Question 1
An administrator wants to centralize the storage of CCTV data from all its branches in a
remote datacenter. To meet compliance standards, the requirements for this solution are as
follows:
• Data must be kept for a minimum of 10 years
• Data must be accessible for use at any time
• Data must be secure
How should the administrator satisfy these requirements?
- A. Create a Volume Group and mount to a server 2) Configure a LifeCycle policy for a 10year retention 3) Enable encryption on the vDisks B. 1) Create an Objects bucket 2) Configure WORM for a 10year retention 3) Replace Objects’s self-signed certificate with a CA-signed certificate C. 1) Create a Storage Container 2) Configure WORM for a 10year retention3) Replace Prism Element’s self-signed certificate with a CA-signed certificate
- D. Create a Files share 2) Configure a Lifecycle policy for a 10 year retention 3) Enable encryption on SMB protocol
Answer:
A
Comments
Question 2
What are the three main metrics monitored for each Files instance and per share?
- A. Concurrent Connections, Throughput and OP sizes
- B. Access time, IOPS and Throughput
- C. Bandwidth, Speed and IOPS
- D. Latency, Throughput and IOPS
Answer:
C
Comments
Question 3
The Compliance department would like the administrator to have the ability to revert
documents to previous versions. How should the administrator facilitate this request?
- A. Configure protection snapshots on the File Server
- B. Enable Self-Service Restore on the Share/Export
- C. Configure Protection snapshots on the Share/Export
- D. Enable Self-Service Restore on the File Server
Answer:
A
Comments
Question 4
An administer is determining the most recent operation a user performed on the share cifs1
within the last 24 hours? How should the administrator complete this task in File Analytics?
- A. In the Anomalies section, view the anomaly rule created for the user with an interval of 24 hours.
- B. In the Audit Trails section, search for the cifs1 share and view the actions on the share over the past 24hour range
- C. In the Audit Trails section, search for the user and view their last operations.
- D. In the Anomalies section, select Users exceed an operation count threshold an input the 24hour range for share cifs1
Answer:
D
Comments
Question 5
An administrator is upgrading Files. When running the pre upgrade check, the following
message is generated:
FileServer in HA state
Which two steps should the administrator take to resolve this error message? (Choose two.)
- A. Check if Stargate services are running.
- B. Check for alerts for NVB being down.
- C. Check if Zookeeper services are running
- D. Verify FSVM is booted and not stuck
Answer:
B,D
Comments
Question 6
Refer to the exhibit.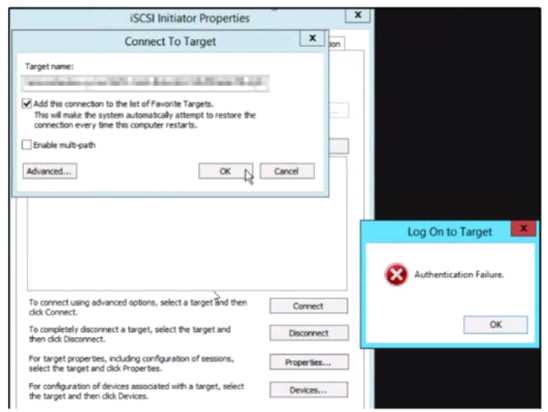
An administrator reports that a Volume Group (VG) is no longer accessible on their server.
Upon attempting to reconnect, an error is displayed , as shown in the exhibit.
Which condition would cause this error?
- A. The client is trying to access the wrong target.
- B. MPIO is enabled for the volume group
- C. Encryption is enabled for the container hosting the VG.
- D. The wrong CHAP secret has been configured.
Answer:
A
Comments
Question 7
Which two statements are true about object counts in an object store?
- A. Upload counts are included in the object counts
- B. Each upload of a multipart upload is counted as a separate object until the object is finalized.
- C. Each upload of a multipart upload is counted as a separate object
- D. Upload Counts are not included in the object counts
Answer:
CD
Comments
Question 8
A company has two Files clusters for their workloads. Once cluster is running VDI workloads
and another one is running Big Data (large file ingestion) workloads. The administrator is
planning to optimize the workload performance on the cluster where the VDI workloads are
running.
The administrator needs to complete these requirements
• Determine the current workload type on the cluster.
• Optimize the file share for operations such as small overwrites into larger files
Which two actions should the administrator take to satisfy this requirement? (choose two)
- A. Set the share workload type to sequential
- B. Execute command afs share.edit share-name share_workload_type=default
- C. Set the share workload type to random
- D. Execute command afs share.io_size_distribution
Answer:
A,D
Comments
Question 9
An administer has a new requirement to separate management and block storage network traffic for
bare-metal workloads. What should the administrator do to satisfy this requirement?
- A. Add a second virtual NIC to CVMs, configure them in prism.
- B. Configure Backplane LAN to isolate hypervisor traffic
- C. Configure Management LAN to segment internal communication.
- D. Enable Volumes network segmentation
Answer:
C
Comments
Question 10
An administrator has received the following alert:
File Server In Heterogeneous State
What is the reason for this alert?
- A. The FSVMs do not match in their CPU or memory configuration.
- B. The FSVMs are not distributed properly on the hosts in the cluster
- C. Performance of the File Server is optimal and the alert can be ignored
- D. The hosts where the FSVMs run do not match in their CPU or memory configuration.
Answer:
B
Comments
Page 1 out of 9
Viewing questions 1-10 out of 98
page 2