The correct answer should be color and not priority.
What is the default action for the SYN Flood option within the DoS Protection profile?
d
What is the minimum frequency for which you can configure the firewall to check for new WildFire antivirus signatures?
d
Reference:
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-new-features/wildfire-features/five-minute-wildfire-updates
Which setting is available to edit when a tag is created on the local firewall?
d
The correct answer should be color and not priority.
What can be achieved by selecting a policy target prior to pushing policy rules from Panorama? *
a
The target allows you to select a device that the policy will be pushed to
I had 5-day training course, but there's nothing about Panorama management. How could this exam have such a question?
You receive notification about new malware that is being used to attack hosts. The malware exploits a software bug in common application.
Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database?
b
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control (RBAC)? (Choose two.)
ab
Reference:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-firewall-administrators/administrative-authentication.html
Assume a custom URL Category Object of `NO-FILES` has been created to identify a specific website.
How can file uploading/downloading be restricted for the website while permitting general browsing access to that website?
b
Reference:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/set-up-file-blocking
What do application filters help provide access to?
b
Which Security policy action will message a user's browser that their web session has been terminated?
d
Given the image, which two options are true about the Security policy rules. (Choose two.)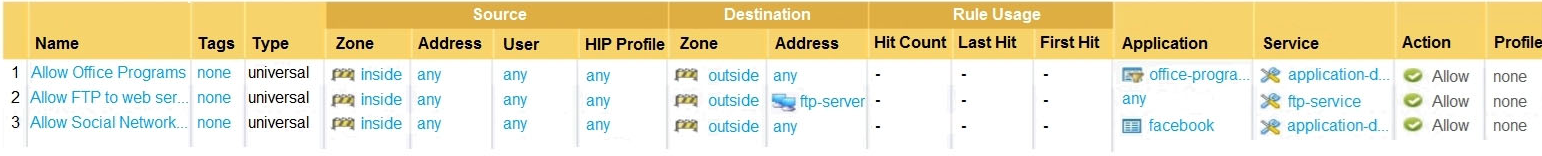
bc
office programs are using an application filter not a group. no app-id can be seen to be used so answer has to be A and D