oracle 1z0-1070-21 practice test
Oracle Cloud Platform Identity and Security Management 2021 Specialist Exam
Last exam update: Jan 29 ,2025
Question 1
Which is a major concern with regards to Line of Business (LOB) buyers when acquiring cloud
services?
- A. Line of Business (LOB) buyers were buying IT services without notifying their security team.
- B. Customers are acquiring services that may not be in compliance with external regulations.
- C. Line of Business (LOB) buyers do not have executive approval to acquire such services.
- D. End users have no visibility over an organization’s cloud strategy.
Answer:
C
Question 2
From the Oracle Management Cloud Security Monitoring and Analytics dashboard, you noticed a
threat of key transfer and suspicious SMB communication activity by a user.
Which two remedial actions will be taken automatically to mitigate some risk? (Choose two.)
- A. User added to suspicious data access watchlist
- B. Multi-factor Authentication (MFA) is imposed
- C. Host anti-virus (AV) update enforced
- D. Targets added to file change watchlist
Answer:
A,B
Question 3
Suspicious events that you or Oracle CASB Cloud Service determine to be serious, result in an entry
in which of these pages?
- A. Configuration, Threat Management
- B. Risk Events
- C. Incidents
- D. Reports
Answer:
B
Question 4
Oracle Security Monitoring and Analytics is built on top of Oracle Log Analytics, and the procedures
for adding and managing entities are identical.
How do you associate entities with existing log sources?
- A. Create a group in the administration console in Oracle Management Cloud.
- B. Use the Oracle Log Analytics Entities page.
- C. Edit property values for existing entries.
- D. Create and set global properties.
Answer:
A
Question 5
Which two features does Oracle CASB Cloud Service support? (Choose two.)
- A. automatically resolves suspicious events that occur
- B. security controls for custom applications running on AWS
- C. prevents unauthorized access to cloud application files
- D. security controls for Oracle ERP Cloud Service
Answer:
B,C
Question 6
Which Identity SOC Cloud Service supports auto-access to the configurations in dynamic application
environments?
- A. Oracle Orchestration Cloud Service
- B. Oracle Configuration and Compliance Cloud Service
- C. Oracle Identity Cloud Service
- D. Oracle Log Analytics Cloud Service
Answer:
C
Question 7
Which Oracle CASB Cloud Service feature could you use to quickly determine whether there is a
concentration of security threats that is originating from a specific geographic area?
- A. Access Map
- B. Key Security Indicators
- C. Risk Events
- D. Reports
Answer:
A
Question 8
Which four are the main pillars of the Oracle Identity Security Operations Center (SOC) solution?
(Choose four.)
- A. Threat Intelligence
- B. Cloud Access Security Broker (CASB)
- C. Security information and event management (SIEM)
- D. IT Orchestration
- E. Application Performance
- F. User Entity Behavior and Analytics (UEBA)
Answer:
B,C,E,F
Question 9
A customer use case requires the second Factor Email during Oracle Identity Cloud Service
Authentication process for a group of users only. The security administrator, signed in Oracle Identity
Cloud Service console, enabled the email factor, edited the default sign-on policy and added a new
sign-on rule. The new sign-on rule included the group name in the member of these groups
conditions and prompt for additional factor every time. The administrator saved both the rule and
the policy.
After executing this configuration, why does the email factor NOT appear to users from that group?
- A. The default Sign-on Policy can’t be changed.
- B. The security administrator needs to specify the list of users instead of the group name.
- C. The Passcode Length and Validity Duration of the email factor don’t have a default value.
- D. The security administrator didn’t change the order of the sign-on rules.
Answer:
C
Question 10
What do you add to applications if you want to create custom attributes that can be used to search
for the applications more effectively?
- A. Scopes
- B. Resources
- C. Audiences
- D. Tags
Answer:
D
Question 11
Click the exhibit.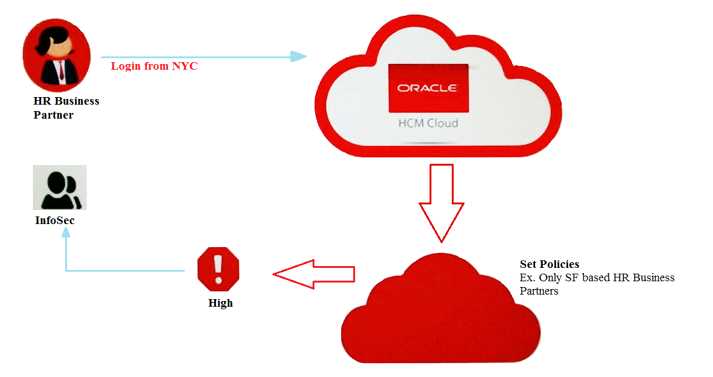
According to the diagram, which Oracle Identity Security Operations Center (SOC) component allows
you to monitor Oracle Human Capital Management (HCM) users activity and access management to
avoid service misuse?
- A. Oracle CASB Cloud Service
- B. Oracle Management Cloud
- C. Oracle Database Security
- D. Oracle Security Monitoring and Analytics Cloud Service
Answer:
D
Question 12
Which three are key business benefits of Oracle Security Monitoring and Analytics (SMA) Cloud
Service? (Choose three.)
- A. Greater SOC Efficiency
- B. Improved Security and Risk Posture
- C. Synchronize with on-premises directory structures
- D. Automate threat prevention
- E. Rapid Time to Value
Answer:
A,B,E
Question 13
Which feature do you activate in Oracle Identity Cloud Service so that users can use their Microsoft
Active Directory passwords to sign in to access resources that are protected by Oracle Identity Cloud
Service?
- A. The Import utility
- B. The bridge
- C. Identity Provider
- D. Delegated Authentication
Answer:
D
Question 14
In which Oracle Identity SOC component can you view threats like file integrity anomaly and
exfiltration attacks and the auto remediation action taken for an application?
- A. Oracle CASB Cloud Service
- B. Oracle Identity Cloud Service
- C. Oracle Configuration and Compliance Cloud Service
- D. Oracle Security Monitoring and Analytics Cloud Service
Answer:
A
Question 15
Which two statements are true for Security Monitoring and Analytics Cloud Service? (Choose two.)
- A. Gateway for Security Monitoring and Analytics Cloud Service could be deployed on AIX.
- B. Cloud Agent for Security Monitoring and Analytics Cloud Service could be deployed on AIX.
- C. Gateway for Security Monitoring and Analytics Cloud Service could not be deployed on a MAV operating system.
- D. Cloud Agent for Security Monitoring and Analytics Cloud Service could be deployed on a Chrome operating system.
Answer:
A,B