microsoft ms-500 practice test
Microsoft 365 Security Administration
Note: Test Case questions are at the end of the exam
Last exam update: Mar 26 ,2025
Question 1 Topic 7, Mixed Questions
As part of your GDPR responsibilities, a user makes a formal request for you to provide a copy of all personal data held in
Office 365. You're enlisting the help of your compliance team and you are planning to minimize the number of actions.
Which of these actions do you take? (Choose all that apply.)
- A. Assign eDiscovery permissions to case members
- B. Create a Data Subject Request (DSR)
- C. Create an eDiscovery case
- D. Add members to the case
- E. Modify search query
- F. Save search query
- G. Run search query
- H. Place data sources on hold
- I. Create a report
- J. Export the data
Answer:
A B D G J
Explanation:
Be sure to also know the order of operations in case you have to arrange fewer options in the correct order.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/manage-gdpr-data-subject-requests-with-the-dsr-case-
tool?view=o365-worldwide
Question 2 Topic 7, Mixed Questions
Which role do you need if you want to view alerts in the data governance and DLP categories? You must implement the
principle of least privilege.
- A. Record Management
- B. Compliance Administrator
- C. Global Administrator
- D. Security Reader
- E. Security Administrator
Answer:
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide
Question 3 Topic 7, Mixed Questions
Which of the following device platforms can be enrolled through the Device Enrolment Program (DEP)?
- A. Android
- B. Android for Work
- C. iOS
- D. Windows 8.1
- E. Windows 10
Answer:
C
Explanation:
Reference:
https://docs.microsoft.com/en-us/mem/intune/enrollment/device-enrollment-program-enroll-ios
Question 4 Topic 7, Mixed Questions
Which of the following Windows 10 Enterprise features provides identity protection?
- A. Windows Hello
- B. Credential Guard
- C. Device Guard
- D. Defender Antivirus
- E. Defender ATP
Answer:
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/
Question 5 Topic 7, Mixed Questions
You are the M365 administrator for your organization. Your company has created a policy that requires that the mailboxes of
employees that have left the organization be retained for content searches for three years and then be automatically deleted.
You also need the licenses assigned to the users to be available for reassignment to new employees.
Select all the actions that will accomplish this task. Every selection is part of the overall solution. (Choose two.)
- A. Delete the user account
- B. Block the user account
- C. Assign an AIP policy
- D. Assign a retention policy
- E. Create an eDiscovery case
Answer:
A D
Explanation:
Blocking the user account will prevent logins, but not release the license you must delete the account to release the
license. You could alternatively block and manually release the license, but that is not one of the answer options.
AIP is for protection (classify, label and encrypt), not retention. It can also not auto-delete things. You must use a retention
label.
It is not required to open an eDiscovery case yet. It will be possible in future, but not needed to meet the objectives of the
question.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/inactive-mailboxes-in-office-365?view=o365-worldwide
Question 6 Topic 7, Mixed Questions
You want to prevent users from accessing cloud applications which your organization has determined to be unsanctioned
apps. You mark the identified apps as unsanctioned in MCAS.
What else is required to enforce the policy? (Choose two.)
- A. Integrate with Azure ATP
- B. Integrate with Defender ATP
- C. Integrate with the firewall
- D. Integrate with Intune
- E. Integrate with Office ATP
Answer:
B C
Explanation:
You can download the FW blocking script or enable integration with ATP.
FW blocking only works for on-premises connections, ATP works regardless of where the user connects from
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/governance-discovery
Question 7 Topic 7, Mixed Questions
You create a new user using the M365 admin center. You plan to assign the new user the Security Reader role, but you first
want to confirm what permissions will be made available to the user if you do so.
Which interface will you use to accomplish your task?
- A. MCAS
- B. Office 365 Security & Compliance Center
- C. Azure Portal
- D. M365 Security Center
- E. M365 Compliance Center
Answer:
C
Explanation:
AAD Roles and administrators is the only one of the interfaces listed that enumerates the permissions of roles.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/roles-create-custom
Question 8 Topic 7, Mixed Questions
You are configuring Intune Mobile Application Management policies.
Which of the following restrictions would require your devices to be enrolled in Mobile Device Management?
- A. Prevent Save-As
- B. Restrict Cut, copy and paste
- C. Require simple PIN for access
- D. Block managed apps from running on jailbroken or rooted devices
- E. All of the options
- F. None of the options
Answer:
F
Explanation:
All of the options are available through MAM policies only and do not require the device to be enrolled into MDM for it to
work.
Reference:
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy
Question 9 Topic 7, Mixed Questions
Your organization has several conditional access policies for various purposes. One of these policies requires users to
provide MFA when they access Teams. However, you're uncertain that all users are being prompted for MFA and you want
to verify this.
Where would you obtain information to help you reach your goal?
- A. O365 Security & Compliance Center, Reports
- B. M365 Security Center, Reports
- C. M365 Admin Center, Reports
- D. Azure AD portal, Enterprise applications
- E. Azure AD portal, Conditional access
Answer:
D
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-sign-in-problem-first-party-
microsoft#check-a-specific-conditional-access-policy
Question 10 Topic 7, Mixed Questions
Which two do you need to configure to allow access to your company's Exchange online service from Outlook on mobile
devices, but only if the corporate data on the mobile device is encrypted? (Choose two.)
- A. Cloud App Security access policy
- B. Information Protection policy
- C. Intune App Protection policy
- D. Conditional Access policy
- E. Intune Device Compliance policy
Answer:
C D
Explanation:
You need a conditional access policy to block access unless Outlook is used (exception) You need a MAM-WE policy to
ensure Outlook mobile encrypts the data
Reference:
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy
Question 11 Topic 7, Mixed Questions
Using minimum effort, how would you enforce Safe Boot on your Windows 10 computers?
- A. Run Msinfo32
- B. Deploy AD Group Policy
- C. Modify BIOS settings
- D. Deploy an Intune configuration profile
Answer:
C
Explanation:
Reference:
https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/disabling-secure-boot
Question 12 Topic 7, Mixed Questions
NOTE: This question is a part of a series of questions that present the same scenario. For each of the following statements,
select the best response(s) to the question or statement below. Each answer is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in
the review screen.
You have devices organized in groups as in the exhibit. You also have Intune device configuration profiles assigned to
groups as in the second exhibit. You want to determine which policies will be applied to which devices.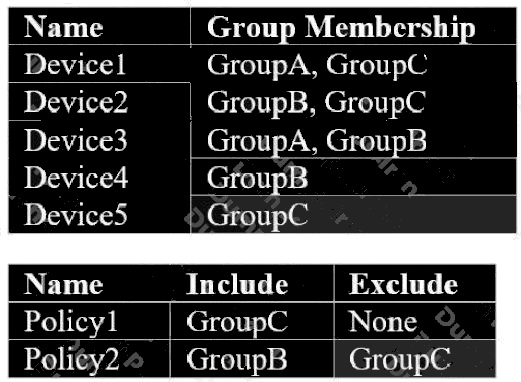
Select all devices on which Policy2 will be applied. (Choose two.)
- A. Device1
- B. Device2
- C. Device3
- D. Device4
- E. Device5
Answer:
C D
Explanation:
Excluded groups override included groups
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-assign#assign-a-device-profile
Question 13 Topic 7, Mixed Questions
NOTE: This question is a part of a series of questions that present the same scenario. For each of the following statements,
select the best response(s) to the question or statement below. Each answer is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in
the review screen.
You have devices organized in groups as in the exhibit. You also have Intune device configuration profiles assigned to
groups as in the second exhibit. You want to determine which policies will be applied to which devices.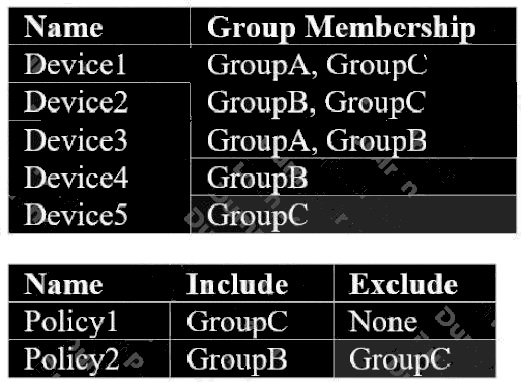
Select all devices on which Policy1 will be applied. (Choose three.)
- A. Device1
- B. Device2
- C. Device3
- D. Device4
- E. Device5
Answer:
A B E
Explanation:
Excluded groups override included groups
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-assign#assign-a-device-profile
Question 14 Topic 7, Mixed Questions
NOTE: This question is a part of a series of questions that present the same scenario. For each of the following statements,
select the best response(s) to the question or statement below. Each answer is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in
the review screen.
You have user accounts as in the exhibit.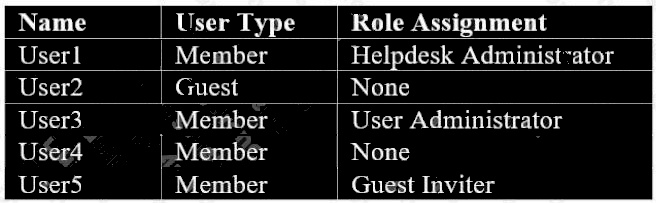
Which users passwords can be reset by User3? (Choose three.)
- A. User1
- B. User2
- C. User3
- D. User4
- E. User5
Answer:
C D E
Explanation:
Helpdesk admin and user admin can reset passwords of non-admin users. No-one can reset passwords of guest accounts
since these accounts are held and managed by another Azure AD tenant/ instance.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directory-assign-admin-roles
Question 15 Topic 7, Mixed Questions
NOTE: This question is a part of a series of questions that present the same scenario. For each of the following statements,
select the best response(s) to the question or statement below. Each answer is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in
the review screen.
You have user accounts as in the exhibit.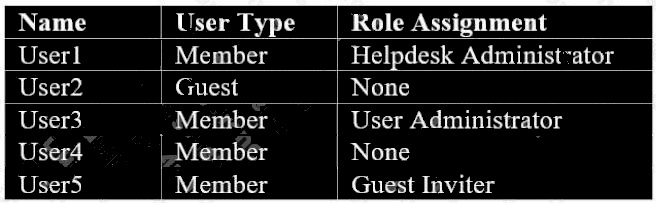
Which users passwords can be reset by User1? (Choose three.)
- A. User1
- B. User2
- C. User3
- D. User4
- E. User5
Answer:
A D E
Explanation:
Helpdesk admin and user admin can reset passwords of non-admin users. No-one can reset passwords of guest accounts
since these accounts are held and managed by another AAD tenant/instance. Careful of the tricky nature of some of these
questions of course User1 can reset his own password, but that might not be obvious to you when you are rushing or not
thinking clearly about the question and scenario.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directory-assign-admin-roles