palo alto networks pcnse practice test
Palo Alto Networks Certified Network Security Engineer
Last exam update: Apr 14 ,2025
Question 1
Which of the following commands would you use to check the total number of the sessions that are currently going through SSL Decryption processing?
- A. show session all filter ssl-decryption yes total-count yes
- B. show session all ssl-decrypt yes count yes
- C. show session all filter ssl-decrypt yes count yes
- D. show session filter ssl-decryption yes total-count yes
Answer:
c
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClF2CAK
Question 2
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users.
What should the administrator be aware of regarding the authentication sequence, based on the Authentication profiles in the order Kerberos, LDAP, and TACACS+?
- A. The priority assigned to the Authentication profile defines the order of the sequence.
- B. The firewall evaluates the profiles in the alphabetical order the Authentication profiles have been named until one profile successfully authenticates the user.
- C. If the authentication times out for the first Authentication profile in the authentication sequence, no further authentication attempts will be made.
- D. The firewall evaluates the profiles in top-to-bottom order until one Authentication profile successfully authenticates the user.
Answer:
c
Question 3
In an existing deployment, an administrator with numerous firewalls and Panorama does not see any WildFire logs in Panorama. Each firewall has an active WildFire subscription. On each firewall, WildFire logs are available.
This issue is occurring because forwarding of which type of logs from the firewalls to Panorama is missing?
- A. System logs
- B. WildFire logs
- C. Threat logs
- D. Traffic logs
Answer:
a
Question 4
An administrator needs firewall access on a trusted interface. Which two components are required to configure certificate-based, secure authentication to the web
UI? (Choose two.)
- A. server certificate
- B. SSL/TLS Service Profile
- C. certificate profile
- D. SSH Service Profile
Answer:
bc
Question 5
What is the best description of the HA4 Keep-alive Threshold (ms)?
- A. the timeframe that the local firewall waits before going to Active state when another cluster member is preventing the cluster from fully synchronizing
- B. the timeframe within which the firewall must receive keepalives from a cluster member to know that the cluster member is functional
- C. the maximum interval between hello packets that are sent to verify that the HA functionality on the other firewall is operational
- D. the time that a passive or active-secondary firewall will wait before taking over as the active or active-primary firewall
Answer:
b
Question 6
Which three options are supported in HA Lite? (Choose three.)
- A. Virtual link
- B. Active/passive deployment
- C. Synchronization of IPsec security associations
- D. Configuration synchronization
- E. Session synchronization
Answer:
bcd
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-high-availability/ha-lite
Question 7
If an administrator wants to decrypt SMTP traffic and possesses the server's certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
- A. TLS Bidirectional Inspection
- B. SSL Inbound Inspection
- C. SSH Forward Proxy
- D. SMTP Inbound Decryption
Answer:
b
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/decryption/configure-ssl-inbound-inspection
Question 8
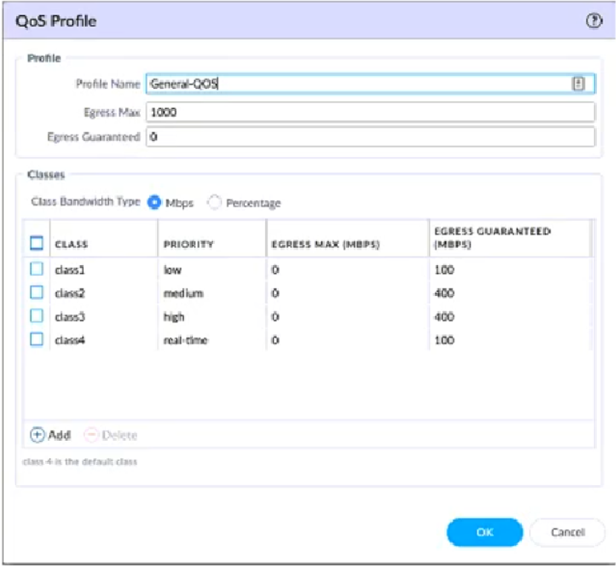
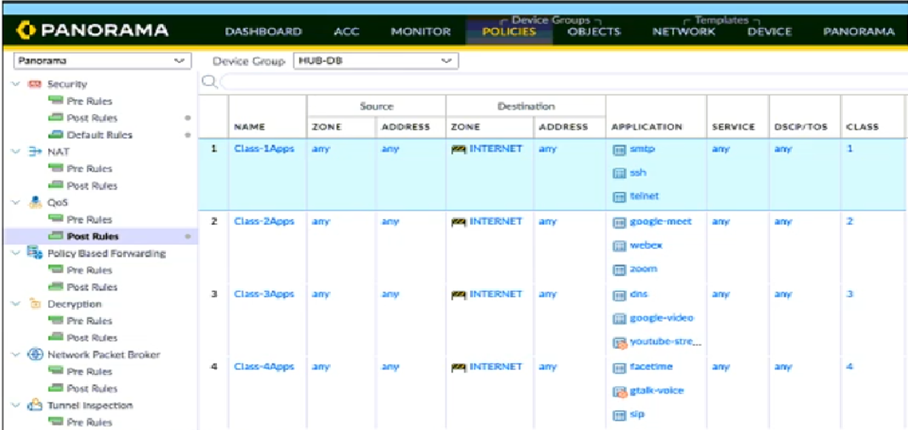
View the screenshots. A QoS profile and policy rules are configured as shown.
Based on this information, which two statements are correct? (Choose two.)
- A. SMTP has a higher priority but lower bandwidth than Zoom.
- B. Facetime has a higher priority but lower bandwidth than Zoom.
- C. google-video has a higher priority and more bandwidth than WebEx.
- D. DNS has a higher priority and more bandwidth than SSH.
Answer:
bd
Question 9
An administrator just submitted a newly found piece of spyware for WildFire analysis. The spyware passively monitors behavior without the user's knowledge.
What is the expected verdict from WildFire?
- A. Malware
- B. Grayware
- C. Phishing
- D. Spyware
Answer:
b
Question 10
What is the best description of the Cluster Synchronization Timeout (min)?
- A. The maximum interval between hello packets that are sent to verify that the HA functionality on the other firewall is operational
- B. The maximum time that the local firewall waits before going to Active state when another cluster member is preventing the cluster from fully synchronizing
- C. The timeframe within which the firewall must receive keepalives from a cluster member to know that the cluster member is functional
- D. The time that a passive or active-secondary firewall will wait before taking over as the active or active-primary firewall
Answer:
b