oracle 1z0-1067-21 practice test
Oracle Cloud Infrastructure 2021 Cloud Operations Associate Exam
Last exam update: Apr 14 ,2025
Question 1
You set up a bastion host in your VCN to only allow your IP address (140.19.2.140) to establish SSH
connections to your Compute Instances that are deployed in a private subnet. The Compute
Instances have an attached Network Security Group with a Source Type: Network Security Group
(NSG), Source NSG: NSG-050504. To secure the bastion host, you added the following ingress rules to
its Network Security Group: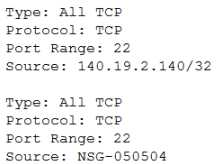
However, after checking the bastion host logs, you discovered that there are IP addresses other than
your own that can access your bastion host.
What is the root cause of this issue? (Choose the best answer.)
- A. An ALARM with a name unique across the tenancy, a SUBSCRIPTION, and a METRIC with the measurement of interest.
- A. The Security List allows access to all IP address which overrides the Network Security Group ingress rules.
- B. A TOPIC with a name unique across the tenancy, a SUBSCRIPTION, and a MESSAGE where content is published.
- B. All compute instances associated with NSG-050504 are also able to connect to the bastion host.
- C. A TOPIC with a name unique across the compartment, a SUBSCRIPTION, and a MESSAGE where content is published.
- C. The port 22 provides unrestricted access to 140.19.2.140 and to other IP address.
- D. An ALARM with a name unique across the compartment, a SUBSCRIPTION, and a METRIC with the measurement of interest.
- D. A netmask of /32 allows all IP address in the 140.19.2.0 network, other than your IP 140.19.2.140
Answer:
B
Question 2
You have a group pf developers who launch multiple VM.Standard2.2 compute instances every day
into the compartment Dev. As a result, your OCI tenancy quickly hit the service limit for this shape.
Other groups can no longer create new instances using VM.Standard2.2 shape.
Because of this, your company has issued a new mandate that the Dev compartment must include a
quota to allow for use of only 20 VM.Standard2.2 shapes per Availability Domain. Your solution
should not affect any other compartment in the tenancy.
Which quota statement should be used to implement this new requirement? (Choose the best
answer.)
- A. Client-side encryption is managed by the customer.
- A. set compute quota vm-standard2–2count to 10 in compartment dev where request.region = us- phoenix–1
- B. Data needs to be decrypted on the client side before retrieving it.
- B. set compute quota vm-standard2–2–count to 20 in compartment dev
- C. OCI Vault Management is used by default to provide data security.
- C. zero compute quotas in tenancy set compute quota vmstandard22count to 20 in compartment dev
- D. All traffic to and from Object Storage service is encrypted using TLS.
- D. zero compute quotas in tenancy set compute quota vmstandard22count to 20 in tenancy dev
- E. A VPN connection to OCI is required to ensure secure data transfer to an object storage bucket.
Answer:
B
Explanation:
https://docs.oracle.com/en-us/iaas/Content/General/Concepts/resourcequotas.htm#two
Question 3
Your deployment platform within Oracle Cloud Infrastructure (OCI) leverages a compute instance
with multiple block volumes attached. There are multiple teams that use the same compute instance
and have access to these block volumes. You want to ensure that no one accidentally deletes any of
these block volumes. You have started to construct the following IAM policy but need to determine
which permissions should be used.
allow group DeploymentUsers to manage volume-family where ANY
{ request.permission != <???>, request.permission != <???>, request.permission !=
<???> }
Which permissions can you use in place of <???> in this policy? (Choose the best answer.)
- A. OS Management Service agent (osms) must be installed on the instances.
- A. VOLUME_DELETE, VOLUME_ATTACHMENT_DELETE, VOLUME_BACKUP_DELETE
- B. Audit logs for the instances should be enabled.
- B. VOLUME_ERASE, VOLUME_ATTACHMENT_ERASE, VOLUME_BACKUP_ERASE
- C. Service gateway should be setup to allow instances to send metrics to monitoring service.
- C. ERASE_VOLUME, ERASE_VOLUME_ATTACHMENT, ERASE_VOLUME_BACKUP
- D. Monitoring for the instances should not be enabled.
- D. DELETE_VOLUME, DELETE_VOLUME_ATTACHMENT, DELETE_VOLUME_BACKUP
Answer:
A
Explanation:
https://docs.oracle.com/en-us/iaas/Content/Identity/Concepts/policyadvancedfeatures.htm
Question 4
You have been asked to investigate a potential security risk on your companys Oracle Cloud
Infrastructure (OCI) tenancy. You decide to start by looking through the audit logs for suspicious
activity.
How can you retrieve the audit logs using the OCI Command Line Interface (CLI)? (Choose the best
answer.)
- A. –t
- A. oci audit event list –-end-time $end-time –-compartment-id $compartment-id
- B. – –image-id
- B. oci audit event list –-start-time $start-time –-compartment-id $compartment-id
- C. – –shape “”
- C. oci audit event list -start-time $start-time -end-time $end-time - compartment-id $compartment-id
- D. –c
- D. oci audit event list –-start-time $start-time –-end-time $end–time –-tenancy-id $tenancy–id
- E. – –subnet-id
Answer:
C
Explanation:
https://docs.oracle.com/en-us/iaas/tools/oci-cli/2.9.7/oci_cli_docs/cmdref/audit/event/list.html
Question 5
Multiple teams are sharing a tenancy in Oracle Cloud Infrastructure (OCI). You are asked to figure out
an appropriate method to manage OCI costs.
Which is NOT a valid technique to accurately attribute costs to resources used by each team?
(Choose the best answer.)
- A. Network Security Group
- A. Create a Cost-Tracking tag. Apply this tag to all resources with team information. Use the OCI cost analysis tools to filter costs by tags.
- B. Data Safe
- B. Create separate compartment for each team. Use the OCI cost analysis tools to filter costs by compartment.
- C. Web Application Framework (WAF)
- C. Create an Identity and Access Management (IAM) group for each team. Create an OCI budget for each group to track spending.
- D. Vault
- D. Define and use tags for resources used by each team. Analyze usage data from the OCI Usage Report which has detailed information about resources and tags.
Answer:
C
Explanation:
Budgets are set on cost-tracking tags or on compartments not by user groups
Question 6
Which statement about Oracle Cloud Infrastructure paravirtualized block volume attachments is
TRUE? (Choose the best answer.)
- A. 10.0.0.0/30 and 192.168.0.0/30
- A. Paravirtualized volumes may reduce the maximum IOPS performance for larger block volumes.
- B. 10.0.0.0/8 and 11.0.0.0/8
- B. Paravirtualized is required to manage iSCSI configuration for virtual machine instances.
- C. 10.0.8.0/21 and 10.0.16.0/22
- C. Paravirtualized volumes become immediately available on bare metal compute instances.
- D. 10.0.0.0/16 and 10.0.64.0/24
- D. Paravirtualization utilizes the internal storage stack of compute instance OS and network hardware virtualization to access block volumes.
Answer:
A
Explanation:
https://docs.oracle.com/en-us/iaas/Content/Block/Concepts/overview.htm#Paravirtualized
Reference:
https://blogs.oracle.com/cloud-infrastructure/paravirtualized-block-volume-attachments-
for-vms
Question 7
You have been asked to update the lifecycle policy for object storage using the Oracle Cloud
Infrastructure (OCI) Command Line Interface (CLI).
Which command can successfully update the policy? (Choose the best answer.)
- A. Allow group SystemAdmins to manage virtual-network-family in compartment CompartmentB:CompartmentC
- A. oci os object-lifecycle-policy delete –ns <object_storage_namespace> –bn <bucket_name>
- B. Allow group SystemAdmins to manage virtual-network-family in compartment Root
- B. oci os object-lifecycle-policy put –ns <object_storage_namespace> –bn <bucket_name>
- C. Allow group SystemAdmins to manage virtual-network-family in compartment CompartmentA:CompartmentB:CompartmentC
- C. oci os object-lifecycle-policy put ns <object_storage_namespace> bn <bucket_name> items <json_formatted_lifecycle_policy>
- D. Allow group SystemAdmins to manage virtual-network-family in compartment CompartmentC
- D. oci os object-lifecycle-policy get –ns <object_storage_namespace> –bn <bucket_name>
Answer:
C
Explanation:
https://docs.oracle.com/en-us/iaas/Content/Object/Tasks/usinglifecyclepolicies.htm#cli
https://docs.oracle.com/en-us/iaas/tools/oci-cli/2.17.0/oci_cli_docs/cmdref/os/object-lifecycle-policy/put.html
Question 8
You are launching a Windows server in your Oracle Cloud Infrastructure (OCI) tenancy. You provided
a startup script during instance initialization, but it was not executed successfully.
What is a possible reason for this error? (Choose the best answer.)
- A. Limit access to the same Availability Domain (AD) as the File Storage service where possible.
- A. Didn’t include anything in user_data.
- B. Serialize operations to the file system to access consecutive blocks as much as possible.
- B. Wrote a custom script which tried to install GPU drivers.
- C. Right size compute instances from where file system is accessed based on their network capacity.
- C. Ran a cloudbase-init script instead of cloud-init.
- D. Increase concurrency by using multiple threads, multiple clients, and multiple mount targets.
- D. Specified a #directive on the first line of your script.
Answer:
C
Explanation:
Reference:
https://blogs.oracle.com/cloud-infrastructure/windows-custom-startup-scripts-and-
cloud-init-on
- oracle-cloud-infrastructure
Question 9
You created an Oracle Linux compute instance through the Oracle Cloud Infrastructure (OCI)
management console then immediately realize you forgot to add an SSH key file. You notice that OCI
compute service provides instance console connections that supports adding SSH keys for a running
instance. Hence, you created the console connection for your Linux server and activated it using the
connection string provided. However, now you get prompted for a username and password to login.
What option should you recommend to add the SSH key to your running instance, while minimizing
the administrative overhead? (Choose the best answer.)
- A. oci os object-lifecycle-policy delete –ns –bn
- A. You need to configure the boot loader to use ttyS0 as a console terminal on the VM.
- B. oci os object-lifecycle-policy put –ns –bn
- B. You need to terminate the running instance and recreate it by providing the SSH key file.
- C. oci os object-lifecycle-policy put –ns –bn – –items
- C. You need to reboot the instance from the console, boot into the bash shell in maintenance mode, and add SSH keys for the opc user.
- D. oci os object-lifecycle-policy get –ns –bn
- D. You need to modify the serial console connection string to include the identity file flag, i to specify the SSH key to use.
Answer:
C
Explanation:
If you created an instance without an SSH key, you can use the serial console to boot into
maintenance mode and add or reset the SSH key for the opc user or reset the password for the opc
user. Alternately, you can stop the instance, attach the boot volume to a new instance, and configure
SSH on the new instance.
https://docs.oracle.com/en-us/iaas/Content/Compute/Tasks/accessinginstance.htm
Question 10
You are using Oracle Cloud Infrastructure (OCI) services across several regions: us-phoenix-1, us-
ashburn-1, uk-london-1 and ap-tokyo-1. You have creates a separate administrator group for each
region: PHX-Admins, ASH-Admins, LHR-Admins and NRT-Admins, respectively.
You want to restrict admin access to a specific region. E.g., PHX-Admins should be able to manage all
resources in the us-phoenix-1 region only and not any other OCI regions.
What IAM policy syntax is required to restrict PHX-Admins to manage OCI resources in the us-
phoenix-1 region only? (Choose the best answer.)
- A. VOLUME_DELETE, VOLUME_ATTACHMENT_DELETE, VOLUME_BACKUP_DELETE
- A. Allow group PHX-Admins to manage all-resources in tenancy where request.region= ‘phx’
- B. VOLUME_ERASE, VOLUME_ATTACHMENT_ERASE, VOLUME_BACKUP_ERASE
- B. Allow group PHX-Admins to manage all-resources in tenancy where request.permission= ‘phx’
- C. ERASE_VOLUME, ERASE_VOLUME_ATTACHMENT, ERASE_VOLUME_BACKUP
- C. Allow group PHX-Admins to manage all-resources in tenancy where request.target= ‘phx’
- D. DELETE_VOLUME, DELETE_VOLUME_ATTACHMENT, DELETE_VOLUME_BACKUP
- D. Allow group PHX-Admins to manage all-resources in tenancy where request.location= ‘phx’
Answer:
A
Explanation:
Use conditions to limit access depending on region: request.region
https://docs.oracle.com/en-
us/iaas/Content/Identity/Reference/policyreference.htm#General
Question 11
You launched a Linux compute instance to host the new version of your company website via Apache
Httpd server on HTTPS (port 443). The instance is created in a public subnet along with other
instances. The default security list associated to the subnet is: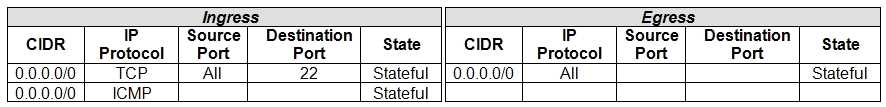
You want to allow access to the company website from public internet without exposing websites
eventually hosted on the other instances in the public subnet.
Which action would you take to accomplish the task? (Choose the best answer.)
- A. Create Auth token, use it to create an object storage credential by executing DBMS_CLOUD.CREATE_CREDENTIAL, using the web console upload the CSV files to an OCI object storage bucket, create the tables in the ADW database and then execute DBMS_CLOUD.COPY_DATA for each CSV file to copy the contents into the corresponding ADW database table.
- A. Create a network security group, add a stateful rule to allow ingress access on port 443 and associate it to the public subnet that hosts the company website.
- B. Create the tables in the ADW database and then execute SQL*Loader for each CSV file to load the contents into the corresponding ADW database table.
- B. In default security list, add a stateful rule to allow ingress access on port 443.
- C. Create Auth token, use it to create an object storage credential by executing DBMS_CLOUD.CREATE_CREDENTIAL, using OCI CLI upload the CSV files to an OCI object storage bucket, create the tables in the ADW database and then execute Data Pump Import for each CSV file to copy the contents into the corresponding ADW database table.
- C. Create a new security list with a stateful rule to allow ingress access on port 443 and associate it to the public subnet.
- D. Create Auth token, use it to create an object storage credential by executing DBMS_CLOUD.CREATE_CREDENTIAL, using OCI CLI upload the CSV files to an OCI object storage bucket, create the tables in the ADW database and then execute DBMS_CLOUD.COPY_DATA for each CSV file to copy the contents into the corresponding ADW database table.
- D. Create a network security group, add a stateful rule to allow ingress access on port 443 and associate it to the instance that hosts the company website.
Answer:
D
Explanation:
Since we want to avoid exposing other instances in the same public subnet to the internet, Network
Security Groups (NSG) must be used instead of Security Lists. NSG are attached to the vnic of the
instance and not to the subnet
Question 12
The boot volume on your Oracle Linux instance has run out of space. Your application has crashed
due to a lack of swap space, forcing you to increase the size of the boot volume.
Which step should NOT be included in the process used to solve the issue? (Choose the best answer.)
- A. set compute quota vm-standard2–2count to 10 in compartment dev where request.region = us-phoenix–1
- A. Reattach the boot volume and restart the instance.
- B. set compute quota vm-standard2–2–count to 20 in compartment dev
- B. Attach the resized boot volume to a second instance as a data volume; extend the partition and grow the file system in the resized boot volume.
- C. zero compute quotas in tenancy set compute quota vm–standard2–2–count to 20 in compartment dev
- C. Stop the instance and detach the boot volume.
- D. zero compute quotas in tenancy set compute quota vm–standard2–2–count to 20 in tenancy dev
- D. Resize the boot volume by specifying a larger value than the boot volume’s current size.
- E. Create a RAID 0 configuration to extend the boot volume file system onto another block volume.
Answer:
B
Question 13
You have ordered two FastConnect connections that provide a high availability connection
architecture between your on-premises data center and Oracle Cloud Infrastructure (OCI). You want
to run these connections in an ACTIVE/PASSIVE architecture.
How can you accomplish this? (Choose the best answer.)
- A. The Security List allows access to all IP address which overrides the Network Security Group ingress rules.
- A. Decrease the prefix length of AS for the FastConnect you want to use as PASSIVE connection.
- B. All compute instances associated with NSG-050504 are also able to connect to the bastion host.
- B. Enable BGP on the FastConnect that you want as the ACTIVE connection.
- C. The port 22 provides unrestricted access to 140.19.2.140 and to other IP address.
- C. Use AS PATH prepending with your routes.
- D. A netmask of /32 allows all IP address in the 140.19.2.0 network, other than your IP 140.19.2.140
- D. Adjust one of the connections to have a higher ASN.
Answer:
C
Explanation:
Reference:
https://docs.oracle.com/en-
us/iaas/Content/Resources/Assets/whitepapers/connectivity
- redundancy-guide.pdf (5)
Question 14
You have set an alarm to be generated when the CPU usage of a specified instance is greater than
10%. In the alarm behavior view below you notice that the critical condition happened around 23:30.
You were expecting a notification after 1 minute, however, the alarm firing state did not begin until
23:33.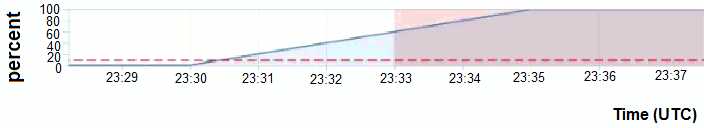
What should you change to fix it? (Choose the best answer.)
- A. Create an instance pool with a VM.Standard2.2 shape instance configuration. Setup the autoscaling configuration to use 2 availability domains and have a minimum of 2 instances, to handle the weekly spikes, and a maximum of 4 instances.
- A. Change the alarm’s metric interval to 1.
- B. Create an instance with 1 OCPU shape. Use the Resize Instance action to scale up to a larger shape when more resources are needed.
- B. Change the alarm condition to be grater than 3%.
- C. Create an instance with 1 OCPU shape. Use a CLI script to clone it when more resources are needed.
- C. Change the notification topic that you previously associated with the alarm.
- D. Create an instance pool with a VM.Standard2.1 shape instance configuration. Setup the autoscaling configuration to use 2 availability domains and have a minimum of 2 instances and a maximum of 8 instances.
- D. Change the alarm’s trigger delay minutes value to 1.
Answer:
D
Question 15
You have created the following JSON file to specify a lifecycle policy for one of your object storage
buckets: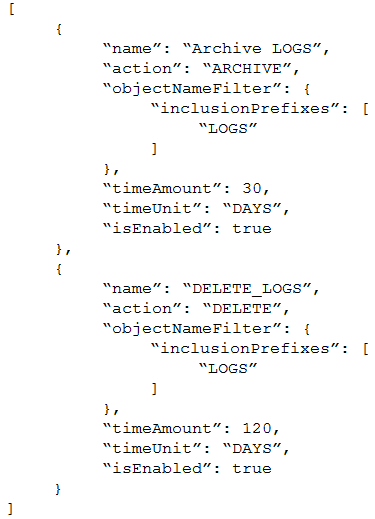
How will this policy affect the objects that are stored in the bucket? (Choose the best answer.)
- A. Reattach the boot volume and restart the instance.
- A. Objects with the prefix “LOGS” will be retained for 120 days and then deleted permanently.
- B. Attach the resized boot volume to a second instance as a data volume; extend the partition and grow the file system in the resized boot volume.
- B. Objects containing the name prefix LOGS will be automatically migrated from standard Storage to Archive storage 30 days after the creation date. The object will be deleted 120 days after creation.
- C. Stop the instance and detach the boot volume.
- C. The objects with prefix “LOGS” will be deleted 30 days after creation date.
- D. Resize the boot volume by specifying a larger value than the boot volume’s current size.
- D. Objects containing the name prefix LOGS will be automatically migrated from standard Storage to Archive storage 30 days after the creation date. The object will be migrated back to standard Storage 120 days after creation.
- E. Create a RAID 0 configuration to extend the boot volume file system onto another block volume.
Answer:
B