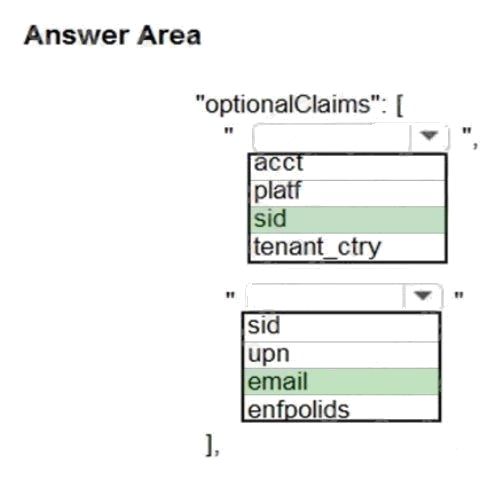
Explanation:
Box 1: sid
Sid: Session ID, used for per-session user sign-out. Personal and Azure AD accounts.
Scenario: Manual review
To review content, the user must authenticate to the website portion of the ContentAnalysisService using their Azure AD
credentials. The website is built using React and all pages and API endpoints require authentication. In order to review
content a user must be part of a ContentReviewer role.
Box 2: email
Scenario: All completed reviews must include the reviewers email address for auditing purposes.
Implement Azure security
Comments
Question 9 Topic 8, Case Study 8Case Study Question View Case
HOTSPOT
You need to secure the Shipping Function app.
How should you configure the app? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: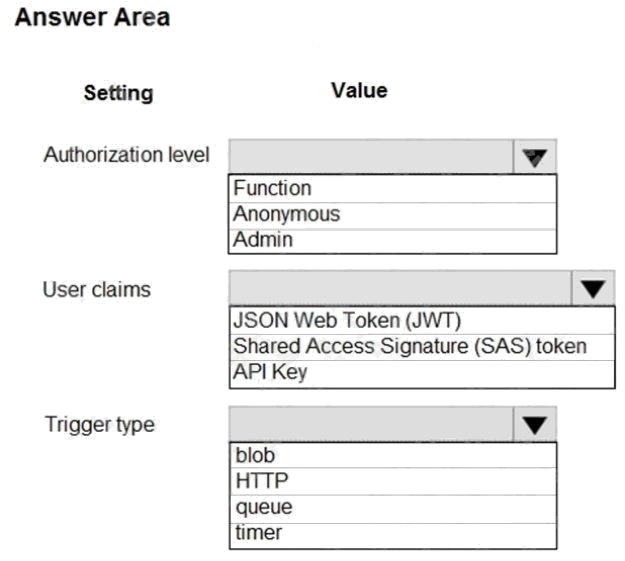
Answer:
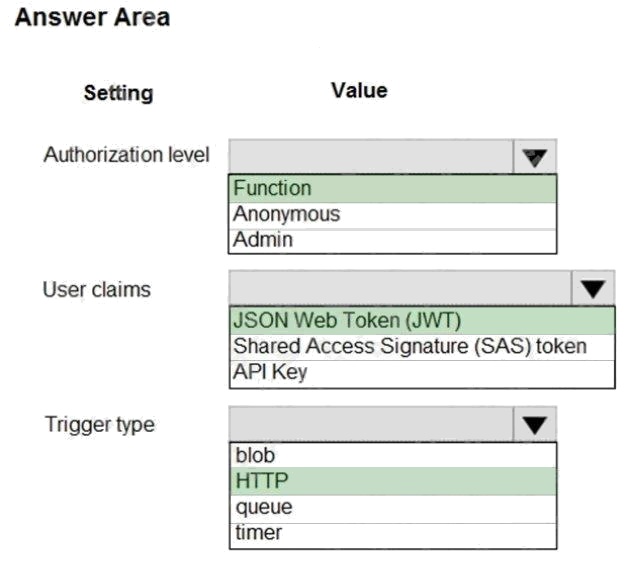
Explanation:
Scenario: Shipping Function app: Implement secure function endpoints by using app-level security and include Azure Active
Directory (Azure AD).
Box 1: Function
Box 2: JSON based Token (JWT)
Azure AD uses JSON based tokens (JWTs) that contain claims
Box 3: HTTP
How a web app delegates sign-in to Azure AD and obtains a token
User authentication happens via the browser. The OpenID protocol uses standard HTTP protocol messages.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-scenarios
Comments
Question 10 Topic 8, Case Study 8Case Study Question View Case
You need to secure the Shipping Logic App.
What should you use?
- A. Azure App Service Environment (ASE)
- B. Integration Service Environment (ISE)
- C. VNet service endpoint
- D. Azure AD B2B integration
Answer:
B
Explanation:
Scenario: The Shipping Logic App requires secure resources to the corporate VNet and use dedicated storage resources
with a fixed costing model.
You can access to Azure Virtual Network resources from Azure Logic Apps by using integration service environments (ISEs).
Sometimes, your logic apps and integration accounts need access to secured resources, such as virtual machines (VMs)
and other systems or services, that are inside an Azure virtual network. To set up this access, you can create an integration
service environment (ISE) where you can run your logic apps and create your integration accounts. Reference:
https://docs.microsoft.com/en-us/azure/logic-apps/connect-virtual-network-vnet-isolated-environment-overview
Comments
Page 1 out of 25
Viewing questions 1-10 out of 252
page 2