oracle 1z0-580 practice test
Solaris 11 Installation and Configuration Essentials Exam
Last exam update: Apr 14 ,2025
Question 1
The Oracle Solaris Image Packaging System (IPS) ________.
- A. requires the administrator to create software repositories
- B. requires a network connection to the Oracle software repositories
- C. automatically includes and installs required software dependence
- D. can be used on Oracle Solaris 10 with SVR4 packages
- E. can be used to manage remote systems' repositories
Answer:
C
Explanation:
Note:
* In many cases, one software package depends on another package. For example, one package
might require functionality that is in a second package in order to function or install correctly. These
relationships, or dependencies, between packages are important for automating package installation
operations and for upgrading system software to known and well-tested states. IPS supports a
number of different relationships between packages.
Incorrect:
Not B: IPS relies on network-accessible or locally available software repositories as a delivery
mechanism.
Not D:
Table, SVR4 and IPS Package Command Equivalents
SVR4 Package Command
IPS Package Command Equivalent
pkgadd
pkg install
patchadd
pkg update
pkgrm
pkg uninstall
pkgadm addcert, pkgadm removecert
pkg set-publisher -k, -c, --approve-ca-cert, --revoke-ca-cert, unset-ca-cert
pkginfo, pkgchk -l
pkg info, pkg list, pkg contents, pkg search
pkgchk
pkg verify, pkg fix, pkg revert
Question 2
The Oracle Solaris Image Packaging System (IPS) cannot be used to_____.
- A. manage local software repositories
- B. create new software repositories
- C. create new Oracle Solaris 11 boot environments
- D. restore an installed file to its original content
- E. manage permissions of installed software
Answer:
E
Explanation:
Incorrect:
not A: IPS relies on network-accessible or locally available software repositories as a delivery
mechanism, which is similar to how other operating systems (notably Oracle Linux) supply
software updates.
not D: can be done with the pkg command.
Note:
* Image Packaging System (IPS) is a new network based package management system included in
Oracle Solaris 11. It provides a framework for complete software lifecycle management such as
installation, upgrade and removal of software packages.
Safe system upgrades with ZFS boot environments
Network package repositories of software
Efficient downloads and automatic dependency checking
Support for disconnected data center environments
Extensive package publishing tools
Question 3
What physical devices will be used in sequence to boot the system, given the following output?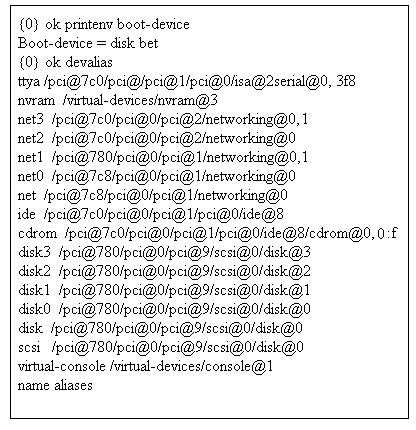
- A. disk then net
- B. /pci@780/pci@0/pci@1/network@0 then/pci@780/pci@0/pci@9/scsi@0/disk@0
- C. /pci@780/pci@0/pci@9/scsi@0 then/pci780/pci@0/pci@1/networking@0
- D. /pci@780/pci@0/pci@9/scsi@0/disk@1 then/pci780/pci@0/pci@1/networking@0,1
- E. /pci@780/pci@0/pci@9/scsi@0/disk@0 then/pci780/pci@0/pci@1/networking@0
Answer:
B
Explanation:
Note:
* second line in exhibit (minor typo):
boot-device = disk net
*The line starting with net is:
/pci@780/pci@0/pci@1/network@0
Question 4
Best practice for creating local IPS repositories recommends_______.
- A. avoiding the use of ZFS to host repositories
- B. creating a separate ZFS file system for each repository
- C. hosting local repositories on separate servers
- D. replicating all publishers across all repository servers
- E. creating one large repository for all required software
Answer:
B
Explanation:
Recommended best practice is to create a separate ZFS file system for your local package repository.
Using a separate ZFS file system enables you to take advantage of the following benefits:
Achieve better performance.
Set separate file system characteristics.
Directly snapshot and recover specified file systems.
If one system hosts more than one IPS repository, make each repository a separate ZFS file system so
that you can rollback and recover each repository separately.
Reference: Copying and Creating Oracle Solaris 11 Package Repositories, Prepare the Repository Host
System
Question 5
Three zones each need access to shared data. Which configuration method can be used to safely
achieve this goal?
- A. Put the data on an NFS server, and mount that share from each zone.
- B. Put the data on an NFS server, mount the share in the global zone, and configure a loopback mount from the global zone into each zone using zonecfg.
- C. Create an iSCSI LUN on a remote server, accessible to the global zone. Give each zone direct access to the LUN.
- D. Create a LUN on a SAN and give the global zone access to it. Give each zone direct device access to the LUN.
- E. Create a ZFS file system and utilize the cloning feature to replicate the data to the individual zones.
Answer:
B
Explanation:
How to Loopback Mount a File That Is Usually Not Visible in a Labeled Zone
This procedure enables a user in a specified labeled zone to view files that are not exported from the
global zone by default.
1. Halt the zone whose configuration you want to change.
# zoneadm -z zone-name halt
2. Loopback mount a file or directory.
For example, enable ordinary users to view a file in the /etc directory.
# zonecfg -z zone-name
add filesystem
set special=/etc/filename
set directory=/etc/filename
set type=lofs
add options [ro,nodevices,nosetuid]
end
exit
Note - Certain files are not used by the system, so that loopback mounting them has no effect. For
example, the /etc/dfs/dfstab file in a labeled zone is not checked by Trusted Extensions software. For
more information, see Sharing Files From a Labeled Zone.
3. Start the zone.
# zoneadm -z zone-name boot
Note:
* In this Solaris release, you create a ZFS file system share and publish the share as follows:
Create the file system share and define the NFS or SMB share properties by using the zfs share
command.
* ZFS File Sharing Within a Non-Global Zone
In previous Solaris releases, you could not create and publish NFS or SMB shares in a Oracle Solaris
non-global zone. In this Solaris release, you can create and publish NFS shares by using the zfs set
share command and the legacy share command with a non-global zone.
* If a ZFS file system is mounted and available in a non-global zone, it can be shared in that zone.
* A file system can be shared in the global zone if it is not mounted in a non-global zone or is not
shared to a non-global zone.
* If a ZFS file system's mountpoint property set to legacy, the file system can be shared by using the
legacy share command.
Reference: Oracle Solaris 11 Express, Managing Zones
Question 6
Examine the message below.
What would be the next action?
Message:
Intel(R) Boot Agent GE v1.2.42
Copyright (C) 1997-2006, Intel Corporation
Intel(R) Boot Agent PXE Base Code (PXE-2.1 build 085)
Copyright (C) 1997-2006, Intel Corporation
CLIENT MAC ADDR: 00 1E 68 57 51 4A GUID: 080020FF FFFF FFFF FFFF 001E685714A
CLIENT IP: 10.79.200.235 MASK: 255.255.255.192 DHCP IP: 10.79.200.222
GATEWAY IP: 10.79.200.193
TFTP.
PXE-T02: Access violation
PXE-E3C: TFTP Error - Access Violation
- A. Contact the secondary tftp server.
- B. Load the pxegrub file.
- C. Abandon network boot and hang.
- D. Boot the internal raid device.
- E. Boot the CDROM.
Answer:
C
Explanation:
TFTP Error or System Hangs After GATEWAY Message
The DHCP server provides an IP address and a location of the initial boot program as part of the
DHCP response.
If the boot program does not exist, then the AI client boot cannot proceed. The following message is
displayed:
Intel(R) Boot Agent PXE Base Code (PXE-2.1 build 0.86)
Copyright(C) 1997-2007, Intel Corporation
CLIENT MAC ADDR 00 14 4F 29 04 12 GUID FF2000008 FFFF FFFF FFFF 7BDA264F1400
CLIENT IP: 10.6.68.29 MASK: 255.255.255.0 DHCP IP: 10.6.68.49
GATEWAY: 10.6.68.1
TFTP.
PXE-T02: Access Violation
PXE-E3C: TFTP Error - Access violation
PXE-MOF: Exiting Intel Boot Agent
Reference: Oracle Solaris 11 Express, Client Installation Fails
Question 7
Which two statements about flows are true?
- A. A flow must have a bandwidth limit defined in order to be observed.
- B. A flow can use NIC hardware resources when supported and available.
- C. A flow can only be set within the global zones yet can be observed within a non-global zone.
- D. A flow can be defined with local and remote port combination.
- E. A flowstat allows collection of only receive-side statistics.
Answer:
B, C
Explanation:
B: Example: Creating a Policy Around a Mission-Critical Port
The command below creates a policy around inbound HTTPS traffic on an HTTPS server so that HTTPS
obtains dedicated NIC hardware and kernel TCP/IP resources. The name specified, https-1, can be
used later to modify or delete the policy.
# flowadm add-flow -l bge0 -a transport=TCP,local_port=443 https-1
# flowadm show-flow -l bge0
FLOW
LINK
IP ADDR
PROTO PORT RPORT DSFLD
https1
bge0
--
tcp 443 -- --
C:
Note:
* Flow Restrictions Per Zone
Within a zone, no two flows can have the same name. After adding a flow with the link specified, the
link will not be required for display, modification, or deletion of the flow.
Incorrect:
Not A: Flow Properties
The following flow properties are supported. Note that the ability to set a given property to a given
value depends on the driver and hardware.
maxbw
Sets the full duplex bandwidth for the flow. The bandwidth is specified as an integer with one of the
scale suffixes(K, M, or G for Kbps, Mbps, and Gbps). If no units are specified, the input value will be
read as Mbps. The default is no bandwidth limit.
priority
Sets the relative priority for the flow. The value can be given as one of the tokens high, medium, or
low. The default is medium.
Not D: The following types of combinations of attributes are supported:
local_ip[/prefixlen]=address
remote_ip[/prefixlen]=address
transport={tcp|udp|sctp|icmp|icmpv6}
transport={tcp|udp|sctp},local_port=port
transport={tcp|udp|sctp},remote_port=port
dsfield=val[:dsfield_mask]
On a given link, the combinations above are mutually exclusive. An attempt to create flows of
different combinations will fail.
Note: Flow Attributes
The flow operand that identify a flow in a flowadm command is a comma-separated list of one or
more keyword, value pairs from the list below.
local_ip[/prefix_len]
remote_ip[/prefix_len]
transport={tcp|udp|sctp|icmp|icmpv6}
local_port
Identifies a service specified by the local port.
remote_port
Identifies a service specified by the remote port.
dsfield[:dsfield_mask]
Not E:
* flowstat
- report flow statistics
* The flowstat command reports run time statistics about user defined flows. flowadm show-flow
provides the flow name information for this command.
* flowstat [-r | -t] [-i interval] [-l link] [flow]
This form of the command iteratively examines all flows and reports statistics. The output is sorted in
descending order of flow utilization. If no flow is specified, the system displays statistics for all flows.
-r
Display receive-side statistics only. Includes bytes and packets received, drops, and so forth.
-t
Display transmit-side statistics only. Includes bytes and packets sent, drops, and so forth.
-i interval
Specify an interval in seconds at which statistics are refreshed. The default interval is one second.
-l link | flow]
Display statistics for all flows on the specified link or statistics for the specified flow.
Reference: man flowadm, man flowstat
Question 8
Which term describes a read-only copy of a file system or volume, which can be created quickly
easily, and initially consumes no additional Space within the pool?
- A. vdev
- B. dataset
- C. snapshot
- D. clone
- E. pool
Answer:
C
Explanation:
A snapshot is a read-only point-in-time copy of a file system. The copy-on-write design
of ZFS makes them essentially free - They are space efficient and instantaneous, providing an
invaluable part of backup strategies and synchronizing data between systems.
Incorrect:
Incorrect:
Not A: A ZFS vdev (aka "virtual device") is either:
a single disk, or
two or more disks that are mirrored, or
a group of disks that are organized using RAID-Z.
There are also special kinds of vdevs like hot-spares, ZIL or cache devices, etc.
Not D:
Clones are writeable snapshots, ideal for storing many private
copies of shared data for operations such as data migration, test
and development, or backup.
Question 9
Which three options are features of the Oracle Solaris 11 Automated Installer?
- A. direct reuse of Jumpstart profiles and rules
- B. Solaris 11 Zones provisioning
- C. Solaris 10 branded (BrandZ) Zone provisioning
- D. directly bootable installation images
- E. Image Packaging System (IPS) integration
Answer:
B, D, E
Explanation:
Note:
Not A:
* Jumpstart Profiles and Rules would have to be converted to be used in Automated Installer.
Use the js2ai utility with the -r option to convert both JumpStart rules and their associated profiles to
AI criteria and manifests.
* Both Solaris Custom JumpStart and Oracle Solaris Automated Installer (AI) provide hands-free
installation of multiple systems on a network. Clients are booted over the network, and once the
client is booted, the installer takes over.
Question 10
You are working on a system that appears to be hanging during the boot process. Which would be
the course of action for determining which step in the boot process is causing the issue?
- A. Boot the system into single user mode, run ps -ef to determine processes that are not running.
- B. Boot the system into the "none" milestone, enable all services, then run svcs -a to determine the state of your services, as well as check for error messages in /var/svc/log.
- C. Boot the system, disable all services using the "svcs disable all" command, reboot and bring up each service individually.
- D. Interrupt the boot process before services are started with Stop-A or <CTRL><ALT><DELETE>.
- E. Perform an Interactive boot, and disable services as they request startup.
Answer:
B
Explanation:
* Booting a system using the none milestone can be very useful for debugging startup problems.
There is no equivalent run level to the none milestone.
* If problems with starting services occur, sometimes a system will hang during the boot. This
procedure shows how to troubleshoot this problem.
2. Boot without starting any services.
This command instructs the svc.startd daemon to temporarily disable all services and start sulogin on
the console.
ok boot -m milestone=none
2. Log in to the system as root.
3. Enable all services.
# svcadm milestone all
4. Determine where the boot process is hanging.
When the boot process hangs, determine which services are not running by running svcs -a. Look for
error messages in the log files in /var/svc/log.
1. After fixing the problems, verify that all services have started.
Verify that all needed services are online.
# svcs -x
Verify that the console-login service dependencies are satisfied.
This command verifies that the login process on the console will run.
# svcs -l system/console-login:default
6.Continue the normal booting process.
Reference: How to Boot Without Starting Any Services
Question 11
After installing an Oracle Solaris 11 system, you execute the following command to create a data set
into which several non-global zones will be installed: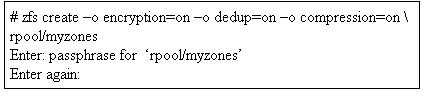
What impact will this command have on any zones installed under this ZFS data set?
- A. The zones will have encrypted swap and /tmp file systems.
- B. The zones will not permit any move or clone operations.
- C. The zones will be required to be "Solaris" brands only.
- D. The zones will cache the encryption key while running.
- E. The zones will be unable to start during system boot.
Answer:
E
Explanation:
Note:
* Oracle Solaris 11 adds transparent data encryption functionality to ZFS. All data and file system
metadata (such as ownership, access control lists, quota information, and so on) are encrypted when
stored persistently in the ZFS pool.
* A ZFS pool can support a mix of encrypted and unencrypted ZFS data sets (file systems and ZVOLs).
Data encryption is completely transparent to applications and other Oracle Solaris file services, such
as NFS or CIFS. Since encryption is a first-class feature of ZFS, we are able to support compression,
encryption, and deduplication together. Encryption key management for encrypted data sets can be
delegated to users, Oracle Solaris Zones, or both. Oracle Solaris with ZFS encryption provides a very
flexible system for securing data at rest, and it doesn't require any application changes or
qualification.
ZFS makes it easy to encrypt data and manage data encryption. You can have both encrypted and
unencrypted file systems in the same storage pool. You can also use different encryption keys for
different systems, and you can manage encryption either locally or remotely.
Reference: How to Manage ZFS Data Encryption
Question 12
The dladm command manages these:
- A. NICs
- B. VNICs
- C. VLANs
- D. Bridges
- E. Routers
Answer:
B, C, D
Explanation:
* vnic-link
A virtual network interface created on a link or an etherstub. It is a pseudo device that can be treated
as if it were an network interface card on a machine.
* vlan-link
A VLAN datalink.
* bridge
A bridge instance, identified by an administratively-chosen name. The name may use any
alphanumeric characters or the underscore, _, but must start and end with an alphabetic character. A
bridge name can be at most 31 characters. The name default is reserved, as are all names starting
with SUNW.
Note:
* dladm administer data links
* The dladm command is used to administer data-links. A data-link is represented in the system as a
STREAMS DLPI (v2) interface which can be plumbed under protocol stacks such as TCP/IP. Each data-
link relies on either a single network device or an aggregation of devices to send packets to or
receive packets from a network.
Each dladm subcommand operates on one of the following objects:
link
A datalink, identified by a name. In general, the name can use any alphanumeric characters (or the
underscore, _), but must start with an alphabetic character and end with a number. A datalink name
can be at most 31 characters, and the ending number must be between 0 and 4294967294
(inclusive). The ending number must not begin with a zero. Datalink names between 3 and 8
characters are recommended.
Some subcommands operate only on certain types or classes of datalinks. For those cases, the
following object names are used:
phys-link
A physical datalink.
vlan-link
A VLAN datalink.
aggr-link
An aggregation datalink (or a key; see NOTES).
ether-link
A physical Ethernet datalink.
wifi-link
A WiFi datalink.
vnic-link
A virtual network interface created on a link or an etherstub. It is a pseudo device that can be treated
as if it were an network interface card on a machine.
iptun-link
An IP tunnel link.
dev
A network device, identified by concatenation of a driver name and an instance number.
etherstub
An Ethernet stub can be used instead of a physical NIC to create VNICs. VNICs created on an
etherstub will appear to be connected through a virtual switch, allowing complete virtual networks
to be built without physical hardware.
bridge
A bridge instance, identified by an administratively-chosen name. The name may use any
alphanumeric characters or the underscore, _, but must start and end with an alphabetic character. A
bridge name can be at most 31 characters. The name default is reserved, as are all names starting
with SUNW.
Note that appending a zero (0) to a bridge name produces a valid link name, used for observability.
secobj
A secure object, identified by an administratively-chosen name. The name can use any alphanumeric
characters, as well as underscore (_), period (.), and hyphen (-). A secure object name can be at most
32 characters.
Question 13
When upgrading to Oracle Solaris 11 from Oracle Solaris 11 Express or Oracle Solaris 11 Early
Adopter, the progress suddenly fails. Which command can you rely upon to get you to a good known
state where you can still boot the Oracle Solaris 11 Express or Oracle Snarls 11 Early Adopter images,
as they were, prior to your upgrade attempt?
- A. pkg
- B. beadm
- C. installadm
- D. zfs
- E. ifconfig
Answer:
B
Explanation:
If an error occurs when booting the new BE, activate and boot to the previous BE.
Example:
# beadm activate solaris
# init 6
Question 14
The beadm utility ______.
- A. can create and manage both UFS and ZFS boot environments
- B. cannot manage boot environment snapshots
- C. can be used only on Solaris 11 for x86 systems that use GRUB
- D. can manage boot environments in non-global zones
- E. cannot create a new boot environment from an inactive boot environment
Answer:
B
Explanation:
You can use the beadm utility to create and manage snapshots and clones of your boot
environments.
Note: The following distinctions relevant to boot environment administration:
A snapshot is a read-only image of a dataset or boot environment at a given point in time. A
snapshot is not bootable.
A boot environment is a bootable Oracle Solaris environment, consisting of a root dataset and,
optionally, other datasets mounted underneath it. Exactly one boot environment can be active at a
time.
A clone of a boot environment is created by copying another boot environment. A clone is bootable.
Reference: Managing Boot Environments With Oracle Solaris 11 Express, Using beadm Utility
Question 15
When troubleshooting the client boot process, you notice the following scenario:
What is the most likely reason for this?
- A. This error could occur if another DHCP server is responding to the client.
- B. This error could occur if the switch has auto-negotiation disabled.
- C. This error could occur when you try to use a x86 Automated Installer server to boot a SPARC client.
- D. There is an HTTP version mismatch.
- E. This cannot occur if there is no DHCP server configured yet, so you need to configure one first.
Answer:
A
Explanation:
Boot Load Failed
If the AI client starts downloading the boot_archive, but then fails with the error, Boot load failed,
that indicates that the client DHCP information is configured incorrectly.
Rebooting with command: boot net:dhcp - install
Boot device: /pci@7c0/pci@0/network@4:dhcp File and args:
1000 Mbps FDX Link up
HTTP: Bad Response: 500 Internal Server Error
Evaluating:
Boot load failed
This error could happen if another DHCP server is responding to the client. Check the DHCP
configuration for this client. If the configuration appears to be correct, determine whether there is
another DHCP server in the subnet.
Reference: Installing Oracle Solaris 11 Systems, Boot Load Failed