NetApp ns0-162 practice test
NetApp Certified Data Administrator, ONTAP Exam
Last exam update: Dec 19 ,2024
Question 1
Which configuration Is supported using NetApp's All SAN Array (ASA)?
- A. 24-node cluster
- B. single node cluster
- C. 2-node cluster
- D. 12-node cluster
Answer:
C
Explanation:
Reference:
https://docs.netapp.com/allsan/index.jsp?topic=%2Fcom.netapp.doc.dot-asa-config%2FGUID-C0C9B6EF-1AA7-429E-BB84-AC5F9E16D088.html
Question 2
Exhibit.
Miss-----------------
You have an ONTAP 9.8 cluster. After network maintenance, the LIF that is shown in the exhibit is not
always on a correct port and is unreachable by users until the LIFs are moved to port eOc or eOd on
either storage node.
In this scenario, which action should you take to ensure that the LIF only fails over to the correct
ports?
- A. Create a DNS load balancing zone.
- B. Split the broadcast domain.
- C. Create an IPspace.
- D. Change the LIF’s failover policy to sfo-partner-only
Answer:
B
Question 3
You have an ESXI cluster with VMware VMFS LUNs on an AFF A400 system. After troubleshooting
performance Issues, you determine that timeout best practices are not set on the hosts.
In this scenario, which NetApp tool would apply the best practice settings?
- A. SnapCenter Plug-in for VMware vSphere
- B. SAN Host Utilities
- C. Virtual Storage Console (VSC)
- D. SnapManager
Answer:
C
Explanation:
Reference:
https://docs.netapp.com/vapp-96/index.jsp?topic=%2Fcom.netapp.doc.vsc-dsg%2FGUID-EAD6C97B-A9E4-4C07-BAD8-790ACEE0897B.html
Virtual Storage Console for VMware vSphere checks and sets the ESXi host multipathing settings and
HBA timeout settings that work best with NetApp storage systems.
Question 4
Exhibit.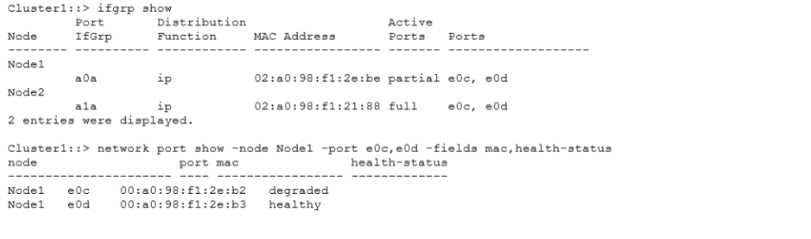
You have received an alert from Active IQ Unified Manager that interface eOc has gone offline.
Network engineering asks for the corresponding MAC address for the port that has a problem.
Referring to the exhibit, which MAC address would you supply to the engineering team?
- A. 02:a0:98:fl:2e:be
- B. 00:a0:98:fl:2e:b2
- C. 00:a0:98:fl:2e:b3
- D. 02:a0:98:fl:21:88
Answer:
C
Question 5
What establishes a quorum in a 4-node cluster?
- A. epsilon
- B. cluster peer
- C. ONTAP Mediator
- D. TieBreaker
Answer:
A
Explanation:
Reference:
https://library.netapp.com/ecmdocs/ECMP1196798/html/GUID-EFE1DEF4-8B87-4C4A-8E4E-C6C79F760710.html
Question 6
A volume Is set to use Adaptive QoS with the default policy.
In this scenario, which change would affect the QoS throughput ceiling?
- A. Data is added to the volume.
- B. Disks are added to the volume's aggregate.
- C. More clients access the volume.
- D. The volume Is resized.
Answer:
D
Explanation:
Reference:
https://www.flackbox.com/netapp-storage-qos-tutorial
https://kb.netapp.com/Advice_and_Troubleshooting/Data_Storage_Software/ONTAP_OS/What_is_
Adaptive_QoS_and_how_does_it_work
Question 7
You need to Increase the number of files that can be created In a volume. Which two methods
enable you to achieve this goal? (Choose two.)
- A. Increase the number of files permitted on the volume.
- B. Set the space guarantee to 'volume".
- C. Set the fractional reserve to "0".
- D. Increase the size of the volume.
Answer:
AD
Explanation:
Reference:
https://docs.netapp.com/ontap-9/index.jsp?topic=%2Fcom.netapp.doc.dot-cm-vsmg%2FGUID-E4A62DE4-E7A4-410E-9E9E-8EB5C360D8FF.html
Question 8
When you set up an ONTAP cluster, which two SVM types are automatically created? (Choose two.)
- A. admin
- B. node
- C. data
- D. cluster
Answer:
AB
Explanation:
Reference:
https://library.netapp.com/ecmdocs/ECMP1354558/html/GUID-D860985F-11BF-4589-9457-E0FD03130B1F.html
Question 9
You want to configure Active Directory domain controller access for NetApp ONTAP cluster
administration. In this scenario, which two actions would accomplish this task? (Choose two.)
- A. Configure an authentication tunnel through an admin SVM.
- B. Use the vservar active-directory create command to create a computer account on the domain for a non-CIFS SVM.
- C. Use the vserver active-directory create command to create a computer account on the domain for a CIFS SVM.
- D. Configure an authentication tunnel through an existing CIFS SVM.
Answer:
BD
Explanation:
https://docs.netapp.com/ontap-9/index.jsp?topic=%2Fcom.netapp.doc.pow-adm-auth-rbac%2FGUID-BC7B1934-DDE6-4AFB-A319-6C85D1ADACB6.html
Configuring an authentication tunnel
If you have already configured a CIFS server for a data SVM, you can use the security login domain-
tunnel create command to configure the SVM as a gateway, or tunnel, for AD access to the cluster.
Creating an SVM computer account on the domain
If you have not configured a CIFS server for a data SVM, you can use the vserver active-directory
create command to create a computer account for the SVM on the domain.
Question 10
Which security method would be used to authenticate targets and Initiators In an ISCSI
environment?
- A. NIS
- B. LDAP
- C. /etc/hosts
- D. CHAP
Answer:
D
Explanation:
Reference:
https://library.anetapp.com/ecmdocs/ECMP1368845/html/GUID-5DCC56E6-A0EF-4E1D-B52C-F372D9CB986A.html
Question 11
You want to scale out storage performance for read-Intensive data across multiple locations. In this
scenario, which NetApp feature accomplishes this task?
- A. FlexClone
- B. FlexVol
- C. FlexCache
- D. Flash Pool
Answer:
C
Explanation:
Reference:
https://www.netapp.com/knowledge-center/what-is-flex-cache/
Question 12
Exhibit.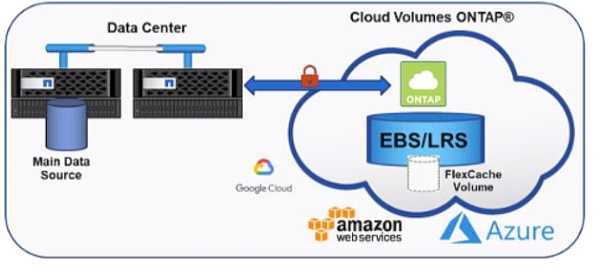
You are caching on-premises ONTAP volumes into the cloud with Cloud Volumes ONTAP as shown in
the exhibit. In this scenario, which two protocols are supported? (Choose two.)
- A. SMB
- B. NVMe
- C. ISCSI
- D. NFS
Answer:
CD
Explanation:
Reference:
https://docs.netapp.com/us-en/occm/pdfs/sidebar/Manage_Cloud_Volumes_ONTAP.pdf
https://cloud.netapp.com/hubfs/ONTAP_Cloud_FAQs-final.pdf
Question 13
After deploying an ONTAP 9.8 cluster, you want to disable the unused Ethernet ports. In this scenario,
which two methods would accomplish this task? (Choose two.)
- A. Use ONTAP System Manager.
- B. Use the command line interface.
- C. Use Active IQ Config Advisor.
- D. Use Active IQ Unified Manager.
Answer:
AB
Question 14
Your company wants to Increase access security In both their NFS and ISCSI environments. Currently
ISCSI Is not authenticated and NFS relies only on export policies for security.
Which two enhancements do you use to satisfy this new criteria? (Choose two.)
- A. Enable Kerberos for NFS exports.
- B. Enable Kerberos for iSCSI LUN access.
- C. Enable Challenge-Handshake Authentication Protocol (CHAP) for NFS exports.
- D. Enable Challenge-Handshake Authentication Protocol (CHAP) for ISCSI LUN access.
Answer:
AD
Explanation:
Reference:
https://docs.netapp.com/ontap-9/index.jsp?topic=%2Fcom.netapp.doc.cdot-famg-nfs%2FGUID-0D282583-0A6F-4556-AF94-4B08FC5ADDE8.html
Question 15
After creating an SVM In an ONTAP cluster, you are asked to delegate administration of the newly
created SVM to an SVM administrator. In this scenario, which two tasks must you complete? (Choose
two.)
- A. Create the vsadmin user account in the new SVM.
- B. Create a LIF for SVM management.
- C. Configure role-based access control (RBAC) for the vsadmin user account.
- D. Set a password for the vsadmin user account.
Answer:
BD
Explanation:
Reference:
https://www.ibm.com/docs/en/nseriessoftware/com.ibm.nseries.software.doc/sc27628501.pdf