Ensuring least-privileged access to cloud resources and infrastructure
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
A
DRAG DROP
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Select and Place: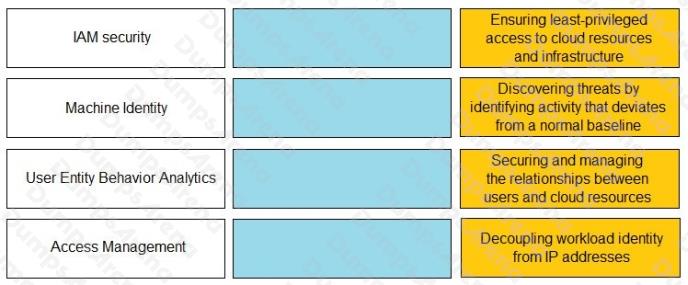
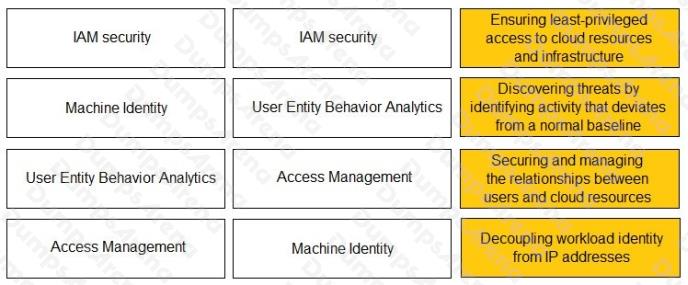
Ensuring least-privileged access to cloud resources and infrastructure
Thanks for submitting , your comment will be approved soon by our moderators
In the attached network diagram, which device is the switch?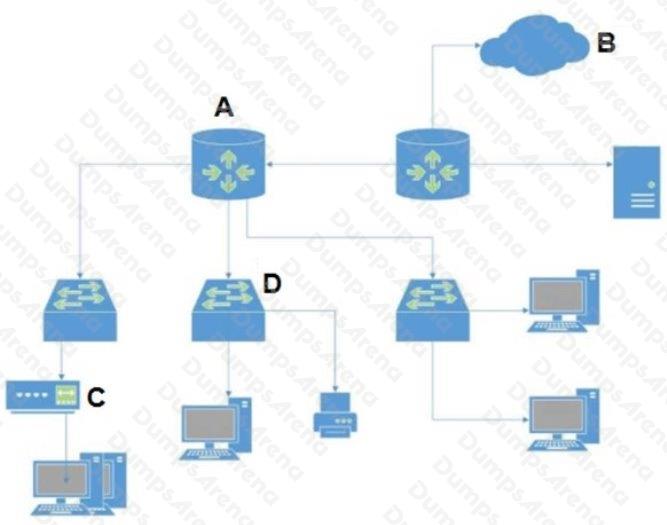
D
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost
and is infinitely scalable?
C
Which activities do local organization security policies cover for a SaaS application?
B
Which endpoint product from Palo Alto Networks can help with SOC visibility?
B
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up
IoC investigations?
C
Which statement describes DevOps?
B
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack
context needed to accelerate analysis, forensics, and hunting workflows?
C
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
D
Which subnet does the host 192.168.19.36/27 belong?
D
Which IoT connectivity technology is provided by satellites?
C
Which term describes data packets that move in and out of the virtualized environment from the host network or a
corresponding traditional data center?
A
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose
three.)
C D E
Why is it important to protect East-West traffic within a private cloud?
A